Market Overview
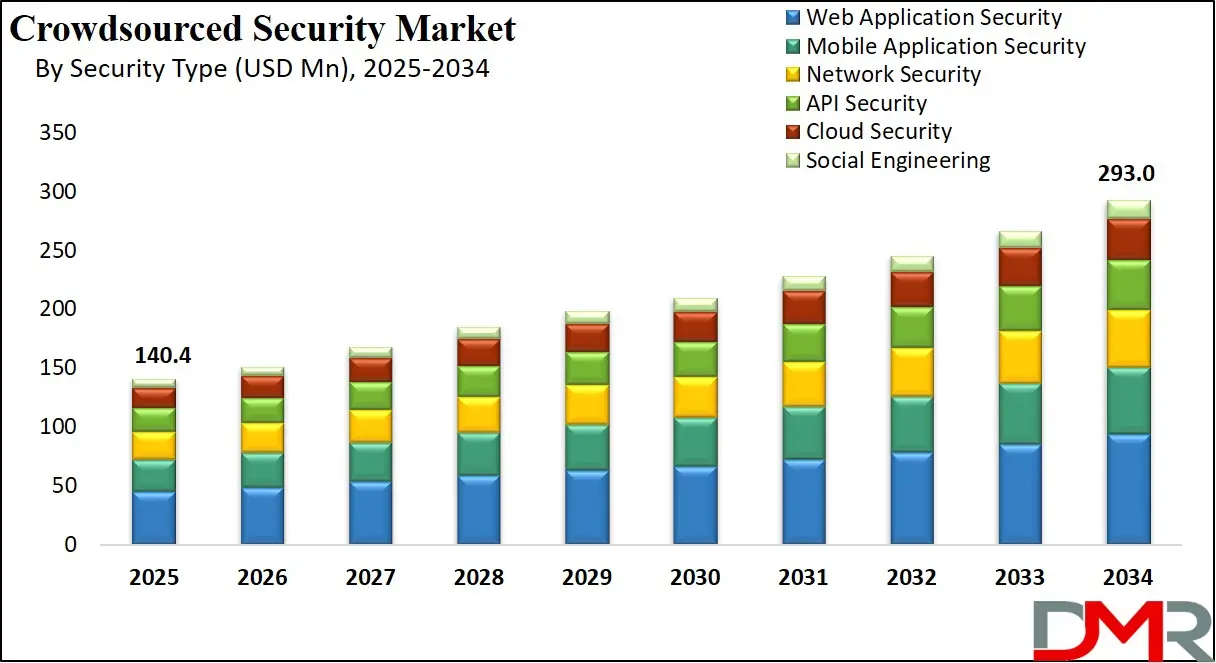
The Global Crowdsourced Security Market size is projected to reach USD 140.4 million in 2025 and grow at a compound annual growth rate of 8.5% from there until 2034 to reach a value of USD 293.0 million.
Crowdsourced security is a modern approach to protecting digital systems, applications, and data by involving a large group of independent security researchers or ethical hackers. These researchers test systems for vulnerabilities, report issues, and sometimes help fix them. Instead of relying only on in-house security teams, companies invite external experts to find flaws. This open model helps organizations discover hidden weaknesses more quickly and thoroughly than traditional methods.

In recent years, demand for crowdsourced security has grown because of the rising number of cyberattacks and data breaches. As digital transformation accelerates, companies are launching more applications, websites, and services, rise in the number of potential entry points for attackers. Many organizations find it difficult to keep up with the speed and complexity of modern threats. Crowdsourced security offers access to a broader talent pool and often uncovers critical vulnerabilities that automated tools or internal teams may miss.
Trends in the industry include the rise of bug bounty programs, where companies reward researchers for reporting valid security flaws. These programs are now widely used by technology companies, financial services, and even government agencies. Some platforms also offer vulnerability disclosure programs, where researchers can report issues ethically without receiving payment but still help improve security. Another growing trend is penetration testing as a service (PTaaS), where crowdsourced experts simulate real-world attacks to test defenses.
Several important events have highlighted the value of crowdsourced security. Major companies have prevented breaches by fixing bugs reported through bug bounty platforms. Governments have also turned to ethical hackers to secure their systems. Over time, what was once considered a risky or informal approach has gained respect and trust in the broader cybersecurity industry.
Key insights include the important role of platforms that connect researchers with organizations in a structured, secure, and legal way. These platforms manage researcher identities, track submissions, and ensure responsible disclosure. This has made crowdsourced security more scalable and easier to manage for companies of all sizes. Another insight is that diversity among researchers helps uncover a wider range of vulnerabilities, as different people think in different ways.
The US Crowdsourced Security Market
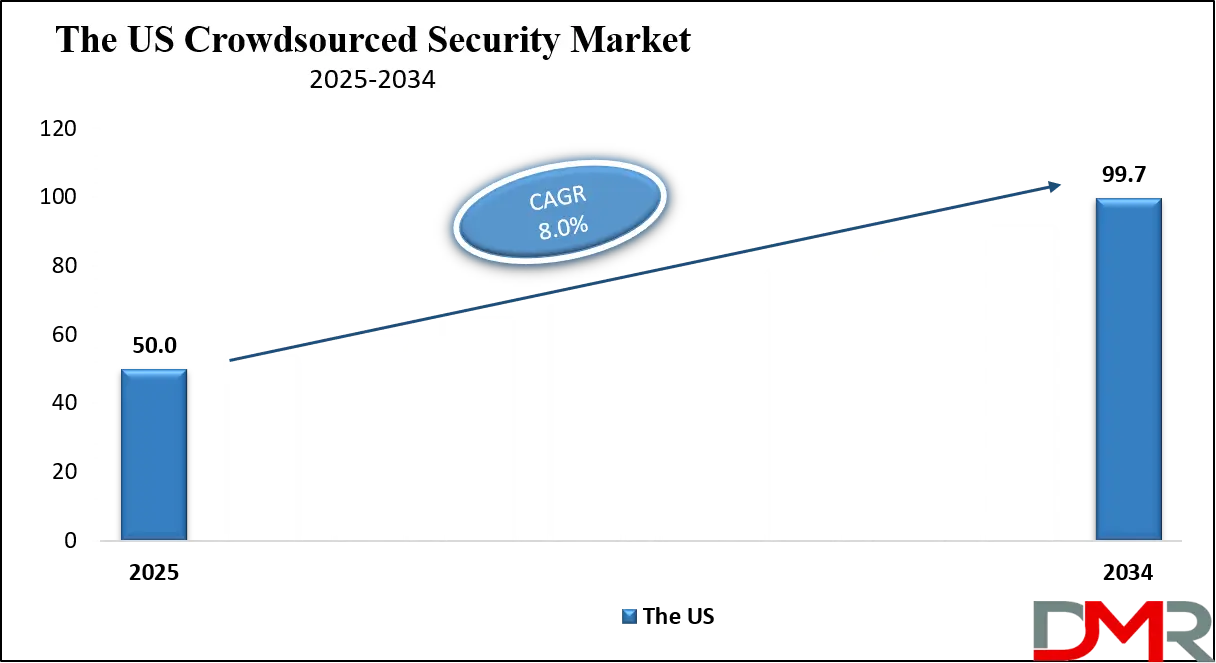
The US Crowdsourced Security Market size is projected to reach USD 50.0 million in 2025 at a compound annual growth rate of 8.0% over its forecast period.
The US plays a leading role in the crowdsourced security market due to its strong technological infrastructure, advanced cybersecurity ecosystem, and early adoption of ethical hacking practices. Many of the world’s largest tech companies and security platforms are based in the US, helping to set global standards for bug bounty and vulnerability disclosure programs.
The US government and defense sectors have also embraced crowdsourced security through structured initiatives, encouraging ethical hacking to protect public systems. Strong legal frameworks and data protection policies further support the safe execution of these programs. Additionally, the US has a large pool of skilled cybersecurity professionals and researchers who actively contribute to global platforms, making it a key driver of growth and innovation in this market.
Europe Crowdsourced Security Market
Europe Crowdsourced Security Market size is projected to reach USD 39.0 million in 2025 at a compound annual growth rate of 8.4% over its forecast period.
Europe plays a growing and influential role in the crowdsourced security market, driven by increasing digitalization, strict data protection regulations, and rising cybersecurity concerns. The General Data Protection Regulation (GDPR) has encouraged organizations to take proactive steps toward securing personal and business data, including the use of ethical hacking and vulnerability disclosure programs.
Many European companies, including those in finance, healthcare, and government, are adopting crowdsourced security models to meet compliance and reduce risk. Europe is also home to a growing number of skilled ethical hackers and research communities contributing to global platforms.
Additionally, regional governments are supporting cybersecurity innovation, further boosting the adoption of collaborative security approaches. As trust in external testing grows, Europe's role in shaping secure digital ecosystems continues to strengthen.
Japan Crowdsourced Security Market
Japan Crowdsourced Security Market size is projected to reach USD 7.0 million in 2025 at a compound annual growth rate of 8.6% over its forecast period.
Japan is gradually strengthening its role in the crowdsourced security market as awareness of cyber threats increases across public and private sectors. Traditionally reliant on internal security teams, Japanese organizations are now beginning to explore external ethical hacking to enhance their cybersecurity posture. Industries like finance, manufacturing, and technology are showing interest in structured vulnerability disclosure and bug bounty programs.
The Japanese government is also encouraging more open security practices, especially in critical infrastructure and smart city initiatives. While cultural preferences for privacy and caution have slowed adoption, trust in managed platforms is growing. Local security communities are emerging, contributing to regional platforms and collaborating with global ecosystems. As digital transformation advances, Japan’s involvement in crowdsourced security is expected to deepen steadily.
Crowdsourced Security Market: Key Takeaways
- Market Growth: The Crowdsourced Security Market size is expected to grow by USD 141.9 million, at a CAGR of 8.5%, during the forecasted period of 2026 to 2034.
- By Security Type: The web application security segment is anticipated to get the majority share of the Crowdsourced Security Market in 2025.
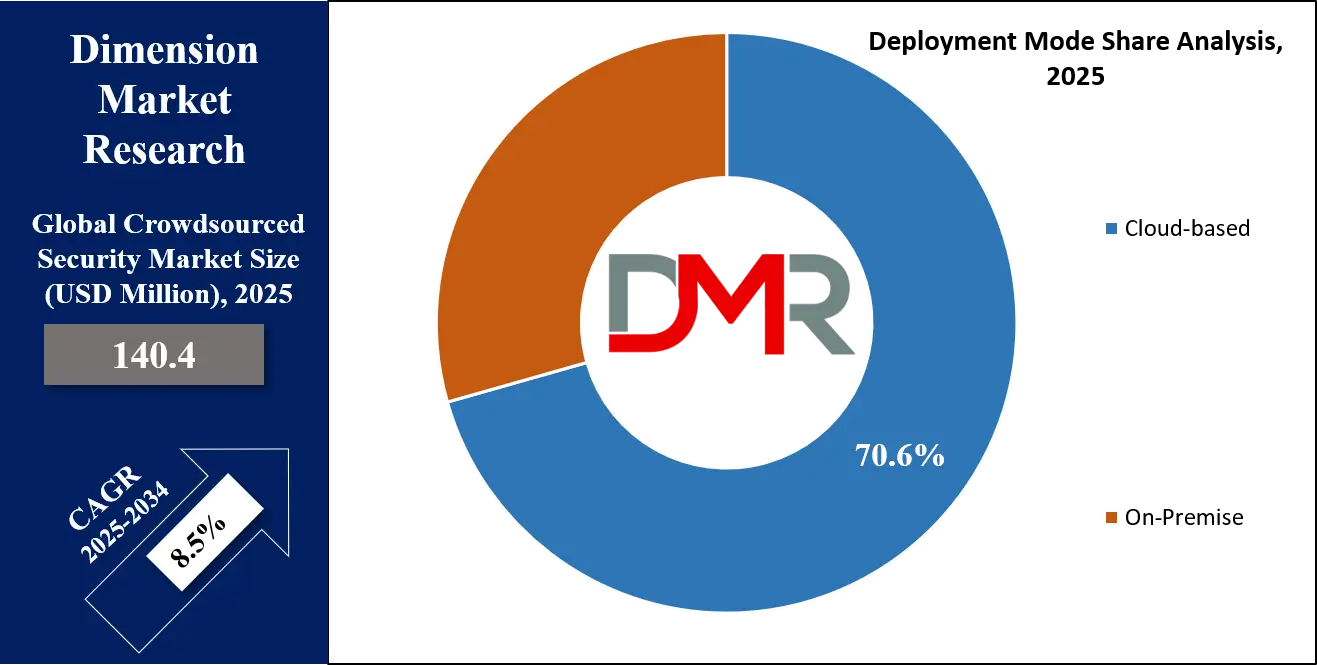
- By Deployment Mode: The Cloud-based segment is expected to get the largest revenue share in 2025 in the Crowdsourced Security Market.
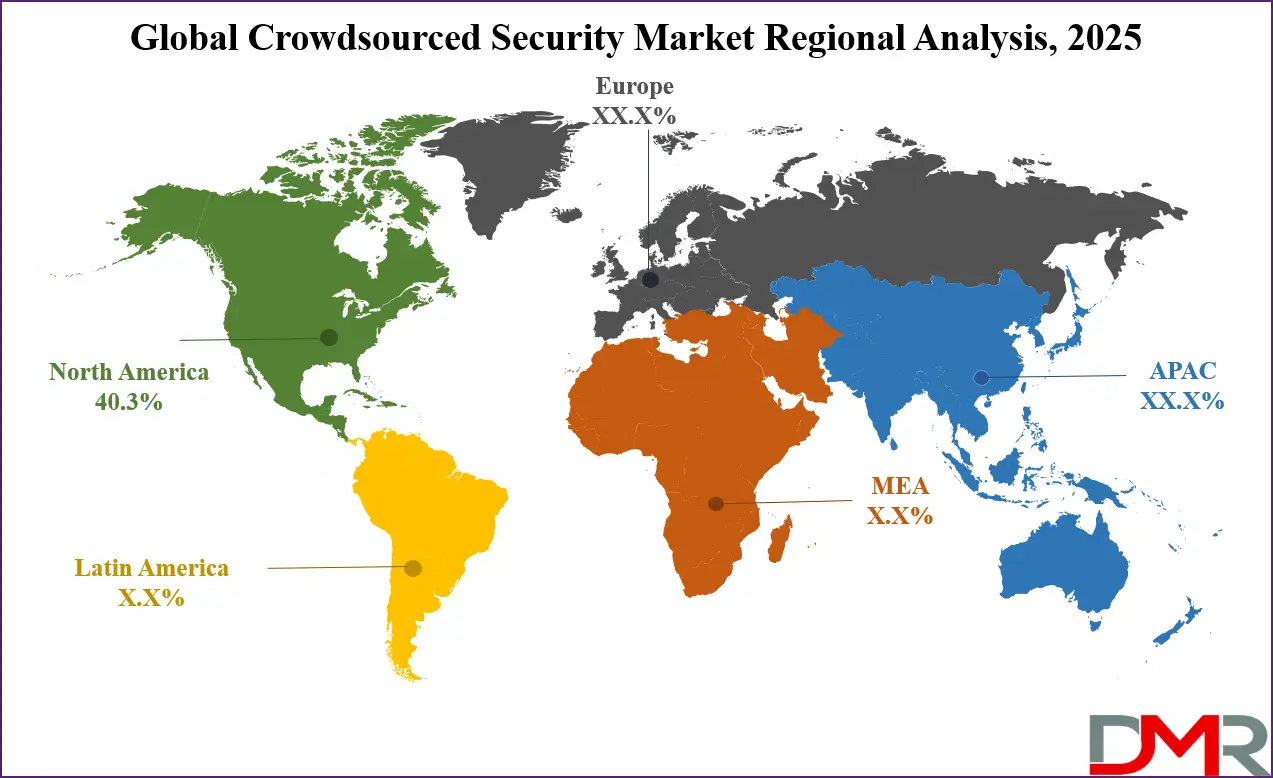
- Regional Insight: North America is expected to hold a 40.3% share of revenue in the Global Crowdsourced Security Market in 2025.
- Use Cases: Some of the use cases of Crowdsourced Security include mobile app security, web application testing, and more.
Crowdsourced Security Market: Use Cases
- Web Application Testing: Crowdsourced security helps uncover hidden vulnerabilities in websites and web apps by using a diverse group of ethical hackers. These researchers test different access points, input fields, and user flows to detect issues missed by automated tools. It improves overall security before a product goes live.
- Mobile App Security: Organizations use crowdsourced experts to test mobile apps across different devices, operating systems, and network conditions. This helps identify flaws like insecure data storage, improper permissions, or weaknesses in app logic. It ensures a safer experience for users and protects sensitive data.
- Cloud Infrastructure Assessment: With the rise of cloud services, companies invite researchers to test the security of their cloud-based platforms. Crowdsourced testing helps detect misconfigurations, access control issues, and other gaps in cloud infrastructure that could lead to data breaches.
- API and Backend Testing: APIs are critical to many applications but often have security gaps that can be exploited. Crowdsourced testing involves checking how APIs handle data, authorization, and input validation. This helps companies fix issues before attackers can exploit them, ensuring safer integration and data sharing.
Stats & Facts
- As per Intigriti
- 18% of all reported vulnerabilities were caused by cross-site scripting (XSS), which lets attackers inject malicious scripts into web applications and compromise user data or sessions.
- 16% of vulnerabilities involved information disclosure, where sensitive internal or user data was exposed due to insecure application behavior or flawed access controls.
- 14% of the identified security flaws were a result of security misconfigurations, often due to incorrect default settings, unnecessary features left enabled, or weak permissions that attackers could exploit.
- According to Sonatype
- 80% of application dependencies go unpatched for more than a year, even though 95% of these outdated versions have safer alternatives ready to use, indicating that many security risks are avoidable with basic update practices.
- Only 0.5% of open-source software components have no safer update path available (No Path Forward), suggesting that nearly every risk from outdated components can be fixed if addressed.
- Even when updates are applied, 3.6% of dependencies remain vulnerable because teams unknowingly replace outdated components with newer but still insecure versions, perpetuating the risk.
- In a study of over 20,000 enterprise applications, it was found that many relied heavily on EOL (end-of-life) components, which no longer receive updates or patches, leading to a slow but steady decline in software integrity and increased vulnerability exposure.
- Out of more than seven million open-source components available, only around 10.5%—approximately 762,000—are actively used in real-world applications, showing how developers often face a confusing overload of component choices, increasing the risk of poor security decisions.
- Developers are frequently exposed to unnecessary complexity when selecting dependencies, with Sonatype noting that the large volume of unused components contributes to confusion and heightens the likelihood of insecure or unmaintained software being included in applications.
- Many organizations fail to perform security reviews when updating components, sometimes replacing vulnerable software with different versions that are also exposed to known threats, instead of genuinely securing their systems.
Market Dynamic
Driving Factors in the Crowdsourced Security Market
Rising Cyber Threats and Security Complexity
As digital transformation accelerates, businesses are rapidly adopting cloud platforms, mobile applications, Internet of Things (IoT) devices, and online services. This rising digital footprint increases the number of potential entry points for cyberattacks. Traditional security teams often struggle to keep pace with the growing complexity and frequency of threats. Crowdsourced security offers a scalable and dynamic solution by bringing in skilled ethical hackers from across the globe.
These external experts help uncover hidden vulnerabilities that internal teams or automated tools might miss. This approach not only improves security coverage but also provides continuous threat monitoring. As cyberattacks become more sophisticated, organizations are seeking more proactive and diverse methods like crowdsourced testing to protect their digital assets. This demand is driving steady market growth.
Growing Adoption of Bug Bounty and Vulnerability Disclosure Programs
Organizations across industries are increasingly launching bug bounty and vulnerability disclosure programs to invite ethical hackers to identify and report security flaws. These programs have gained popularity because they provide access to a large pool of skilled security researchers at a fraction of the cost of full-time hires. The reward-based model is performance-driven, encouraging high-quality results.
Additionally, companies are recognizing the public trust and transparency benefits of disclosing how they handle vulnerabilities. Crowdsourced platforms are making it easier to manage submissions, track progress, and communicate with researchers. As more regulatory bodies and industry standards endorse responsible disclosure, adoption of these programs is expected to grow further. This shift toward openness and collaboration is a strong driver of market expansion.
Restraints in the Crowdsourced Security Market
Concerns Over Data Privacy and Confidentiality
One of the major restraints in the crowdsourced security market is the concern around sharing sensitive systems or data with external researchers. Organizations may hesitate to allow unknown individuals—even if they are ethical hackers—to access parts of their digital infrastructure.
There’s a fear that confidential information could be leaked or misused, especially if the scope of testing is not clearly defined or monitored. While platforms have policies and vetting processes in place, these concerns can slow down adoption, especially in sectors like finance, healthcare, or defense. The risk of exposure or unintentional data sharing limits the willingness of some companies to fully embrace crowdsourced security. Ensuring strict privacy and legal controls remains a key challenge.
Lack of Awareness and Misunderstanding of the Model
Despite its growing popularity, many organizations still do not fully understand how crowdsourced security works. There is a common misconception that inviting outsiders to test security is risky or unprofessional. Some decision-makers confuse ethical hacking with malicious activity, leading to resistance or fear of reputational damage.
Additionally, companies that are used to traditional security methods may find it hard to trust decentralized models. This lack of education about the process, benefits, and safety of managed crowdsourced testing limits its adoption. Without proper internal support and understanding, businesses may fail to take advantage of this effective security layer, thereby restraining market growth.
Opportunities in the Crowdsourced Security Market
Expansion into Emerging Markets and SMEs
There is a major opportunity for crowdsourced security providers to expand into emerging markets and among small to medium-sized enterprises (SMEs). Many of these businesses are becoming increasingly digital but lack the resources to maintain large, in-house security teams. Crowdsourced security offers a cost-effective and flexible solution that fits their budgets while still providing expert-level protection.
As awareness increases, more SMEs are likely to adopt bug bounty or vulnerability disclosure programs to secure their platforms. Emerging markets in Asia, Africa, and Latin America also present untapped potential due to the rise in internet usage and online services. Providers who localize their offerings and provide easy onboarding could capture significant growth in these regions.
Integration with AI and Automation Tools
The integration of crowdsourced security with artificial intelligence and automation presents a promising growth opportunity. AI can help prioritize vulnerability reports, detect patterns in hacker behavior, and streamline communication between researchers and organizations.
Automation tools can assist in managing submissions, validating findings, and tracking progress, making programs more efficient. By combining human creativity with machine intelligence, companies can scale their security testing without losing quality. This blend allows for faster response times and smarter analysis, which appeals to both large enterprises and fast-growing startups. As platforms adopt these technologies, their appeal and efficiency are expected to rise, opening new doors for market expansion.
Trends in the Crowdsourced Security Market
Remote & Distributed Testing
In recent times, crowdsourced security has shifted toward a fully remote model, where ethical hackers from different parts of the world can test systems anytime. This distributed testing setup means companies can keep their applications under constant review, without being limited by time zones or office hours. It also brings diverse perspectives, as testers with varied cultural, technical, and geographic backgrounds participate.
Companies are setting clear scopes and rules to manage remote engagement safely. With better coordination tools and secure testing environments, remote teams can quickly find and report vulnerabilities. This trend makes security testing more agile and responsive, fitting well with modern, always-on digital services.
Gamified Challenges & Skill-Based Tournaments
Another emerging trend is using gamified challenges and skill-based events to engage ethical hackers. Instead of traditional bounty payouts, some platforms host friendly contests where participants earn badges, rankings, or recognition alongside rewards. These competitions encourage experts to push their skills, explore new vulnerabilities, and stay updated with current threats.
They also help companies identify top talent for long-term partnerships. This game-like format builds a sense of community and excitement, making participation more fun and collaborative. It keeps researchers motivated and engaged, while organizations benefit from deeper and more creative security testing.
Research Scope and Analysis
By Security Type Analysis
Web application security will be leading the crowdsourced security market in 2025 with an estimated share of 31.7%, driven by the rising number of online platforms, mobile apps, and customer-facing services. As businesses continue to rely heavily on digital channels, protecting web applications from cyber threats has become a top priority. Crowdsourced security is proving highly effective in identifying hidden vulnerabilities, broken access controls, and injection flaws in real-time environments.
Ethical hackers test different user scenarios that automated tools often miss, helping businesses secure login systems, payment gateways, and user data. With the growing use of e-commerce, online banking, and SaaS solutions, the demand for constant web app testing is increasing. This focus on proactive security through global ethical hacker communities is making web application security a key driver in the expansion of the crowdsourced security market worldwide.
Cloud security, on the other hand, is expected to witness significant growth over the forecast period as more companies move their infrastructure and data to the cloud. This shift has introduced new challenges around access control, misconfigurations, and data privacy.
Crowdsourced security is becoming an essential tool for businesses to identify weaknesses across their cloud environments, from storage to containerized applications. With hybrid and multi-cloud models becoming common, ethical hackers provide valuable insights into potential gaps in real-world cloud deployments. Organizations are increasingly adopting bug bounty and penetration testing services focused specifically on cloud platforms to keep their systems safe. The rising dependence on cloud-native applications and services continues to boost the role of crowdsourced testing in cloud security.
By Deployment Mode Analysis
Cloud-based deployment is expected to lead the crowdsourced security market in 2025 with a projected share of 70.6%, driven by its scalability, flexibility, and ease of access. As organizations adopt cloud services to support remote work, digital platforms, and global operations, cloud-based security testing becomes more practical and efficient. This mode allows companies to quickly launch, manage, and scale bug bounty programs or vulnerability assessments without heavy infrastructure investments.
It also enables real-time collaboration with ethical hackers across different regions. With secure portals, automation, and integration with DevSecOps tools, cloud-based deployment enhances speed and visibility in security processes. Startups and large enterprises alike prefer this model to improve agility while keeping costs under control. The shift toward digital-first operations across industries is making cloud-based deployment a preferred choice for running crowdsourced security programs on a global scale.
On-premise deployment, while more traditional, is also expected to show significant growth over the forecast period as certain industries prioritize full control over their security environments. Sectors such as government, defense, and critical infrastructure prefer on-premise solutions due to strict data handling policies and regulatory demands. These organizations often deal with highly sensitive information and require complete control over how security testing is conducted and who accesses their systems.
On-premise deployment gives them greater customization, internal oversight, and the ability to run crowdsourced programs within their own secure networks. Although it requires higher setup and maintenance efforts, the added layer of control appeals to businesses with complex security needs. As awareness of ethical hacking grows, even security-conscious organizations are exploring how to integrate on-premise crowdsourced testing into their security operations.
By Organization Size Analysis
Large enterprises are projected to lead the crowdsourced security market in 2025 with a share of 62.3%, driven by their complex digital environments and growing need for continuous threat detection. These organizations often manage vast networks, multiple applications, and sensitive customer data, making them prime targets for cyberattacks. To stay ahead of evolving threats, large enterprises are adopting crowdsourced security models such as bug bounty programs and managed vulnerability disclosure systems.
They benefit from accessing a global pool of ethical hackers who can identify and report vulnerabilities at scale. With the resources to implement structured, multi-layered security strategies, these organizations are investing in flexible and scalable solutions. Crowdsourced testing complements their existing security infrastructure, helping them stay resilient. As digital operations expand across sectors like finance, tech, and healthcare, large enterprises continue to drive demand for collaborative, expert-driven cybersecurity models.
SMEs, although operating on smaller scales, are showing significant growth in adopting crowdsourced security over the forecast period. With limited internal security teams and rising exposure to cyber risks, small and medium-sized businesses are turning to ethical hackers to protect their digital systems. Crowdsourced platforms offer affordable, flexible testing options that allow SMEs to uncover vulnerabilities without heavy investments in full-time security personnel.
As digital tools, cloud services, and e-commerce platforms become central to SME operations, the need for dependable cybersecurity has increased. These businesses are beginning to recognize the value of continuous, real-world testing through crowdsourced models. Growing awareness, combined with the availability of user-friendly platforms, is making it easier for SMEs to join the global shift toward collaborative security practices.
By Industry Vertical Analysis
BFSI will be leading the crowdsourced security market in 2025 with a projected share of 23.7%, driven by its critical need for strong cybersecurity across banking, financial services, and insurance systems. This sector handles massive volumes of sensitive data, digital transactions, and customer records, making it a prime target for cyber threats. To stay secure and meet regulatory demands, BFSI organizations are turning to crowdsourced security solutions such as bug bounty programs and responsible vulnerability disclosure.
Ethical hackers help identify weak points in web apps, mobile platforms, payment gateways, and backend infrastructure. As digital banking, fintech, and online insurance services expand, the demand for real-time, expert-led security testing is rising. With increased digital adoption and the constant pressure to protect user trust and compliance, BFSI continues to play a leading role in driving the growth and innovation of crowdsourced security across industries.
Retail & E-commerce, fueled by rapid online growth, is showing significant momentum in adopting crowdsourced security over the forecast period. These businesses operate customer-facing websites, mobile apps, and digital payment systems that are frequently targeted by attackers. To protect customer data and maintain trust, retailers are increasingly using ethical hackers to test for vulnerabilities in login systems, shopping carts, and transaction processes.
The need for fast and secure digital experiences makes real-time testing through crowdsourced models an ideal fit. With seasonal sales, flash offers, and high user traffic, these platforms must remain secure under pressure. As more retail players shift to omnichannel and cross-border e-commerce, their dependence on scalable, affordable security solutions continues to grow—making this vertical a fast-growing contributor to the crowdsourced security market.
The Crowdsourced Security Market Report is segmented on the basis of the following:
By Security Type
- Web Application Security
- Mobile Application Security
- Network Security
- API Security
- Cloud Security
- Social Engineering
By Deployment Mode
By Organization Size
- Small and Medium Enterprises (SMEs)
- Large Enterprises
By Industry Vertical
- BFSI
- IT & Telecom
- Retail & E-commerce
- Healthcare
- Government
- Media & Entertainment
- Energy & Utilities
- Others
Regional Analysis
Leading Region in the Crowdsourced Security Market
North America will be leading the crowdsourced security market in 2025 with a share of 40.3%, driven by strong demand from industries like technology, finance, and government. The region has been quick to adopt bug bounty programs and vulnerability disclosure initiatives, supported by a mature cybersecurity culture and a large base of ethical hackers. With the growing complexity of cyber threats, organizations in North America are turning to crowdsourced security to strengthen their defenses and find hidden flaws faster.
Companies value the flexibility, speed, and broad expertise that this model offers. Government agencies and critical infrastructure providers are also encouraging ethical hacking to improve resilience. The presence of well-established platforms and innovation in security practices continues to support growth. As data protection becomes a bigger concern and regulations tighten, more businesses in North America are choosing crowdsourced testing over traditional methods.
Fastest Growing Region in the Crowdsourced Security Market
Asia Pacific is showing significant growth in the crowdsourced security market over the forecast period, driven by rising digital transformation, increasing cyber threats, and growing awareness of ethical hacking practices. Businesses in countries like India, China, Japan, and Australia are actively adopting vulnerability disclosure programs and bug bounty platforms to strengthen their cybersecurity posture.
The rapid expansion of e-commerce, fintech, and cloud services in the region is creating more demand for proactive security testing. Governments are also supporting cybersecurity initiatives, encouraging responsible disclosure and collaboration with ethical hackers. With more skilled researchers and improved infrastructure, Asia Pacific is becoming an important contributor to the global crowdsourced security landscape.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Competitive Landscape
The crowdsourced security market is becoming more competitive as more platforms and service providers enter the space. Companies are focusing on building strong communities of ethical hackers and offering flexible programs like bug bounties and vulnerability disclosure. The competition is not just about pricing but also about trust, speed of response, and quality of findings.
Players are improving their platforms to make it easier for both clients and researchers to collaborate securely. Some are adding new features like AI-powered analysis and real-time dashboards. There’s also growing specialization, with some focusing on specific industries or types of testing. As awareness of cybersecurity risks increases, the number of clients and researchers is growing, which is further fueling innovation and competition in this market.
Some of the prominent players in the global Crowdsourced Security are:
- HackerOne
- Bugcrowd
- Synack
- Cobalt
- YesWeHack
- Intigriti
- Bishop Fox
- Detectify
- SafeHats
- HackenProof
- Open Bug Bounty
- Security Discovery
- Shielder
- Secarma
- RedHunt Labs
- AppKnox
- CyberSecurityWorks (CSW)
- Hacken.io
- BugBase
- Hackrate
- Other Key Players
Recent Developments
- In July 2025, KnowBe4, focused on human risk management, launched the KnowBe4 Program Maturity Assessment (PMA), a free tool designed to help IT and security leaders evaluate and strengthen their organization’s security culture. Developed by security culture expert Perry Carpenter, the PMA offers a simple, self-guided framework that provides clear, actionable insights across ten key areas of human risk. Unlike technical or consultant-driven models, it simplifies complex cybersecurity topics into practical steps organizations of any size or industry can apply right away.
- In June 2025, Climb Channel Solutions expanded into a North American distribution agreement with Bugcrowd, a top provider of crowdsourced cybersecurity solutions. Through this partnership, Climb will offer Bugcrowd’s AI-powered platform to its network of over 7,000 resellers. Bugcrowd’s key services include penetration testing, vulnerability detection, attack surface management, and Red Team as a Service (RTaaS), which enhances Climb’s cybersecurity offerings and expands Bugcrowd’s reach, helping businesses tackle evolving security threats with proactive, researcher-driven protection tools.
- In April 2025, Bugcrowd launched the first-ever Red Team as a Service (RTaaS) offering powered by crowdsourcing. This service connects organizations with a global network of vetted ethical hackers for tailored red team engagements, fully managed through the Bugcrowd Platform. RTaaS allows businesses to simulate real-world attacks using the latest adversarial tactics, gaining deep insights into their security posture. Integrated with services like Pen Testing as a Service and Bug Bounty programs, RTaaS offers flexible, scalable solutions based on customer needs and maturity levels.
- In October 2024, Silicon Valley Bank (SVB), a division of First Citizens Bank, has extended a USD 50 million growth capital facility to Bugcrowd, a leader in crowdsourced cybersecurity solutions. The funding, offered through SVB’s Enterprise Software Group, will support the global expansion of Bugcrowd’s AI-driven platform, fuel continued innovation, and explore strategic mergers and acquisitions. This investment aims to enhance value for Bugcrowd’s clients, partners, and hacker community by strengthening its ability to identify and mitigate vulnerabilities across applications, systems, and infrastructure
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 140.4 Mn |
| Forecast Value (2034) |
USD 293.0 Mn |
| CAGR (2025–2034) |
8.5% |
| The US Market Size (2025) |
USD 50.0 Mn |
| Historical Data |
2019 – 2024 |
| Forecast Data |
2026 – 2034 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors, etc. |
| Segments Covered |
By Security Type (Web Application Security, Mobile Application Security, Network Security, API Security, Cloud Security, and Social Engineering), By Deployment Mode (Cloud-Based and On-Premise), By Organization Size (Small and Medium Enterprises (SMEs) and Large Enterprises), By Industry Vertical (BFSI, IT & Telecom, Retail & E-commerce, Healthcare, Government, Media & Entertainment, Energy & Utilities, and Others) |
| Regional Coverage |
North America – US, Canada; Europe – Germany, UK, France, Russia, Spain, Italy, Benelux, Nordic, Rest of Europe; Asia-Pacific – China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC; Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America; Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, Rest of MEA |
| Prominent Players |
HackerOne, Bugcrowd, Synack, Cobalt, YesWeHack, Intigriti, Bishop Fox, Detectify, SafeHats, HackenProof, Open Bug Bounty, Security Discovery, Shielder, Secarma, RedHunt Labs, AppKnox, CyberSecurityWorks (CSW), Hacken.io, BugBase, Hackrate, and Other Key Players |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user), Multi-User License (Up to 5 Users), and Corporate Use License (Unlimited User) along with free report customization equivalent to 0 analyst working days, 3 analysts working days, and 5 analysts working days respectively. |
Frequently Asked Questions
The Global Crowdsourced Security Market size is expected to reach a value of USD 140.4 million in 2025 and is expected to reach USD 293.0 million by the end of 2034.
North America is expected to have the largest market share in the Global Crowdsourced Security Market, with a share of about 40.3% in 2025.
The Crowdsourced Security Market in the US is expected to reach USD 50.0 million in 2025.
Some of the major key players in the Global Crowdsourced Security Market are HackerOne, Bugcrowd, Synack, Cobalt, and others
The market is growing at a CAGR of 8.5 percent over the forecasted period.