Market Overview
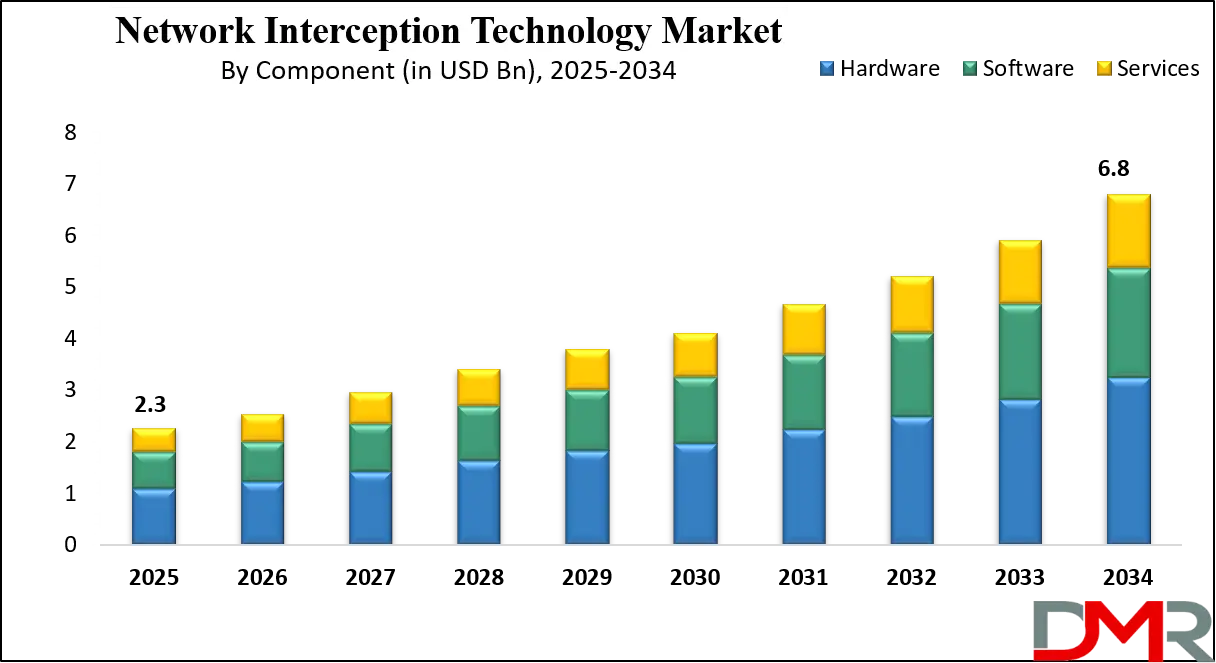
The Global Network Interception Technology Market size is projected to reach USD 2.3 billion in 2025 and grow at a compound annual growth rate of 13.0% from there until 2034 to reach a value of USD 6.8 billion.
Network Interception Technology refers to tools and systems used to monitor, capture, and sometimes alter data as it travels across a network. This can include internet traffic, phone calls, or messages. Governments, intelligence agencies, and some private companies use this technology for security, surveillance, and crime prevention. It works by intercepting data either directly from service providers or through hardware and software inserted in network infrastructure.

Over the past decade, demand for network interception tools has grown steadily. Rising cyber threats, international terrorism, and organized crime have pushed governments to strengthen digital surveillance. The widespread use of encrypted communication apps has also encouraged security agencies to seek better interception tools. Law enforcement and intelligence agencies now need more advanced systems to access data that is often hidden or protected by layers of encryption.
Several important trends have emerged. First, interception technology is becoming more sophisticated, using artificial intelligence and machine learning to sort through vast amounts of data quickly. Second, there's a shift from hardware-based tools to software-driven systems that can operate remotely. Third, many tools now include features that allow real-time monitoring. Lastly, there is an increasing focus on legal and ethical use, especially in democratic countries where privacy concerns are high.
Recent years have seen major global events tied to network interception. For example, media reports on the Pegasus spyware sparked worldwide concern about surveillance overreach. It was revealed that journalists, activists, and even government officials were targeted using advanced interception tools. In another case, several European countries faced criticism for allegedly using interception tools without proper legal oversight. These events brought global attention to the risks of misuse.
The use of interception technology is now more closely examined by lawmakers and courts. Many countries are updating laws to balance security needs with privacy rights. International organizations, such as the UN, have called for clearer rules and more transparency in how such technologies are used. Technology providers are also under pressure to prevent misuse of their products by non-democratic regimes.
As digital communication continues to grow, so will the need for surveillance tools like network interception systems. However, this growth brings challenges. Developers must build tools that are both effective and respectful of privacy. Nations will need to work together to create common standards and ensure responsible use. The future of network interception lies in balancing safety with the rights of individuals.
The US Network Interception Technology Market
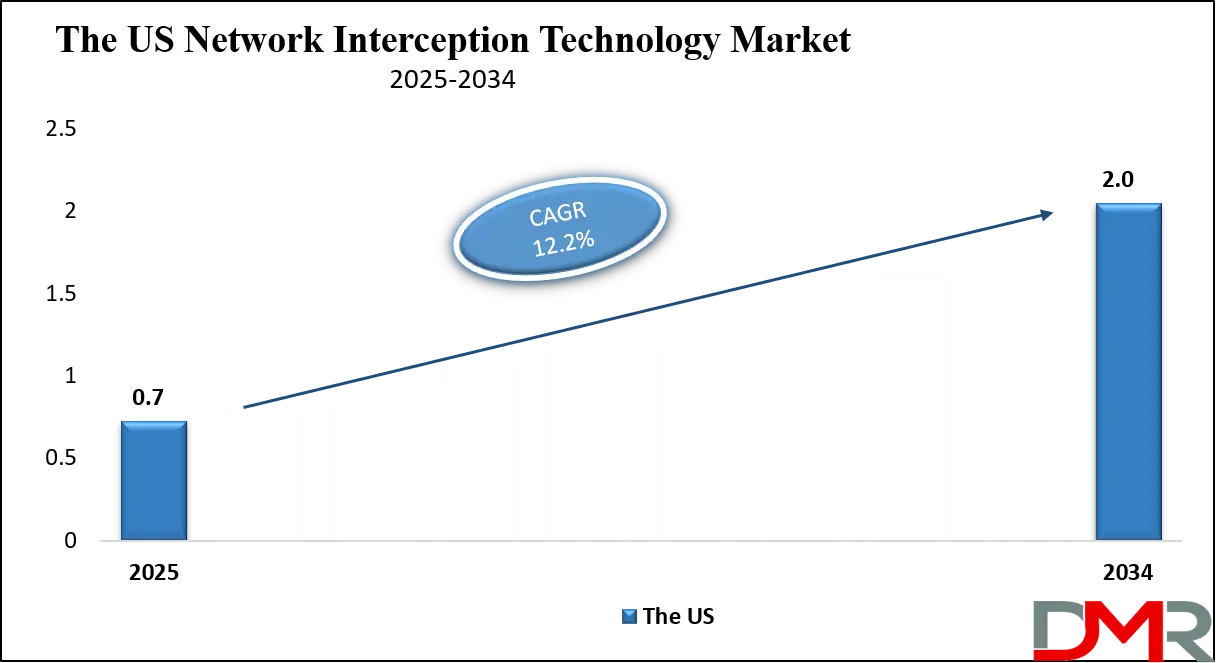
The US Network Interception Technology Market size is projected to reach USD 0.7 billion in 2025 at a compound annual growth rate of 12.2% over its forecast period.
The US plays a leading role in the network interception technology market due to its advanced technological infrastructure and strong focus on national security. US-based agencies heavily invest in surveillance and interception tools to combat cyber threats, terrorism, and organized crime. The US also influences global standards through its intelligence alliances and international partnerships.
Many of the world’s leading developers of interception software and hardware are headquartered in the US, contributing to innovation in areas like artificial intelligence, data analysis, and cloud-based surveillance. Additionally, the US government enforces strict legal frameworks that guide the lawful use of interception technologies.
Europe Network Interception Technology Market
Europe Network Interception Technology Market size is projected to reach USD 0.6 billion in 2025 at a compound annual growth rate of 13.1% over its forecast period.
Europe plays a significant role in the network interception technology market, driven by a strong focus on both security and data privacy. European countries use interception tools primarily for law enforcement, counterterrorism, and cybersecurity purposes. However, Europe is also known for its strict data protection laws, such as the General Data Protection Regulation (GDPR), which influence how interception technologies are developed and used.
European institutions and governments push for transparency, accountability, and ethical use of surveillance tools. Several European nations also collaborate on joint security efforts, sharing intelligence and investing in secure communication monitoring systems. This dual focus on security and rights protection shapes Europe's approach, making it a region that values both innovation and responsible technology use in the interception space.
Japan Network Interception Technology Market
Japan Network Interception Technology Market size is projected to reach USD 0.1 billion in 2025 at a compound annual growth rate of 15.6% over its forecast period.
Japan holds a strategic position in the network interception technology market, driven by its strong emphasis on national security, technological advancement, and cyber defense. As a highly connected society, Japan faces rising threats from cyberattacks, espionage, and organized crime, prompting the government to invest in advanced surveillance and interception tools. Japan integrates interception technologies into its broader cybersecurity infrastructure, focusing on protecting public safety and critical digital infrastructure.
The country also collaborates with international partners to strengthen intelligence sharing and digital monitoring. While Japan maintains strict legal procedures for lawful interception, it continues to develop cutting-edge technologies through its well-established electronics and software industries. This balance of innovation and regulation positions Japan as a key contributor in the global interception landscape.
Network Interception Technology Market: Key Takeaways
- Market Growth: The Network Interception Technology Market size is expected to grow by USD 4.3 billion, at a CAGR of 13.0%, during the forecasted period of 2026 to 2034.
- By Component: The hardware segment is anticipated to get the majority share of the Network Interception Technology Market in 2025.
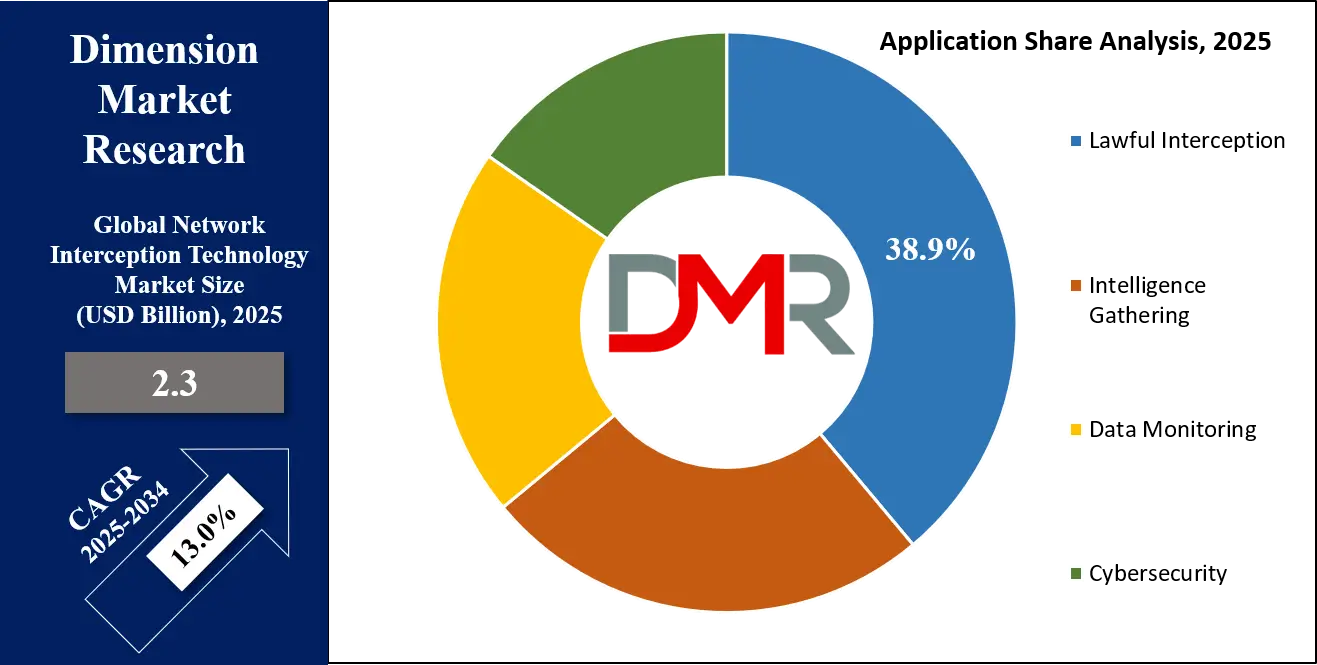
- By Application: The lawful interception segment is expected to get the largest revenue share in 2025 in the Network Interception Technology Market.
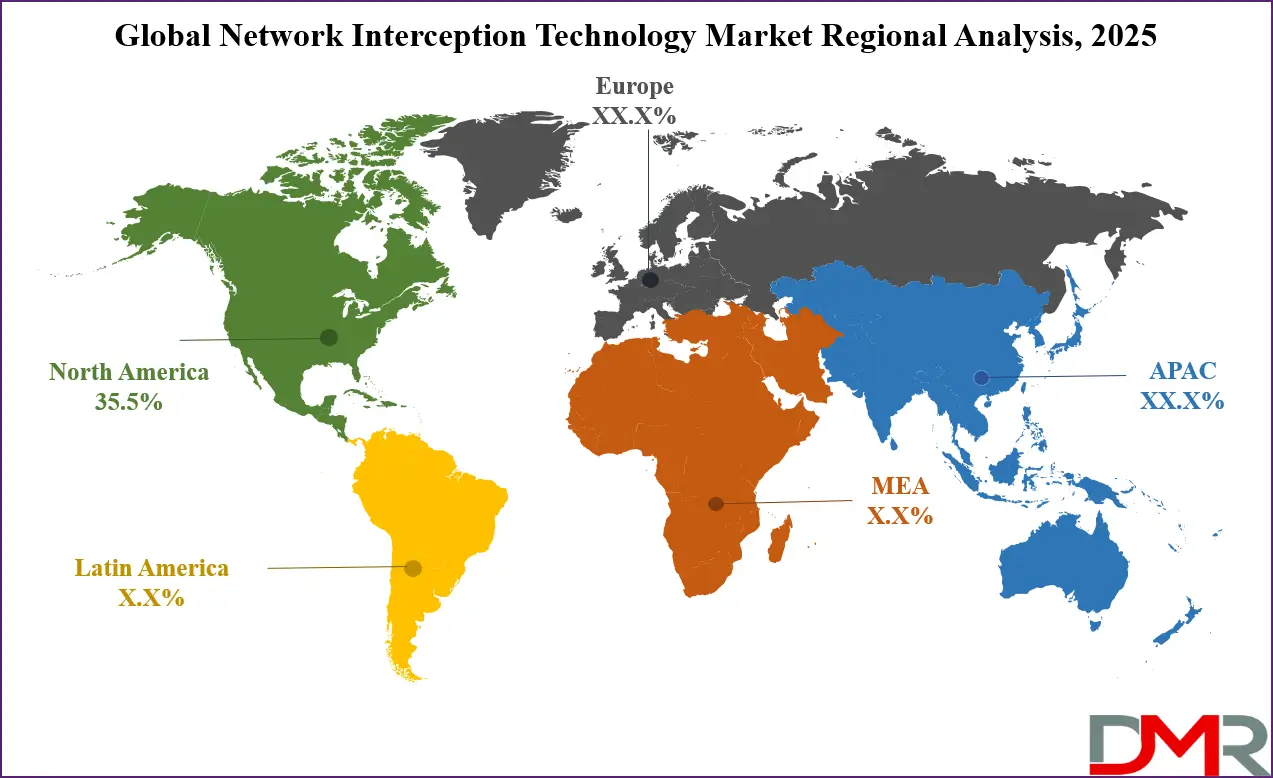
- Regional Insight: North America is expected to hold a 35.5% share of revenue in the Global Network Interception Technology Market in 2025.
- Use Cases: Some of the use cases of Network Interception Technology include border & national security, corporate network monitoring, and more.
Network Interception Technology Market: Use Cases
- Law Enforcement Surveillance: Police and national security agencies use network interception technology to monitor suspects involved in criminal activities. It helps track communication between individuals and detect illegal operations such as drug trafficking, terrorism, or cybercrimes. Real-time access to call records, emails, or chat messages can support investigations and enable quick response.
- Border and National Security: Governments use interception tools at border points and across communication networks to detect and prevent threats to national security. These systems can identify suspicious conversations or data transfers linked to espionage, terrorism, or smuggling. It adds a digital layer of defense beyond physical surveillance.
- Corporate Network Monitoring: Large companies may use interception systems to monitor their internal networks for unauthorized data leaks or insider threats. This helps ensure that sensitive information, such as trade secrets or customer data, is not being stolen or misused. It supports cybersecurity strategies and reduces the risk of internal breaches.
- Telecommunication Regulation Compliance: Telecom providers often install interception tools to comply with legal requirements set by national governments. These systems allow lawful access to user data by authorities under regulated conditions. It ensures telecom operators can cooperate with investigations while following privacy and security laws.
Market Dynamic
Driving Factors in the Network Interception Technology Market
Rising Global Security Concerns
One of the major growth drivers of the network interception technology market is the increasing concern over global security threats. Governments around the world are investing heavily in surveillance tools to combat terrorism, cyberattacks, and organized crime. With digital communication now playing a central role in criminal planning, authorities need advanced tools to track, intercept, and analyze suspicious activity.
The growing use of encrypted messaging apps and virtual private networks (VPNs) has made it harder to monitor threats, pushing demand for more sophisticated interception systems. In addition, rising tensions in global geopolitics have led countries to enhance their intelligence-gathering capabilities. These developments are pushing agencies to adopt cutting-edge technologies that can offer real-time, accurate data interception and analysis.
Expansion of Digital Communication Networks
The rapid expansion of digital communication networks is another key factor driving market growth. With more people using the internet, mobile phones, and cloud-based services, the amount of data being transmitted daily has grown significantly. This increase makes it essential to have tools that can manage and monitor vast streams of information effectively. The growth of smart cities, IoT devices, and remote work environments adds to the complexity, requiring interception systems that can adapt to diverse platforms.
As communication moves across borders and platforms, governments and private sectors alike see a rising need for flexible, scalable solutions. These evolving digital ecosystems are creating new opportunities for network interception technologies across multiple sectors.
Restraints in the Network Interception Technology Market
Privacy and Ethical Concerns
One of the biggest restraints in the network interception technology market is the growing concern over privacy and ethical use. As these tools can access personal messages, calls, and online activities, there is fear of misuse by both governments and private entities. Public backlash and civil rights campaigns have grown stronger, especially after high-profile cases of illegal surveillance came to light. In democratic countries, strict privacy laws make it harder to deploy such technologies freely.
Any misuse can damage public trust and lead to legal consequences, limiting adoption. Developers and users of interception tools are now under pressure to ensure their systems follow ethical guidelines. Balancing national security with individual rights remains a major challenge in this space.
Complex Legal and Regulatory Frameworks
Another major restraint is the complex and constantly changing legal frameworks that govern the use of interception technologies. Different countries have different laws about surveillance, data protection, and lawful access, making it difficult for companies to operate across borders. Even within a single country, legal approval and oversight are often required before interception tools can be used.
This slows down implementation and increases operational costs for providers. In some regions, outdated laws struggle to keep up with new technology, creating confusion and risk of non-compliance. The fear of legal disputes or international backlash also makes governments cautious. This legal uncertainty continues to restrict market expansion and complicates global deployment strategies.
Opportunities in the Network Interception Technology Market
Integration with Artificial Intelligence and Machine Learning
A major opportunity in the network interception technology market lies in integrating artificial intelligence (AI) and machine learning (ML) to enhance system capabilities. AI can help filter and analyze massive amounts of intercepted data, identifying patterns, keywords, or unusual behavior faster than manual processes. This makes it easier for authorities to respond to threats in real time.
Machine learning models can also improve over time, adapting to new types of digital communication and encryption. By reducing false positives and enhancing detection accuracy, AI-driven interception tools can become more efficient and scalable. This opens doors for next-generation solutions that offer both speed and intelligence. As AI technology advances, it will likely play a key role in shaping the future of interception systems.
Growing Demand from Developing Countries
There is a rising opportunity for network interception technology in developing countries that are upgrading their digital and national security infrastructures. As these nations experience growth in internet use, mobile communication, and online services, they also face increasing cyber threats and criminal activities. Many of these governments are now looking for affordable yet effective surveillance solutions to strengthen their internal security. Vendors have a chance to offer tailored, cost-efficient tools suited to regional needs and budgets.
Additionally, international funding and support for anti-terrorism and public safety initiatives are driving adoption in these regions. By expanding into emerging markets, technology providers can tap into new customer bases and long-term partnerships. This global expansion presents a promising path for market growth.
Trends in the Network Interception Technology Market
Integration of Artificial Intelligence and Machine Learning
A significant trend in the network interception technology market is the incorporation of artificial intelligence (AI) and machine learning (ML) to enhance system capabilities. These technologies enable interception systems to analyze vast amounts of data more efficiently, identifying patterns and anomalies that may indicate security threats. By automating data analysis, AI and ML reduce the reliance on manual processes, allowing for quicker and more accurate threat detection.
This advancement not only improves the effectiveness of surveillance operations but also helps in managing the increasing volume and complexity of data generated by modern communication networks. As communication methods evolve, the role of AI and ML in interception technologies is becoming increasingly vital.
Emergence of Cloud-Based Interception Solutions
The shift towards cloud-based interception solutions is another notable trend in the market. Cloud technologies offer scalability and flexibility, allowing interception systems to adapt to varying data volumes and network demands. These solutions facilitate real-time monitoring and analysis of communications across different platforms, enhancing the ability of security agencies to respond promptly to potential threats.
Additionally, cloud-based systems can be more cost-effective and easier to deploy compared to traditional on-premises setups. The adoption of cloud technologies in interception is driven by the need for more agile and responsive surveillance capabilities in the face of rapidly changing communication landscapes
Research Scope and Analysis
By Component Analysis
Hardware as a component in the growth of the Generative Engine Optimization (GEO) market will be leading in 2025, with an expected share of 47.7%. This growth is driven by the increasing need for powerful and efficient physical devices that support complex GEO algorithms and data processing. High-performance processors, GPUs, and specialized chips are essential to handle large-scale computations and improve the speed and accuracy of generative models. As industries adopt GEO for tasks like content creation and data analysis, the demand for reliable hardware infrastructure grows.
Additionally, advances in hardware technology, such as improved memory and faster processing units, enhance overall system performance. These factors contribute to the expanding role of hardware in supporting the efficient deployment and scalability of GEO solutions across various sectors.
Software as a component in the Generative Engine Optimization (GEO) market is expected to see significant growth over the forecast period. The increasing complexity of generative models and demand for customizable, user-friendly software tools drive this expansion. Advanced software solutions enable better control, optimization, and integration of GEO processes, allowing businesses to tailor outputs to their specific needs.
Additionally, improvements in algorithms and user interfaces enhance the accessibility and effectiveness of GEO applications. The rising adoption of cloud-based software platforms also supports remote access and collaboration, fueling further growth. Together, these factors position software as a critical element in advancing the capabilities and reach of GEO technologies in the coming years.
By Interception Method Analysis
The passive interception method is expected to lead the network interception technology market in 2025, with an estimated share of 50.2%. This growth comes from the method’s ability to monitor and capture data without actively interfering with network traffic, making it less detectable and more reliable for continuous surveillance. Passive interception is widely used for collecting voice, video, and data communications across various platforms. Its non-intrusive nature allows organizations to gather intelligence efficiently while minimizing network disruptions.
As communication networks become more complex, passive interception tools are evolving to handle encrypted and high-volume data flows. This adaptability, combined with regulatory acceptance, drives their growing use in law enforcement, national security, and corporate monitoring applications, contributing significantly to the market’s expansion.
Hybrid interception methods are set to see significant growth in the network interception technology market over the forecast period. Combining both passive and active interception techniques, hybrid methods provide greater flexibility and accuracy in capturing communications. This approach allows security agencies to adapt to different network environments and overcome challenges such as encryption and traffic volume.
Hybrid interception offers improved data collection by switching between methods as needed, enhancing threat detection capabilities. Increasing cyber threats and the need for comprehensive surveillance tools are pushing demand for such adaptable solutions. The ability to balance efficiency and thorough monitoring makes hybrid interception an attractive choice, fueling its rise in the market during the coming years.
By Application Analysis
Lawful interception as an application is set to lead the network interception technology market in 2025, with an estimated share of 38.9%. This growth is driven by increasing government regulations that require telecom operators and internet service providers to enable lawful access to communication data. Lawful interception helps law enforcement agencies monitor and investigate criminal activities, terrorism, and threats to national security in a controlled and legal manner.
The rising adoption of communication technologies and growing cybercrime incidents boost the demand for reliable interception systems that comply with privacy and legal standards. Additionally, advancements in interception platforms make it easier to capture encrypted data while respecting lawful boundaries. These factors collectively support the expansion of lawful interception as a critical application within the broader network interception technology market.
Cybersecurity as an application is expected to see significant growth in the network interception technology market over the forecast period. Organizations are increasingly using interception tools to detect and prevent cyber threats such as hacking, malware, and data breaches. By monitoring network traffic in real time, cybersecurity interception systems can identify suspicious activities before they cause harm.
The rise of cloud computing, Internet of Things devices, and remote work has increased network vulnerabilities, making interception technology vital for protecting sensitive information. Enhanced threat detection, faster response times, and compliance with security regulations further drive the adoption of interception solutions in cybersecurity. These trends make cybersecurity an important and growing segment in the network interception technology market.
By End User Analysis
Government and defense as an end user segment is projected to lead the network interception technology market in 2025, with an estimated share of 51.8%. This growth is fueled by the increasing need for national security, intelligence gathering, and counterterrorism efforts. Governments and defense agencies require advanced interception tools to monitor communications, detect threats, and prevent illegal activities. The rise in cyber warfare and digital espionage further pushes the demand for reliable and secure interception systems.
Additionally, investments in upgrading military communication networks and enhancing law enforcement surveillance capabilities contribute to market expansion. The stringent regulations governing lawful interception also support adoption within this sector. Together, these factors position government and defense as the primary drivers behind the rising demand for network interception technology.
Enterprises as an end user segment are expected to see significant growth in the network interception technology market over the forecast period. Businesses increasingly use interception tools to protect sensitive data, prevent insider threats, and ensure compliance with cybersecurity regulations. With the growing reliance on digital communication, companies need efficient systems to monitor network traffic and detect potential breaches or data leaks.
The rise of cloud computing and remote work has also created new security challenges that drive demand for interception solutions. By adopting these technologies, enterprises can strengthen their cybersecurity defenses and safeguard intellectual property. This growing focus on data protection and risk management is helping to boost the role of enterprises in the network interception technology market.
The Network Interception Technology Market Report is segmented on the basis of the following:
By Component
- Hardware
- Software
- Services
By Interception Method
- Active Interception
- Passive Interception
- Hybrid Interception
By Application
- Lawful Interception
- Intelligence Gathering
- Data Monitoring
- Cybersecurity
By End User
- Government & Law Enforcement Agencies
- Telecom Service Providers
- Enterprises
Regional Analysis
Leading Region in the Network Interception Technology Market
The North America region is playing a leading role in the growth of the network interception technology market, with an estimated share of 35.5% in 2025. This strong position comes from the region’s advanced technology infrastructure and high investments in national security and law enforcement agencies. Countries in North America are focusing heavily on protecting their digital communication networks from increasing cyber threats, terrorism, and organized crime. The demand for sophisticated interception tools that can handle encrypted and large-scale data is growing rapidly.
Additionally, strict regulatory frameworks ensure lawful and controlled use of these technologies, which supports market stability. The presence of many technology developers and continuous innovation in AI-driven interception systems further fuel market growth. Overall, North America’s combination of strong security needs, technology innovation, and regulatory support makes it a key driver in expanding the global network interception technology market in coming years.
Fastest Growing Region in the Network Interception Technology Market
The Asia Pacific region is showing significant growth in the network interception technology market over the forecast period due to rapid digitalization and increasing security concerns. Countries in this region are expanding their communication networks and facing rising cyber threats, which drives demand for advanced interception tools. Governments are investing in surveillance systems to monitor criminal activities and protect national security. The growing adoption of smartphones, internet services, and cloud technologies also contributes to market expansion.
Additionally, regulatory changes are encouraging lawful interception and data monitoring, supporting market development. With a focus on improving cybersecurity infrastructure and intelligence capabilities, the Asia Pacific region is estimated to become a key player in the global network interception technology market.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Competitive Landscape
The network interception technology market is becoming more competitive as more players enter the field to meet rising global demand. Companies are working hard to create smarter, faster, and more discreet systems that can handle large volumes of data in real time. Some focus on government contracts, while others develop solutions for private security or telecom providers.
The market includes both long-established technology firms and newer startups offering advanced software tools. Competition is driven by innovation, with companies racing to include features like artificial intelligence, better encryption handling, and improved data filtering. As global concerns about cyber threats and digital privacy grow, firms must also navigate strict legal rules and public pressure for ethical and responsible use of their technologies.
Some of the prominent players in the global Network Interception Technology are:
- Cisco Systems
- BAE Systems
- Palantir Technologies
- Thales Group
- Nokia
- Huawei
- Raytheon Technologies
- HPE (Hewlett Packard Enterprise)
- IBM
- Ericsson
- NSO Group
- Elbit Systems
- Verint Systems
- Boeing
- Northrop Grumman
- Atos
- Siemens
- Check Point Software
- FireEye (Trellix)
- Dell Technologies
- Other Key Players
Recent Developments
- In June 2025, Quantum Network acquired strategic assets from SecureCo, Inc., a U.S. leader in stealth communications and secure data-in-transit solutions. The deal includes SecureCo’s proprietary STRATUS mesh delivery network, cloaked API gateway, and advanced obfuscation architecture, which protect sensitive communications by anonymizing access and reducing attack surfaces. This acquisition allows Quantum Network to further develop and deploy these technologies across government, infrastructure, and enterprise sectors. Terms of the transaction were not disclosed.
- In May 2025, BrowserStack has acquired Requestly, a popular open-source HTTP interception and API mocking tool that tackles key challenges in modern web development. This acquisition enhances BrowserStack’s focus on boosting developer productivity by supporting Requestly’s growth. Requestly helps frontend developers overcome common obstacles, such as waiting for backend APIs and dealing with unstable backend services during testing, by providing advanced tools for HTTP interception, debugging, and mocking network requests. This streamlines workflows and speeds up development and release processes.
- In April 2025, Aliro announced the live deployment of its entanglement-based quantum network, delivering Quantum-Powered Security™ to protect data, voice, and video communications from current and future cyber threats. Leveraging the principles of quantum entanglement, this technology creates provably secure communication channels that go beyond traditional math-based encryption. Aliro’s breakthrough offers unmatched protection, even against emerging quantum computing threats, ensuring organizations stay ahead in cybersecurity.
- In April 2025, Infoblox announced a partnership with Google Cloud to simplify enterprise networking and accelerate cloud transformation. They introduced two solutions: Infoblox Universal DDI™ for Google’s Cloud WAN, combining Google’s global network with Infoblox’s DNS and DHCP, and Google Cloud DNS Armor, a Protective DNS solution powered by Infoblox that detects malicious activity for Google Cloud workloads. Scott Harrell, Infoblox CEO, highlights the partnership’s role in securing hybrid multi-cloud environments and reducing operational complexity for enterprises.
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 2.3 Bn |
| Forecast Value (2034) |
USD 6.8 Bn |
| CAGR (2025–2034) |
13.0% |
| The US Market Size (2025) |
USD 0.7 Bn |
| Historical Data |
2019 – 2024 |
| Forecast Data |
2026 – 2034 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors, etc. |
| Segments Covered |
By Component (Hardware, Software, and Services), By Interception Method (Active Interception, Passive Interception, and Hybrid Interception), By Application (Lawful Interception, Intelligence Gathering, Data Monitoring, and Cybersecurity), By End User (Government & Law Enforcement Agencies, Telecom Service Providers, and Enterprises) |
| Regional Coverage |
North America – US, Canada; Europe – Germany, UK, France, Russia, Spain, Italy, Benelux, Nordic, Rest of Europe; Asia-Pacific – China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC; Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America; Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, Rest of MEA |
| Prominent Players |
Cisco Systems, BAE Systems, Palantir Technologies, Thales Group, Nokia, Huawei, Raytheon Technologies, HPE (Hewlett Packard Enterprise), IBM, Ericsson, NSO Group, Elbit Systems, Verint Systems, Boeing, Northrop Grumman, Atos, Siemens, Check Point Software, FireEye (Trellix), Dell Technologies, and Other Key Players |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user), Multi-User License (Up to 5 Users), and Corporate Use License (Unlimited User) along with free report customization equivalent to 0 analyst working days, 3 analysts working days, and 5 analysts working days respectively. |
Frequently Asked Questions
The Global Network Interception Technology Market size is expected to reach a value of USD 2.3 billion in 2025 and is expected to reach USD 6.8 billion by the end of 2034.
North America is expected to have the largest market share in the Global Network Interception Technology Market, with a share of about 35.5% in 2025.
The Network Interception Technology Market in the US is expected to reach USD 0.7 billion in 2025.
Some of the major key players in the Global Network Interception Technology Market are Cisco Systems, Thales, BAE Systems, and others
The market is growing at a CAGR of 13.0 percent over the forecasted period.