Market Overview
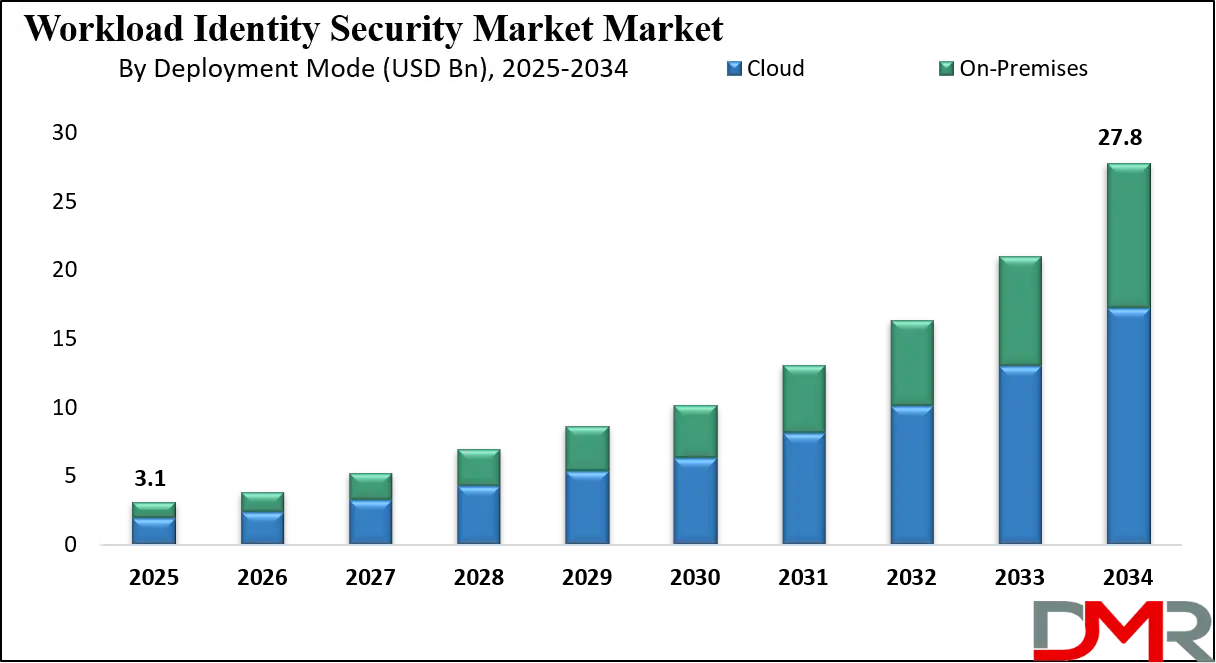
The global workload identity security market is valued at approximately USD 3.1 billion in 2025 and is projected to expand to around USD 27.8 billion by 2034, registering a strong CAGR of 27.7% during the forecast period, driven by rising adoption of cloud native applications, machine identity management solutions, zero trust security frameworks, and identity centric workload protection across hybrid and multi cloud environments.
Workload identity security refers to the set of technologies and practices designed to protect, authenticate, and manage non human identities used by workloads such as applications, containers, microservices, virtual machines, and automated processes operating across cloud and on premises environments.

Unlike human identity security, this approach focuses on securing machine to machine interactions by enforcing strong authentication, least privilege access, credential lifecycle management, and dynamic authorization policies. Workload identity security enables organizations to prevent unauthorized access, credential misuse, lateral movement, and identity based attacks while supporting modern architectures such as cloud native applications, DevOps pipelines, and zero trust security models.
The global workload identity security market represents the expanding ecosystem of software platforms, tools, and services that enable enterprises to secure machine identities across hybrid, multi cloud, and containerized infrastructures. Market growth is being driven by the rapid proliferation of cloud workloads, increased adoption of microservices and Kubernetes environments, and the growing imbalance between human and machine identities within enterprise networks. Organizations are investing in workload identity security solutions to reduce reliance on static secrets, improve compliance with data protection regulations, and enhance visibility and control over automated workloads operating at scale.
Additionally, the market is shaped by rising concerns over identity centric cyber threats, including credential theft, privilege escalation, and misconfigured access policies in cloud environments. Enterprises across industries such as banking, healthcare, government, and information technology are integrating workload identity security into broader identity and access management frameworks to support zero trust initiatives and secure DevOps workflows. As digital transformation accelerates globally, the workload identity security market is expected to evolve with advanced capabilities such as policy based access control, identity aware workload protection, and continuous verification across distributed computing environments.
The US Workload Identity Security Market
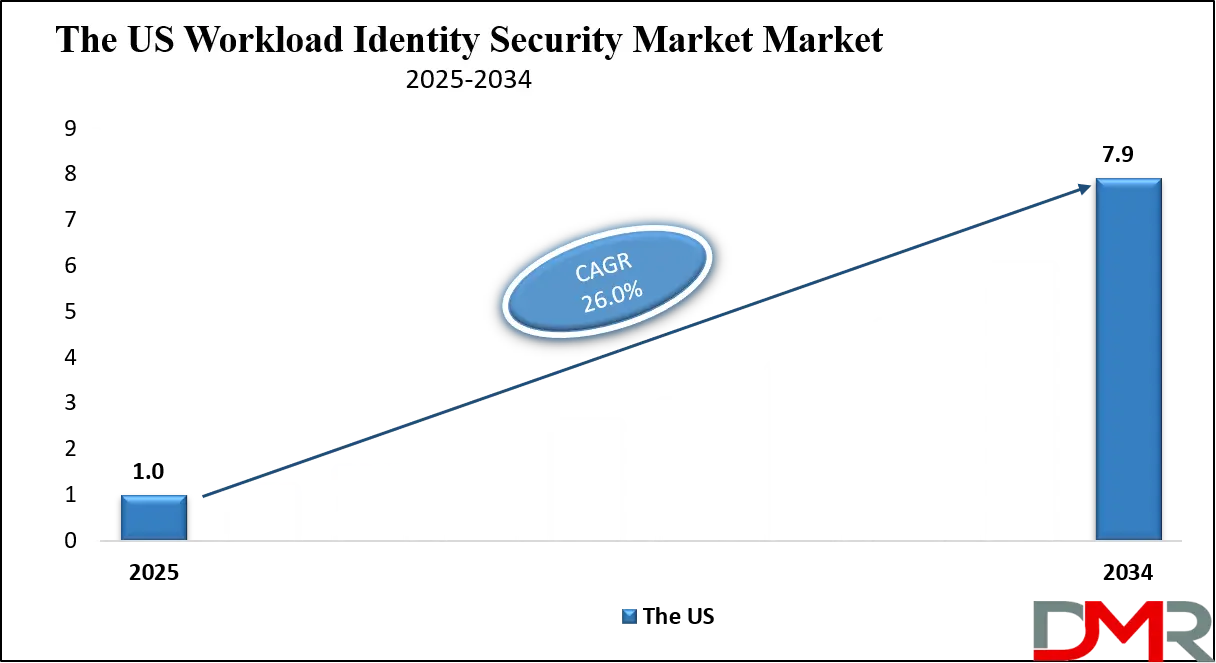
The U.S. Workload Identity Security market size is projected to be valued at USD 1.0 billion by 2025. It is further expected to witness subsequent growth in the upcoming period, holding USD 7.9 billion in 2034 at a CAGR of 26.0%.
The U.S. workload identity security market is witnessing strong expansion as enterprises accelerate cloud migration and adopt cloud native architectures such as containers, microservices, and Kubernetes. Organizations across the country are increasingly prioritizing machine identity management to secure non human identities associated with applications, workloads, and automated processes operating in hybrid and multi cloud environments.
Growing concerns around credential sprawl, unauthorized access, and identity based cyber threats are driving demand for workload identity security solutions that enable dynamic authentication, policy driven access control, and secure workload to workload communication. The widespread adoption of zero trust security models and DevOps practices is further reinforcing the need for identity aware workload protection across the U.S. enterprise landscape.
Additionally, the market is supported by stringent regulatory requirements, high cybersecurity spending, and the strong presence of leading identity security vendors and cloud service providers in the United States. Sectors such as BFSI, healthcare, government, and technology are actively deploying workload identity security platforms to enhance compliance, protect sensitive data, and reduce risks associated with misconfigured permissions and long lived credentials.
The growing use of automation, artificial intelligence driven workloads, and distributed cloud environments is also increasing the complexity of identity governance, creating sustained demand for advanced workload identity security solutions that offer continuous verification, least privilege enforcement, and centralized visibility across large scale digital infrastructures.
Europe Workload Identity Security Market
The Europe workload identity security market is projected to reach approximately USD 700 million in 2025, reflecting strong adoption of cloud native applications, containerized workloads, and automated processes across enterprises in the region. Organizations across industries such as BFSI, healthcare, government, and IT are increasingly investing in machine identity management solutions, zero trust security frameworks, and policy driven access controls to secure both human and non human identities. The market growth is also supported by stringent data protection regulations, rising cybersecurity awareness, and the presence of leading identity security vendors offering advanced solutions tailored for European enterprises.
With a regional CAGR of approximately 25.0%, the Europe market is expected to expand steadily over the forecast period as organizations continue their digital transformation and cloud migration initiatives. The demand for cloud workload protection, lifecycle and credential management, and access management solutions is accelerating as enterprises seek to reduce identity based risks, enforce compliance, and maintain operational continuity. Increasing integration of AI powered analytics for identity threat detection and automated policy enforcement further strengthens market growth, making Europe one of the key regions contributing to the global workload identity security landscape.
Japan Workload Identity Security Market
The Japan workload identity security market is projected to reach approximately USD 200 million in 2025, driven by the rapid adoption of cloud native applications, containerized workloads, and automated processes across enterprises. Japanese organizations, particularly in sectors such as BFSI, IT and telecom, healthcare, and manufacturing, are increasingly investing in machine identity management, zero trust security models, and policy based access controls to protect both human and non human identities. Rising concerns over credential theft, unauthorized workload access, and identity centric cyber threats are further accelerating the deployment of workload identity security solutions across cloud, hybrid, and on premises environments.
With a regional CAGR of around 29.0%, the Japan market is expected to grow robustly over the forecast period as enterprises expand their digital transformation and DevOps initiatives. There is a growing focus on cloud workload protection, access management, and lifecycle credential management, complemented by AI driven analytics for anomaly detection and automated policy enforcement. The increasing integration of advanced identity security tools into enterprise IT ecosystems is helping Japanese organizations reduce risks, ensure compliance with local and global regulations, and maintain operational efficiency, positioning the country as one of the fastest growing markets within the global workload identity security landscape.
Global Workload Identity Security Market: Key Takeaways
- Cloud and Hybrid Workload Growth: Adoption of cloud native apps, containers, and multi cloud infrastructures is driving demand, with cloud deployment capturing 62% of the market share in 2025.
- AI and Automation Integration: AI and automation enhance threat detection, dynamic policy enforcement, and workload visibility, reducing operational overhead.
- Market Consolidation and Investment: Mergers, acquisitions, and funding rounds exceeding USD 700 million reflect strong innovation and market consolidation.
- Zero Trust Adoption: Enterprises increasingly implement zero trust frameworks and policy based access controls to secure machine identities.
- Industry and Regional Focus: BFSI, healthcare, and IT sectors dominate adoption, with North America holding 38% of global market revenue and APAC showing fastest growth.
Global Workload Identity Security Market: Use Cases
- Secure Cloud Native Application Access: Workload identity security is widely used to protect cloud native applications built on microservices and containerized architectures. In global enterprises, applications running across Kubernetes clusters and multi cloud environments rely on secure machine identities to authenticate service to service communication. Workload identity security solutions eliminate hard coded secrets by enabling dynamic identity based authentication and least privilege access. This use case helps organizations prevent unauthorized workload access, reduce credential leakage risks, and improve visibility across distributed cloud workloads while supporting zero trust security frameworks and modern application development practices.
- Protection of DevOps and CI CD Pipelines: In DevOps driven environments, automated build, test, and deployment pipelines require secure access to cloud resources, APIs, and infrastructure services. Workload identity security enables secure authentication for CI CD tools, scripts, and automation workloads without relying on static credentials. By enforcing identity aware access controls and short lived credentials, organizations can protect software supply chains, reduce attack surfaces, and prevent privilege escalation during application deployment. This use case is increasingly important as enterprises adopt continuous integration, infrastructure as code, and cloud based development workflows globally.
- Identity Based Cloud Workload Protection: Enterprises use workload identity security to safeguard virtual machines, containers, and serverless workloads operating across hybrid and multi cloud infrastructures. By assigning unique machine identities to each workload, organizations can enforce granular access policies, monitor workload behavior, and detect identity misuse in real time. This use case supports compliance requirements, improves threat detection capabilities, and strengthens cloud workload protection strategies against identity centric cyber attacks. It is particularly relevant for industries handling sensitive data and operating large scale distributed systems.
- Zero Trust Enforcement for Machine Identities: Workload identity security plays a critical role in implementing zero trust architectures by continuously verifying the identity and permissions of workloads before granting access to resources. Instead of relying on network based trust, organizations apply dynamic policy enforcement based on workload identity, context, and behavior. This use case enables secure workload to workload communication, minimizes lateral movement, and reduces the impact of compromised identities. Globally, enterprises adopt this approach to enhance security posture across complex digital ecosystems while supporting scalability and operational agility.
Impact of Artificial Intelligence on the global Workload Identity Security market
The integration of artificial intelligence into the global workload identity security market is transforming how organizations secure machine identities, enforce access policies, and detect anomalous behavior across cloud and hybrid environments. AI driven analytics and machine learning models are enabling security platforms to process vast amounts of identity telemetry from applications, containers, microservices, and automated processes.
By analyzing patterns of machine to machine interactions, AI can identify deviations from normal behavior that may indicate compromised credentials, misconfigurations, or lateral movement attempts. This improves the accuracy and speed of threat detection beyond traditional rule based systems, helping enterprises reduce security incidents and strengthen identity centric defenses.
Artificial intelligence is also enhancing automation and adaptive response capabilities within workload identity security solutions. Intelligent tools can automatically assess risk scores for workload access requests based on contextual signals such as time, location, resource sensitivity, and historical behavior. This enables dynamic policy enforcement and least privilege access without manual intervention, reducing operational overhead for security teams and minimizing human error.
Moreover, AI driven insights help organizations optimize identity lifecycle management by predicting stale or unused machine identities, recommending credential rotation, and prioritizing remediation actions. As enterprises increasingly adopt cloud native technologies, DevOps practices, and zero trust frameworks, the impact of artificial intelligence on the workload identity security market will continue to expand, driving more proactive, efficient, and scalable identity protection strategies.
Global Workload Identity Security Market: Stats & Facts
FBI IC3 Annual Report (2024)
- In 2024, the FBI’s Internet Crime Complaint Center received 263,455 cyber threat complaints.
- Those complaints resulted in USD 1.571 billion in reported losses from cyber‑enabled fraud.
- 4,878 complaints in 2024 were from critical infrastructure organizations.
- Ransomware and data breaches were among the most reported cyber threats.
FBI Internet Crime Report (State Level, 2024)
- In Texas, the top cybercrime complaint in 2024 was 7,854 extortion cases.
- Personal data breaches accounted for 5,424 complaints in Texas in 2024.
- Phishing/spoofing had 3,987 complaints in the same region.
Identity Theft Resource Center (ITRC via Government Reporting)
- In Q2 2025, there were 913 reported compromise incidents.
- In Q3 2025, 835 compromise incidents were tracked.
- Through Q3 2025, 2,563 total compromises were reported.
- Those led to almost 202 million victim notices so far in 2025.
U.S. Government Accountability Office (GAO) Cybersecurity Reports
- Federal agencies reported 32,211 information security incidents in fiscal year 2023.
- Over 4,000 recommendations have been issued by GAO since 2010 to federal agencies to improve cybersecurity.
- More than 850 GAO cybersecurity recommendations remained unimplemented as of February 2023.
Pew Research Center (survey reported national online crime)
- Nearly 73% of U.S. adults say they have experienced an online scam or attack at some point.
- About 29% reported a personal online account hack within the survey timeframe.
- 24% reported giving away personal information due to a scam email, text, or call.
- More than 9 in 10 Americans view online scams as a national problem.
Global Workload Identity Security Market: Market Dynamics
Global Workload Identity Security Market: Driving Factors
Rapid Growth of Cloud Native and Automated Workloads
The increasing adoption of cloud native applications, microservices architectures, and container orchestration platforms is a major driver of the workload identity security market. As organizations deploy thousands of automated workloads across hybrid and multi cloud environments, the number of non human identities has grown exponentially. This surge has heightened the need for secure machine identity management, dynamic authentication, and policy based access controls to prevent unauthorized workload interactions and identity misuse across distributed systems.
Rising Identity Centric Cybersecurity Threats
Enterprises are facing a growing number of cyberattacks that exploit weak or unmanaged machine identities, such as credential theft, privilege escalation, and lateral movement within cloud infrastructures. Traditional perimeter based security models are no longer sufficient, pushing organizations to adopt workload identity security solutions that align with zero trust principles. The need to protect sensitive data, ensure regulatory compliance, and maintain business continuity is accelerating investment in identity aware workload protection technologies.
Global Workload Identity Security Market: Restraints
Complexity of Integration across Hybrid Environments
Implementing workload identity security across diverse environments that include legacy systems, private data centers, and multiple cloud platforms can be complex. Many organizations struggle to integrate identity security solutions with existing identity and access management frameworks, DevOps tools, and security operations platforms. This complexity can slow adoption and increase deployment costs, particularly for organizations with fragmented IT infrastructures.
Limited Awareness and Skill Gaps
Despite growing cybersecurity investments, many enterprises still lack a clear understanding of workload identity risks and best practices for securing machine identities. Shortages of skilled cybersecurity professionals with expertise in cloud security, DevOps security, and identity governance further limit effective implementation. This lack of awareness and expertise can delay decision making and reduce the effectiveness of workload identity security deployments.
Global Workload Identity Security Market: Opportunities
Expansion of Zero Trust and Identity First Security Models
The global shift toward zero trust architectures presents significant growth opportunities for the workload identity security market. Organizations are increasingly focusing on continuous verification and least privilege enforcement for both human and non human identities. Workload identity security solutions that integrate seamlessly with zero trust frameworks, cloud access controls, and policy engines are well positioned to gain traction as enterprises modernize their security strategies.
Growing Adoption in Regulated and Data Intensive Industries
Industries such as banking, healthcare, government, and critical infrastructure are under increasing pressure to secure automated workloads handling sensitive data. These sectors present strong opportunities for workload identity security vendors offering advanced compliance management, identity lifecycle automation, and real time monitoring capabilities. As regulatory requirements tighten globally, demand for identity aware workload protection is expected to rise significantly.
Global Workload Identity Security Market: Trends
AI Driven Identity Analytics and Automation
Artificial intelligence and machine learning are emerging as key trends within the workload identity security market. AI powered analytics enable real time detection of abnormal workload behavior, automated risk assessment, and adaptive policy enforcement. This trend supports proactive threat prevention, reduces manual intervention, and enhances the scalability of identity security solutions in complex cloud environments.
Shift toward Short Lived Credentials and Secretless Architectures
Organizations are increasingly moving away from static credentials toward short lived identities and secretless authentication methods. This trend reduces the risk of credential exposure and supports secure workload to workload communication across cloud native environments. Workload identity security platforms that enable dynamic credential issuance and automated rotation are gaining prominence as enterprises adopt modern DevOps and cloud security practices.
Global Workload Identity Security Market: Research Scope and Analysis
By Component Analysis
By component analysis, software components are anticipated to dominate the workload identity security market, capturing approximately 74.0% of the total market share in 2025, as organizations increasingly deploy cloud native identity security platforms to manage and secure non human identities across complex digital environments. Software solutions act as the foundational layer of workload identity security by enabling machine identity authentication, dynamic authorization, policy based access control, and credential lifecycle management for applications, containers, microservices, and automated workloads.
The strong dominance of software is also supported by rising adoption of zero trust architectures, DevOps automation, and multi cloud security strategies, where scalable and centrally managed identity platforms are essential for maintaining visibility, compliance, and protection against identity based threats.
The services segment, accounting for the remaining share of the market, plays a critical supporting role in enabling effective deployment and operation of workload identity security solutions. Services include consulting, implementation, system integration, training, and ongoing managed security services that help organizations align workload identity frameworks with existing identity and access management systems and cloud infrastructures.
As enterprises face challenges related to integration complexity, skills shortages, and evolving security requirements, demand for professional and managed services continues to grow. These services help optimize policy configurations, ensure continuous monitoring, and support compliance initiatives, thereby enhancing the overall effectiveness and long term value of workload identity security investments.
By Deployment Mode Analysis
By deployment mode analysis, cloud deployment is anticipated to dominate the workload identity security market, capturing approximately 62.0% of the total market share in 2025, as organizations continue to migrate applications and workloads to public, private, and hybrid cloud environments. Cloud based workload identity security solutions provide the agility and scalability required to secure highly dynamic workloads, including containers, microservices, and serverless functions. These deployments enable centralized identity management, real time policy enforcement, and seamless integration with cloud platforms and DevOps toolchains, making them essential for supporting zero trust security strategies and large scale digital transformation initiatives.
On premises deployment remains an important segment of the market, particularly among organizations operating in highly regulated industries or managing legacy infrastructure that requires direct control over security systems. Enterprises in sectors such as banking, government, and critical infrastructure often prefer on premises workload identity security solutions to meet data sovereignty, compliance, and internal governance requirements.
While growth in this segment is comparatively slower than cloud deployment, on premises solutions continue to play a vital role in hybrid environments by enabling secure workload identity management across both local data centers and cloud platforms, ensuring consistent access control and identity protection across the entire IT ecosystem.
By Organization Size Analysis
By organization size analysis, large enterprises are anticipated to dominate the workload identity security market, capturing approximately 70.0% of the total market share in 2025, as these organizations manage complex IT environments with multiple cloud platforms, applications, and automated workloads. Large enterprises typically face higher exposure to identity based cyber threats and require comprehensive solutions for machine identity management, policy based access control, credential lifecycle management, and zero trust enforcement.
The scale and criticality of operations in sectors such as banking, healthcare, and technology drive significant investment in workload identity security software and services, enabling large organizations to maintain compliance, visibility, and protection across distributed and hybrid infrastructures.
Small and medium enterprises, while representing a smaller share of the market, are increasingly adopting workload identity security solutions to secure cloud native workloads and DevOps pipelines. SMEs face growing risks associated with automated processes, containerized applications, and multi cloud deployments, making identity aware security an essential component of their cybersecurity strategy.
The adoption in this segment is often supported by cloud based deployment models and managed services that reduce implementation complexity and operational overhead. As SMEs continue to accelerate digital transformation, the demand for scalable, cost effective, and easy to deploy workload identity security solutions is expected to grow steadily.
By Security Capability Analysis
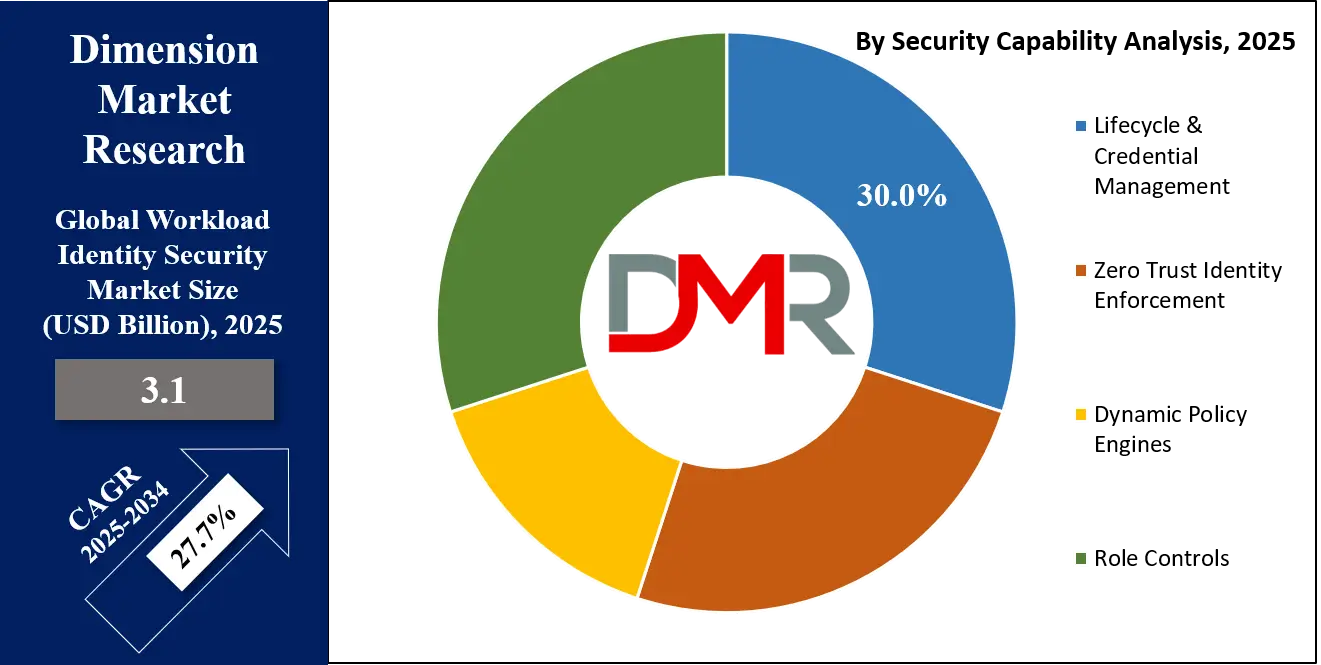
By security capability analysis, lifecycle and credential management is anticipated to dominate the workload identity security market, capturing approximately 32.0% of the total market share in 2025, as organizations seek to efficiently manage the creation, rotation, and retirement of machine identities across cloud, hybrid, and on premises environments.
This capability ensures that workloads such as applications, containers, microservices, and automated processes maintain secure authentication and authorization throughout their lifecycle. Effective lifecycle and credential management reduces the risk of credential theft, prevents unauthorized access, and supports compliance with regulatory frameworks by maintaining visibility and control over all active and dormant machine identities in an enterprise ecosystem.
Zero trust identity enforcement is another critical segment within the security capability category, focusing on continuously verifying the identity, permissions, and context of workloads before granting access to resources. Unlike traditional perimeter based approaches, zero trust enforcement applies dynamic, policy driven controls for machine identities across distributed infrastructures.
This approach minimizes lateral movement, reduces the impact of compromised credentials, and strengthens overall security posture. Enterprises implementing zero trust identity enforcement benefit from enhanced operational security, consistent access governance, and the ability to scale protection across complex, cloud native, and automated workloads.
By Application Analysis
By application analysis, access management is anticipated to dominate the workload identity security market, capturing approximately 41.0% of the total market share in 2025, as organizations prioritize controlling machine identities and managing secure interactions between workloads, applications, and cloud services. Access management solutions enable authentication, authorization, role based access control, and policy enforcement for automated processes and non human identities, ensuring that only authorized workloads can access critical systems and sensitive data.
The prominence of this application is driven by the growing adoption of zero trust security frameworks, hybrid cloud environments, and DevOps practices, which require continuous verification and strict governance of workload identities to prevent unauthorized access and identity based cyber threats.
Cloud workload protection is another key application within the market, focused on safeguarding virtual machines, containers, and serverless workloads deployed across public, private, and hybrid cloud environments. This application assigns unique identities to each workload, enforces fine grained access policies, and continuously monitors workload behavior to detect anomalies or unauthorized interactions.
Cloud workload protection is critical for maintaining operational security, ensuring compliance with regulatory standards, and mitigating identity centric attacks in distributed and automated environments. Its adoption is increasing as enterprises scale cloud native applications and rely on automated workloads that demand secure, real time identity management and policy enforcement.
By Industry Vertical Analysis
By industry vertical analysis, the BFSI sector is anticipated to dominate the workload identity security market, capturing approximately 35.0% of the total market share in 2025, as financial institutions face stringent regulatory requirements and heightened exposure to identity based cyber threats. Banks, insurance companies, and other financial organizations rely heavily on automated processes, cloud applications, and digital transactions, which increase the number of machine identities requiring secure management.
Workload identity security solutions in this sector provide robust authentication, role based access controls, credential lifecycle management, and continuous monitoring to prevent unauthorized access, fraud, and lateral movement within critical systems while supporting compliance with global standards such as PCI DSS, GDPR, and SOX.
The IT and telecommunications industry also represents a significant segment within the workload identity security market, driven by the rapid adoption of cloud services, DevOps workflows, and digital transformation initiatives. Service providers and technology companies manage a vast number of applications, APIs, and automated workloads that require secure machine to machine interactions.
Workload identity security solutions in this sector enable secure authentication, policy enforcement, and continuous verification for workloads, ensuring operational continuity and protecting sensitive customer and enterprise data. The adoption of zero trust frameworks and identity centric security models further accelerates demand in IT and telecom, as organizations seek to mitigate risks associated with credential misuse, misconfigured access, and identity based attacks across distributed and hybrid infrastructures.
The Workload Identity Security Market Report is segmented on the basis of the following:
By Component
By Deployment Mode
By Organization Size
By Security Capability
- Lifecycle & Credential Management
- Zero Trust Identity Enforcement
- Dynamic Policy Engines
- Role Controls
By Application
- Access Management
- Cloud Workload Protection
- Compliance & Policy
- DevOps Security
- Threat Detection & Response
- Others
By Industry Vertical
- BFSI
- IT & Telecom
- Healthcare
- Retail
- Government
- Manufacturing
- Others
Global Workload Identity Security Market: Regional Analysis
Region with the Largest Revenue Share
North America is anticipated to lead the global workload identity security market, accounting for approximately 38.0% of total market revenue in 2025, driven by early adoption of cloud native applications, extensive deployment of hybrid and multi cloud infrastructures, and the presence of leading identity security vendors. Enterprises in the region are increasingly implementing zero trust frameworks, DevOps workflows, and machine identity management solutions to secure automated workloads, containers, and microservices. The region’s strong regulatory environment, high cybersecurity spending, and focus on identity centric protection further reinforce North America’s dominance, making it the largest and most mature market for workload identity security solutions globally.
Region with significant growth
The Asia Pacific region is expected to witness significant growth in the global workload identity security market over the coming years, driven by rapid cloud adoption, digital transformation initiatives, and increasing deployment of cloud native applications and automated workloads across industries. Organizations in countries such as China, India, Japan, and Australia are investing in machine identity management, zero trust security frameworks, and DevOps integrated security solutions to protect cloud and hybrid infrastructures. Rising cybersecurity awareness, regulatory compliance requirements, and the expansion of IT and telecom sectors are further fueling demand, positioning Asia Pacific as one of the fastest growing regions in the workload identity security market.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Global Workload Identity Security Market: Competitive Landscape
The competitive landscape of the global workload identity security market is characterized by the presence of diverse vendors offering a broad range of identity centric solutions and services designed to secure machine identities, streamline authentication, and enforce dynamic access policies across cloud, hybrid, and on‑premises environments. Market competition is driven by continuous innovation in areas such as zero trust enforcement, credential lifecycle management, automated threat detection, and seamless integration with DevOps pipelines and identity governance frameworks.
Vendors are increasingly differentiating through advanced analytics, scalable cloud native architectures, and managed services to address the evolving needs of enterprises across verticals. Strategic partnerships, platform expansions, and a focus on customer experience further shape the market, as organizations prioritize comprehensive, interoperable identity security solutions that can adapt to complex digital infrastructures and emerging cyber threats.
Some of the prominent players in the global Workload Identity Security market are:
- CyberArk
- Microsoft
- Okta
- HashiCorp
- IBM
- Ping Identity
- Google Cloud
- Amazon Web Services (AWS)
- BeyondTrust
- Delinea (Thycotic)
- One Identity
- SailPoint Technologies
- Oracle
- Akamai Technologies
- Saviynt
- JumpCloud
- Auth0 (part of Okta)
- Fugue (part of Snyk)
- Sonrai Security
- Ermetic
- Other Key Players
Global Workload Identity Security Market: Recent Developments
- December 2025: Token Security extended its identity governance platform with a new AI agent identity lifecycle management capability to help enterprises gain visibility and control over autonomous and non‑human identities, strengthening workload and machine identity security across hybrid cloud environments.
- December 2025: ServiceNow announced its intent to acquire an AI‑native identity security platform to integrate identity access intelligence and governance into its broader security and risk portfolio, enabling organizations to manage permissions and secure both human and machine identities.
- December 2025: An identity security firm raised USD 700 million in growth equity funding at an approximate USD 3 billion valuation to establish identity security as a foundational layer for securing access and machine identities in the AI era.
- October 2025: A major identity security provider expanded its machine identity security portfolio with advanced discovery and context‑driven capabilities that automatically identify, assess, and secure machine identities such as certificates, keys, secrets, and workload credentials to simplify compliance and reduce risk at scale.
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 3.1 Bn |
| Forecast Value (2034) |
USD 27.8 Bn |
| CAGR (2025–2034) |
27.7% |
| The US Market Size (2025) |
USD 1.0 Bn |
| Historical Data |
2019 – 2024 |
| Forecast Data |
2026 – 2034 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors, etc. |
| Segments Covered |
By Component (Software, Services); By Deployment Mode (Cloud, On-Premises); By Organization Size (Large Enterprises, SMEs); By Security Capability (Lifecycle & Credential Management, Zero Trust Identity Enforcement, Dynamic Policy Engines, Role Controls); By Application (Access Management, Cloud Workload Protection, Compliance & Policy, DevOps Security, Threat Detection & Response, Others); and By Industry Vertical (BFSI, IT & Telecom, Healthcare, Retail, Government, Manufacturing, Others) |
| Regional Coverage |
North America – US, Canada; Europe – Germany, UK, France, Russia, Spain, Italy, Benelux, Nordic, Rest of Europe; Asia-Pacific – China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC; Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America; Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, Rest of MEA |
| Prominent Players |
CyberArk, Microsoft, Okta, HashiCorp, IBM, Ping Identity, Google Cloud, Amazon Web Services, BeyondTrust, Delinea (Thycotic), One Identity, SailPoint Technologies, Oracle, Akamai Technologies, and Others. |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user), Multi-User License (Up to 5 Users), and Corporate Use License (Unlimited User) along with free report customization equivalent to 0 analyst working days, 3 analysts working days, and 5 analysts working days respectively. |
Frequently Asked Questions
The global Workload Identity Security market size is estimated to have a value of USD 3.1 billion in 2025 and is expected to reach USD 27.8 billion by the end of 2034.
The US Workload Identity Security market is projected to be valued at USD 1.0 billion in 2025. It is expected to witness subsequent growth in the upcoming period as it holds USD 7.9 billion in 2034 at a CAGR of 26.0%.
North America is expected to have the largest market share in the global Workload Identity Security market, with a share of about 38.0% in 2025.
Some of the major key players in the global Workload Identity Security market are CyberArk, Microsoft, Okta, HashiCorp, IBM, Ping Identity, Google Cloud, Amazon Web Services, BeyondTrust, Delinea (Thycotic), One Identity, SailPoint Technologies, Oracle, Akamai Technologies, and Others.