Market Overview
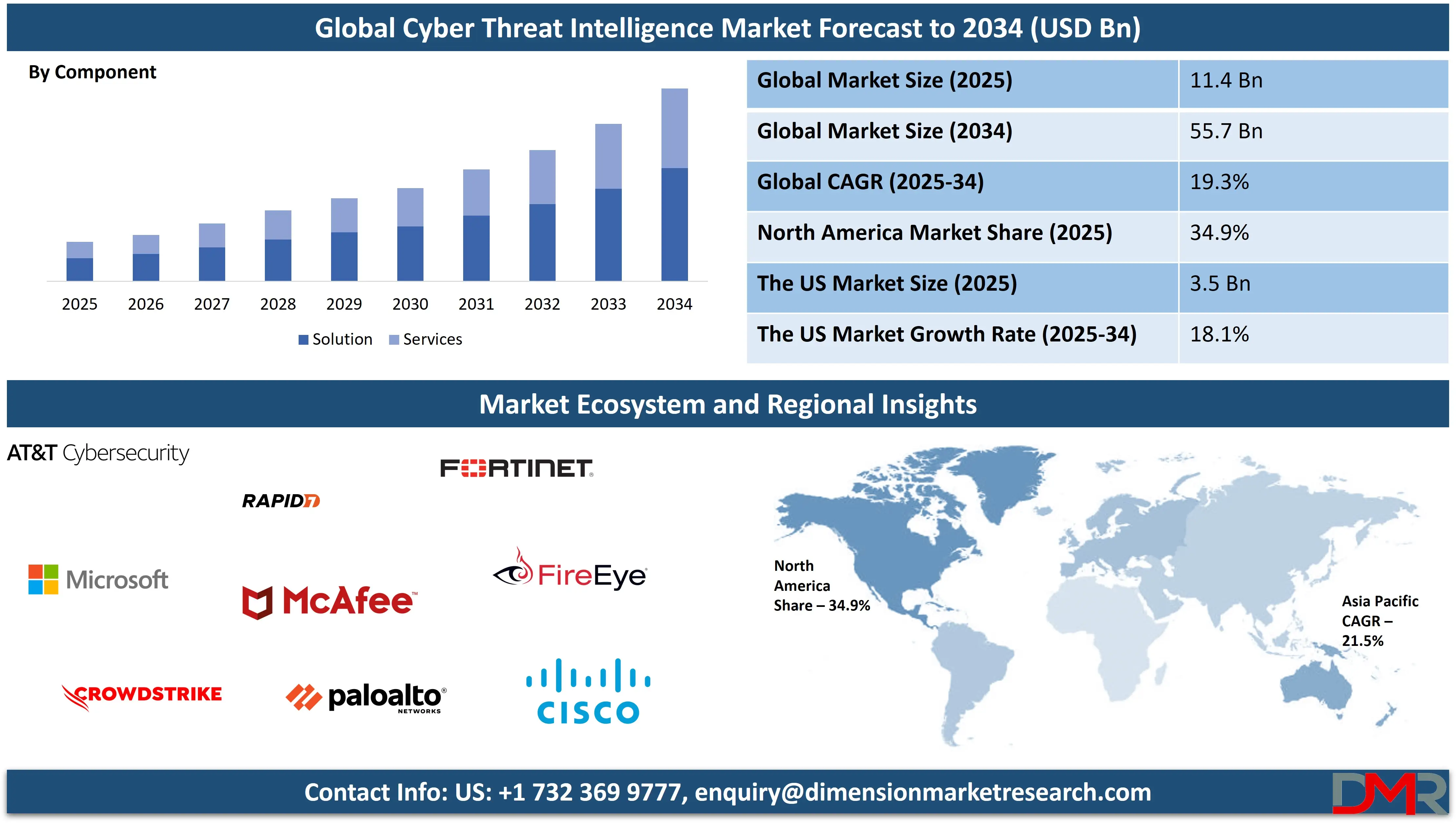
The Global Cyber Threat Intelligence Market size is projected to reach USD 11.4 billion in 2025 and grow at compound annual growth rate of 19.3% to reach a value of USD 55.7 billion in 2034.
Cyber Threat Intelligence (CTI) refers to the process of collecting, analyzing, and applying information about potential or existing cyber threats. This information helps organizations understand who might attack them, why, and how. CTI goes beyond basic cybersecurity measures by offering context about the threats, such as motivations, targets, and tactics. It helps security teams take preventive actions, respond faster to attacks, and reduce the risk of damage. CTI can be strategic (long-term planning), tactical (improving defenses), operational (response to attacks), or technical (detection of specific threats like malware).
ℹ
To learn more about this report –
Download Your Free Sample Report Here
The growth in cyber threats has increased the demand for better intelligence. Several factors are driving the rise of CTI solutions. First, the number and complexity of cyberattacks are growing, especially ransomware, phishing, and nation-state threats. Second, digital transformation and remote work have increased the attack surface for organizations. Third, data protection rules and compliance needs are pushing businesses to improve their defenses. Fourth, there's a shortage of skilled cybersecurity professionals, and CTI helps fill that gap by automating threat detection and response.
Some major trends are shaping the CTI market. One trend is the growing use of artificial intelligence and machine learning to process large amounts of data and detect threats faster. Another is the shift toward threat intelligence sharing, where organizations collaborate to defend against common enemies. There’s also a rise in the use of CTI in sectors beyond just banking and government, such as healthcare, retail, and energy. Integration with Security Information and Event Management (SIEM) and extended detection and response (XDR) platforms is also becoming common.
Recent years have seen major cyber events that underline the importance of CTI. High-profile breaches such as those at large IT companies and government agencies have revealed vulnerabilities that could have been identified earlier with better intelligence. Attacks on supply chains, where hackers target smaller vendors to reach larger companies, have become more common. The rise of ransomware-as-a-service models has also made it easier for less skilled criminals to launch attacks. These events show why CTI must be proactive and constantly updated.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
Cyber Threat Intelligence is also evolving to address new challenges. Attackers are using more advanced techniques, including deepfakes and AI-generated content. This forces CTI teams to stay ahead by analyzing not just technical indicators but also behavioral patterns and geopolitical developments. Threat intelligence now includes monitoring the dark web, social media, and hacker forums to detect early signs of planned attacks. The goal is to turn raw data into insights that can be used to stop threats before they cause harm.
The US Cyber Threat Intelligence Market
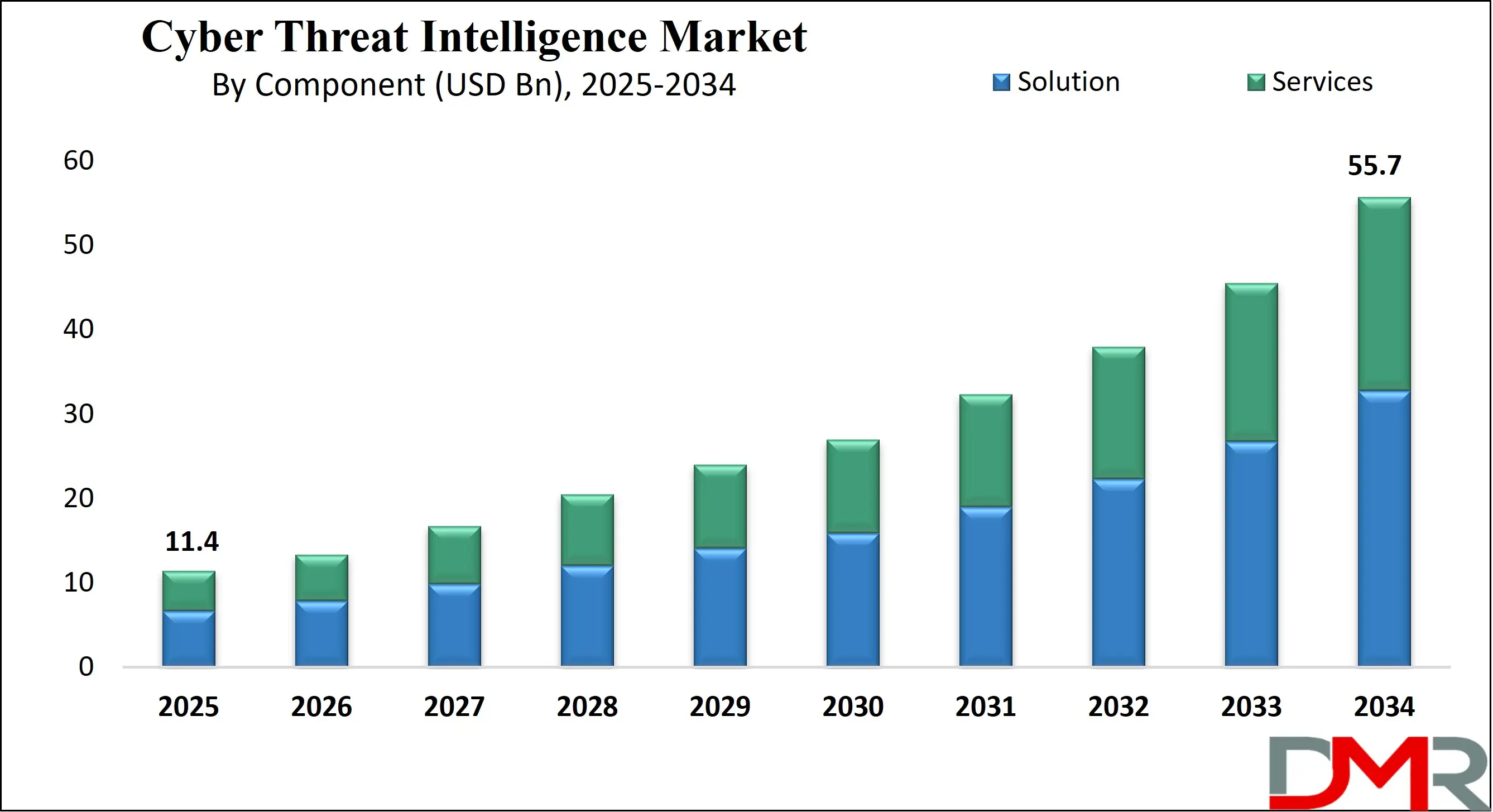
The US Cyber Threat Intelligence Market size is projected to reach USD 3.5 billion in 2025 at a compound annual growth rate of 18.1% over its forecast period.
The US plays a leading role in the Cyber Threat Intelligence market due to its advanced digital infrastructure, high cybercrime exposure, and strong government and private sector investment in cybersecurity. With numerous technology giants, cybersecurity firms, and federal initiatives, the US drives innovation and adoption of threat intelligence tools. Agencies like the FBI, NSA, and DHS actively support CTI development and public-private information sharing.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
The country’s strict regulatory environment, including frameworks like NIST and CISA directives, further encourages organizations to adopt proactive intelligence-based defenses. The US also hosts several global threat intelligence hubs and collaborates internationally to combat emerging threats. This makes the US a central force in shaping the global CTI landscape through leadership, funding, and technological advancement.
Europe Cyber Threat Intelligence Market
Europe Cyber Threat Intelligence Market size is projected to reach USD 3.4 billion in 2025 at a compound annual growth rate of 17.5% over its forecast period.
Europe plays a vital role in the Cyber Threat Intelligence market by promoting regulatory-driven adoption and cross-border collaboration. With strong data protection laws like GDPR, organizations in Europe are increasingly focused on proactive cybersecurity measures, including threat intelligence. The European Union supports CTI through agencies like ENISA and initiatives that encourage information sharing among member states. Countries such as Germany, France, and the UK are leading in building national cyber defense strategies that rely heavily on intelligence-led security.
Europe also invests in research and development to improve threat detection capabilities and supports public-private partnerships. The region’s emphasis on digital sovereignty and secure infrastructure is driving demand for CTI solutions across sectors like finance, government, energy, and healthcare.
Japan Cyber Threat Intelligence Market
Japan Cyber Threat Intelligence Market size is projected to reach USD 570 million in 2025 at a compound annual growth rate of 19.8% over its forecast period.
Japan plays a growing role in the Cyber Threat Intelligence market, driven by its focus on national security, technological advancement, and preparation for large-scale events. With its strong industrial base and high digital connectivity, Japan faces increasing cyber risks that require proactive defense strategies. The government is actively promoting cybersecurity through national policies and partnerships between public and private sectors.
Japanese organizations are investing in CTI to protect critical infrastructure, financial systems, and advanced manufacturing networks. There's also an emphasis on building domestic capabilities, reducing reliance on foreign threat intelligence sources. As Japan continues to modernize its digital ecosystem, CTI is becoming a central part of its cybersecurity framework, especially in response to rising threats from cyber espionage and organized attacks.
Cyber Threat Intelligence Market: Key Takeaways
- Market Growth: The Cyber Threat Intelligence Market size is expected to grow by USD 42.3 billion, at a CAGR of 19.3%, during the forecasted period of 2026 to 2034.
- By Component: The solution is anticipated to get the majority share of the Cyber Threat Intelligence Market in 2025.
- By Deployment Mode: The cloud segment is expected to get the largest revenue share in 2025 in the Cyber Threat Intelligence Market.
- Regional Insight: North America is expected to hold a 34.9% share of revenue in the Global Cyber Threat Intelligence Market in 2025.
- Use Cases: Some of the use cases of Cyber Threat Intelligence include vulnerability management, risk management & planning, and more.
Cyber Threat Intelligence Market: Use Cases
- Incident Response Enhancement: Cyber Threat Intelligence helps security teams respond faster and more effectively to cyberattacks. By providing context about the threat actor, their tactics, and past behavior, it enables quicker decision-making. This reduces downtime and limits the impact of breaches.
- Vulnerability Management: CTI identifies which vulnerabilities are actively being exploited in the wild, helping organizations prioritize which ones to fix first. Instead of patching everything at once, teams can focus on high-risk weaknesses. This makes patch management more strategic and efficient.
- Security Operations Center (SOC) Support: Threat intelligence feeds into SOC tools to improve threat detection and reduce false positives. Analysts gain insights into ongoing attack trends and indicators of compromise. This helps in refining alert systems and focusing on real threats.
- Risk Management and Planning: CTI informs business leaders about emerging cyber risks that could affect operations or reputation. It supports strategic decisions such as investments in new security measures. This makes cyber risk a part of broader enterprise risk management.
Stats & Facts
-
According to CrowdStrike:
- A 442% spike in vishing operations was recorded between the first and second half of 2024, showing how attackers are rapidly evolving social engineering tactics to exploit voice-based communication channels.
- 52% of all vulnerabilities observed during 2024 were linked to initial access vectors, highlighting how attackers are targeting entry points to gain footholds in networks before executing broader campaigns.
- 26 new adversaries were named in 2024, reflecting the expanding threat landscape and the increasing sophistication and diversity of threat actors tracked globally.
- The fastest eCrime breakout time was clocked at just 51 seconds, signaling an urgent need for real-time threat detection and response capabilities across security operations.
- 79% of all detections were malware-free, emphasizing that traditional malware-based indicators are no longer sufficient, as attackers now rely on stealthier, fileless methods to compromise systems.
- There has been a 150% rise in China-nexus activity targeting organizations across multiple sectors, indicating a sharp increase in state-linked cyber operations aimed at espionage and disruption on a global scale.
Market Dynamic
Driving Factors in the Cyber Threat Intelligence Market
Rise in Sophisticated Cyberattacks
As cybercriminals and nation-state actors adopt more advanced and stealthy attack methods, organizations are facing increasingly complex threats that traditional security tools struggle to detect. These include zero-day vulnerabilities, ransomware-as-a-service, and targeted phishing campaigns. The growing number of endpoints, cloud environments, and remote users adds to the challenge.
Cyber Threat Intelligence (CTI) provides the contextual awareness needed to identify and counter these evolving threats. It helps security teams understand attacker behavior, tactics, and intent. This proactive defense approach is driving demand across industries. As cyber threats continue to escalate in scale and severity, CTI becomes a vital investment for resilience and continuity.
Need for Proactive Security Posture
Organizations are shifting from reactive to proactive cybersecurity strategies, and threat intelligence plays a central role in this transition. Instead of waiting for an attack to happen, companies are now seeking to understand threats before they strike. CTI enables early warning systems, informed decision-making, and preemptive responses. It supports everything from real-time monitoring to long-term risk planning.
This shift is especially important in critical sectors like finance, healthcare, and government, where data protection and system integrity are crucial. As regulatory pressures and digital transformation grow, the need for proactive, intelligence-driven security is fueling the adoption of CTI solutions worldwide.
Restraints in the Cyber Threat Intelligence Market
High Implementation and Operational Costs
Despite its benefits, Cyber Threat Intelligence (CTI) solutions often come with high costs related to setup, integration, and ongoing operations. Small and mid-sized businesses may find it difficult to afford advanced CTI tools and skilled analysts required to manage them effectively. The expenses related to data collection, analysis platforms, and subscriptions to threat feeds can add up quickly.
Additionally, integrating CTI with existing security infrastructure requires technical expertise and customization, which further increases costs. These financial and operational burdens can slow down adoption, especially in regions or sectors with limited cybersecurity budgets. Cost remains a major restraint for market growth.
Lack of Skilled Professionals and Contextual Understanding
CTI is a complex domain that requires professionals who can interpret data accurately and translate it into actionable insights. However, there is a global shortage of cybersecurity experts with the experience and analytical skills needed for effective threat intelligence management. Without proper understanding, organizations may either misread the intelligence or fail to act on it in time.
Moreover, raw threat data without the right context may overwhelm security teams with noise rather than clarity. The limited availability of trained personnel and contextual awareness poses a serious barrier to fully utilizing CTI solutions, especially in less mature cybersecurity environments.
Opportunities in the Cyber Threat Intelligence Market
Integration with AI and Machine Learning Technologies
The growing use of artificial intelligence (AI) and machine learning (ML) in cybersecurity presents a strong opportunity for enhancing Cyber Threat Intelligence (CTI). These technologies can automate the collection, correlation, and analysis of massive volumes of threat data in real-time. This enables faster identification of emerging threats, patterns, and anomalies that human analysts might miss.
AI-driven CTI can also reduce false positives and improve the accuracy of predictions. As cyber threats become more dynamic and adaptive, combining CTI with AI/ML will help organizations stay ahead. This integration offers scalable, efficient, and smarter intelligence solutions for businesses of all sizes.
Expansion in Emerging Markets and SMEs
There is a significant opportunity for CTI growth in emerging economies and among small and medium-sized enterprises (SMEs). As these regions undergo rapid digital transformation, they become increasingly vulnerable to cyber threats. However, many still lack mature cybersecurity frameworks. Cloud-based and affordable CTI solutions can help fill this gap by offering accessible intelligence tools without heavy infrastructure investments.
Vendors who offer localized solutions, multi-language support, and simplified dashboards are likely to gain traction in these untapped markets. Expanding awareness, training, and partnerships in these regions can drive CTI adoption and help secure digital growth in underserved sectors and geographies.
Trends in the Cyber Threat Intelligence Market
AI‑Empowered Autonomous Intelligence
Organizations are increasingly adopting AI-driven systems to automate threat detection and response. These tools can hunt and analyze threats autonomously, acting in real‑time with minimal human intervention. Such autonomous agents can monitor anomalous behavior, generate mitigation strategies, and even block attacks before they unfold. This shift enhances scalability and consistency in intelligence operations and frees skilled analysts to focus on strategic tasks.
Wide-Scale Threat Intelligence Sharing Networks
There's growing reliance on collaborative intelligence sharing through sector-specific groups and public-private exchanges. Businesses and critical infrastructure operators are participating in shared platforms to pool insights into phishing, malware, and state-sponsored campaigns. This collective defense approach accelerates threat detection and improves preparedness across industries, especially in finance, healthcare, and energy sectors.
Impact of Artificial Intelligence in Cyber Threat Intelligence Market
- Faster Threat Detection and Response: AI enables real-time analysis of massive volumes of data from multiple sources, helping identify threats much faster than manual methods. It detects patterns, anomalies, and suspicious behavior that may indicate an ongoing or emerging attack.
- Reduced False Positives: AI algorithms improve accuracy by learning from past alerts and distinguishing between genuine threats and harmless anomalies. This helps reduce alert fatigue for security teams and allows them to focus on high-risk incidents.
- Automated Threat Intelligence Processing: AI automates the collection, sorting, and correlation of threat data from diverse feeds, such as malware signatures, phishing attempts, and attack indicators, enabling quicker and smarter decision-making.
- Predictive Threat Analysis: Machine learning models use historical data to predict potential attack vectors, helping organizations prepare in advance and strengthen weak points before they are targeted.
- Adaptive Security Systems: AI-powered CTI systems continuously learn from new data and adapt to changing attacker tactics, ensuring defenses stay relevant against evolving threats.
Research Scope and Analysis
By Component Analysis
Solution as a component is expected to be leading in 2025 with a share of 58.7%, playing a major role in driving the growth of the Cyber Threat Intelligence market. Organizations are increasingly relying on advanced threat detection tools, threat analytics platforms, and real-time alerting systems to stay ahead of cyber risks. These solutions help security teams detect, analyze, and respond to potential threats before they cause serious damage. The demand for integrated threat intelligence platforms that can work across cloud, on-premises, and hybrid environments is rising.
As cyberattacks become more frequent and complex, businesses prefer scalable and automated solutions that offer better visibility and faster response. The growing need for securing critical infrastructure and digital assets is also encouraging companies to adopt full-featured Cyber Threat Intelligence solutions, especially in industries like banking, telecom, and government. This growing preference for advanced tools is pushing solution providers to constantly innovate and improve their offerings.
Services as a component is expected to have significant growth over the forecast period as organizations seek expert support to manage, customize, and scale their Cyber Threat Intelligence capabilities. Services include consulting, integration, training, and managed threat intelligence, which help businesses implement and operate CTI solutions effectively.
Many organizations, especially small and mid-sized ones, lack the in-house expertise to handle complex threat environments, making professional services essential. These services offer deep analysis, tailored intelligence, and continuous monitoring, helping companies build a proactive defense posture. As the threat landscape continues to evolve, the need for specialized services to interpret and act on intelligence data is rising, making this segment a key contributor to market growth.
By Deployment Mode Analysis
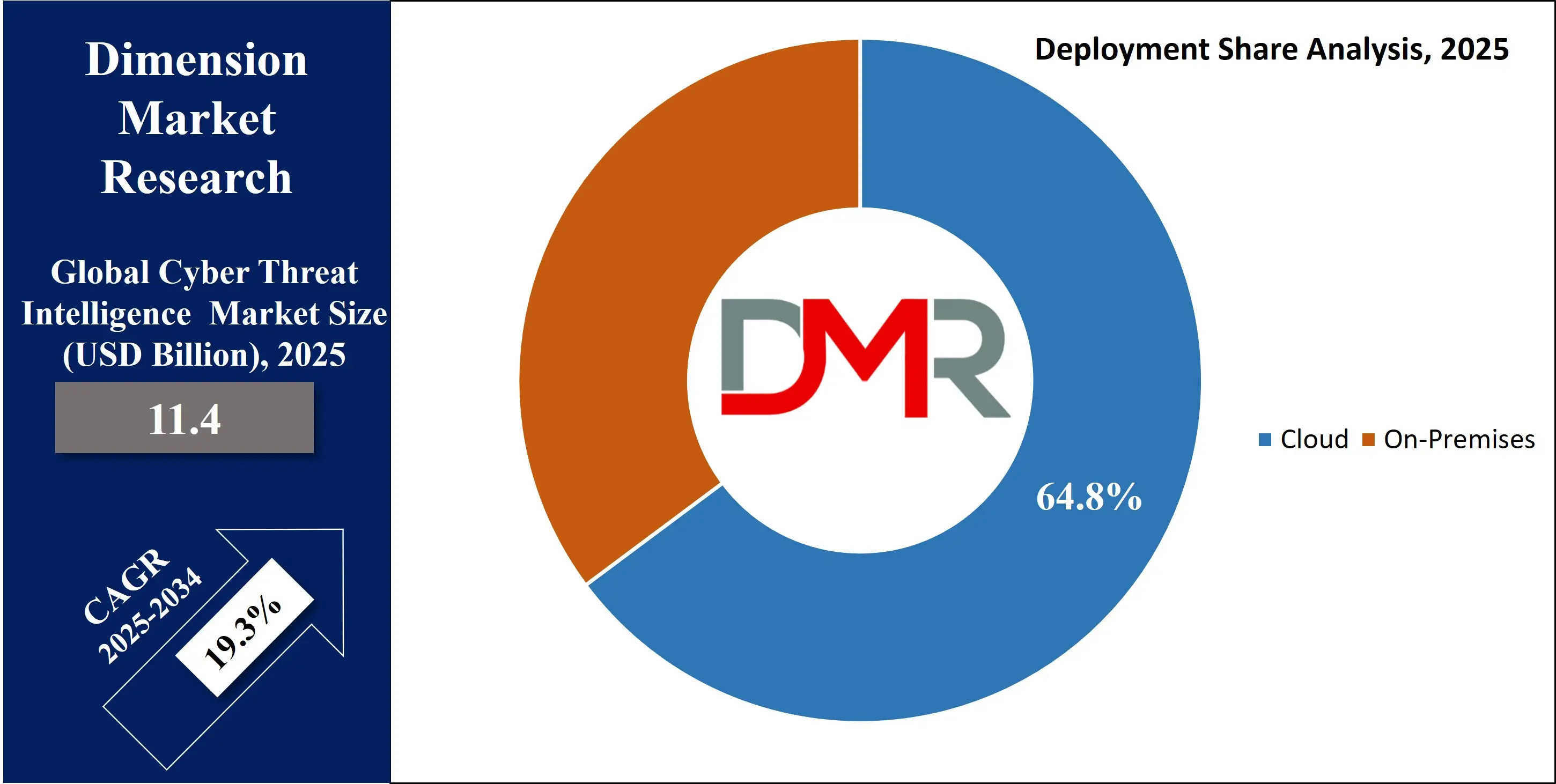
Cloud as a deployment mode is expected to be dominate in 2025 with a share of 64.8%, supporting the rapid growth of the Cyber Threat Intelligence market due to its flexibility, scalability, and cost-efficiency. Businesses are shifting from traditional models to cloud-based platforms for faster deployment and easier access to real-time threat data. Cloud deployments allow organizations to update, manage, and scale their intelligence solutions without heavy hardware or maintenance costs. They support remote security operations, which is essential in today’s hybrid and remote work environments.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
Cloud-based threat intelligence tools also integrate well with other cloud-native cybersecurity solutions, making threat detection and response more efficient. With growing cyberattacks targeting cloud infrastructure, organizations are prioritizing cloud-native CTI systems to ensure faster incident response and broader protection. The strong demand for real-time updates, centralized dashboards, and seamless integration is pushing more companies toward cloud-based deployment in the CTI market.
On-premises as a deployment mode is expected to have significant growth over the forecast period as certain industries continue to prioritize full control over their cybersecurity infrastructure. Sectors like defense, banking, and critical infrastructure often require on-site solutions due to strict data protection rules and internal compliance standards. On-premises Cyber Threat Intelligence systems provide organizations with greater customization and allow sensitive data to remain within secured internal networks.
Although this deployment mode involves higher costs and maintenance, it is preferred by enterprises dealing with confidential or regulated information. The need for tighter security, regulatory compliance, and dedicated infrastructure keeps on-premises solutions relevant. As cyber threats evolve, organizations with strict data governance continue to rely on locally hosted CTI platforms for better oversight and control.
By Organization Size Analysis
Large enterprises as an organizational size is expected to be leading in 2025 with a share of 67.1%, driving the growth of the Cyber Threat Intelligence market due to their vast digital infrastructure and increased exposure to complex cyber threats. These organizations handle high volumes of sensitive data, making them prime targets for cybercriminals and state-sponsored attacks. As a result, they invest heavily in advanced threat detection platforms, threat feeds, and analytics tools to prevent breaches.
Large enterprises often have dedicated cybersecurity teams and budgets, allowing them to adopt full-featured CTI solutions integrated across multiple departments and regions. They also comply with strict regulatory standards, which increases the demand for continuous monitoring and actionable intelligence. With rising risks in sectors like finance, manufacturing, telecom, and healthcare, large enterprises rely on CTI to stay ahead of evolving threats, secure their operations, and protect customer and business-critical information.
SMEs as an organizational size are expected to witness significant growth over the forecast period in the Cyber Threat Intelligence market, mainly due to increasing awareness of cybersecurity risks and growing digital presence. As small and mid-sized businesses become more reliant on digital tools and cloud-based operations, they face similar threats as larger enterprises but often lack the internal resources to defend against them.
This has led to increased demand for affordable, easy-to-deploy CTI solutions tailored to smaller organizations. Cloud-based threat intelligence platforms and managed security services are helping SMEs detect and respond to threats in real-time without the need for large IT teams. The growing availability of subscription-based models and threat-sharing networks is making CTI more accessible, allowing SMEs to protect their operations while scaling securely in a digital-first world.
By Application Analysis
IEM as an application is expected to lead in 2025 with a share of 22.4%, contributing strongly to the growth of the Cyber Threat Intelligence market by enhancing real-time monitoring and automated threat detection. Security Information and Event Management platforms use CTI to improve the accuracy of alerts and reduce false positives. They collect and analyze data from various sources—networks, devices, applications—to identify suspicious activity and potential breaches. By integrating with threat intelligence feeds, SIEM tools gain deeper context, allowing security teams to prioritize threats based on risk and relevance.
This not only improves incident response time but also supports compliance and audit readiness. With rising cyber threats and increasing data complexity, organizations rely on SIEM solutions to centralize visibility, correlate security events, and respond proactively. The growing need for integrated and intelligent security frameworks makes SIEM a key application area in the CTI landscape.
Security Analytics as an application is expected to have significant growth over the forecast period, supporting the expansion of the Cyber Threat Intelligence market through its advanced threat detection capabilities. This application uses big data analysis, behavioral modeling, and machine learning to uncover hidden threats that traditional tools may miss. Security analytics platforms benefit from CTI by adding context to anomalies, helping analysts understand whether activity is truly malicious.
As cyberattacks become more sophisticated, security teams need smarter tools that can interpret patterns and predict threats before damage occurs. Organizations are increasingly adopting analytics-driven approaches to gain deeper visibility across their IT environment. This proactive strategy strengthens overall security posture, making security analytics a fast-growing and essential application of CTI.
By Threat Type Analysis
APTs as a threat type are expected to be leading in 2025 with a share of 20.9%, driving the growth of the Cyber Threat Intelligence market due to their highly targeted, stealthy, and long-term nature. Advanced Persistent Threats are often carried out by skilled attackers, including state-sponsored groups, aiming to gain unauthorized access and remain undetected within a network for extended periods. These attacks are usually aimed at stealing sensitive information or disrupting critical infrastructure. To detect and respond to APTs effectively, organizations require advanced CTI tools that offer real-time threat detection, behavior tracking, and contextual analysis.
The growing frequency of such attacks, especially on government bodies, financial institutions, and tech companies, is pushing the demand for more sophisticated intelligence platforms. CTI enables proactive defense by identifying attack patterns, mapping adversary behavior, and helping security teams respond before damage occurs, making it essential in tackling the rise of APTs globally.
Zero-day Exploits as a threat type are expected to witness significant growth over the forecast period as organizations seek better tools to defend against unknown and unpatched vulnerabilities. These exploits take advantage of software flaws that vendors are not yet aware of, leaving systems highly exposed to advanced attacks. Since traditional security tools cannot detect what is not known, Cyber Threat Intelligence becomes critical in identifying patterns, collecting indicators, and understanding attacker behavior.
CTI solutions use behavior analytics, threat modeling, and community threat sharing to detect signs of zero-day activity. As the number of connected devices and complex software systems increases, the threat of zero-day attacks grows. Organizations are now investing in intelligence-driven security to gain
The Cyber Threat Intelligence Market Report is segmented on the basis of the following
By Component
- Solutions
- Services
- Professional Services
- Managed Services
By Deployment Mode
By Organization Size
- Small and Medium Enterprises (SMEs)
- Large Enterprises
By Application
- Security Information and Event Management (SIEM)
- Threat Intelligence Platforms (TIP)
- Risk & Compliance Management
- Incident Response
- Security Analytics
- Others
By Threat Type
- Advanced Persistent Threats (APT)
- Zero-day Exploits
- Insider Threats
- Distributed Denial of Service (DDoS)
- Malware
- Phishing
- Others
Regional Analysis
Leading Region in the Cyber Threat Intelligence Market
North America will be leading the Cyber Threat Intelligence market in 2025 with a share of 34.9%, driven by strong technological infrastructure, rising cyberattacks, and a well-established cybersecurity ecosystem. The region includes major players in the cybersecurity industry, advanced threat detection platforms, and significant government backing through national security programs. In the US and Canada, both public and private sectors are highly focused on strengthening their cyber defenses, pushing the adoption of threat intelligence solutions across industries. The presence of a skilled cybersecurity workforce, active regulatory frameworks, and early adoption of cloud and AI technologies contribute to the market’s rapid growth.
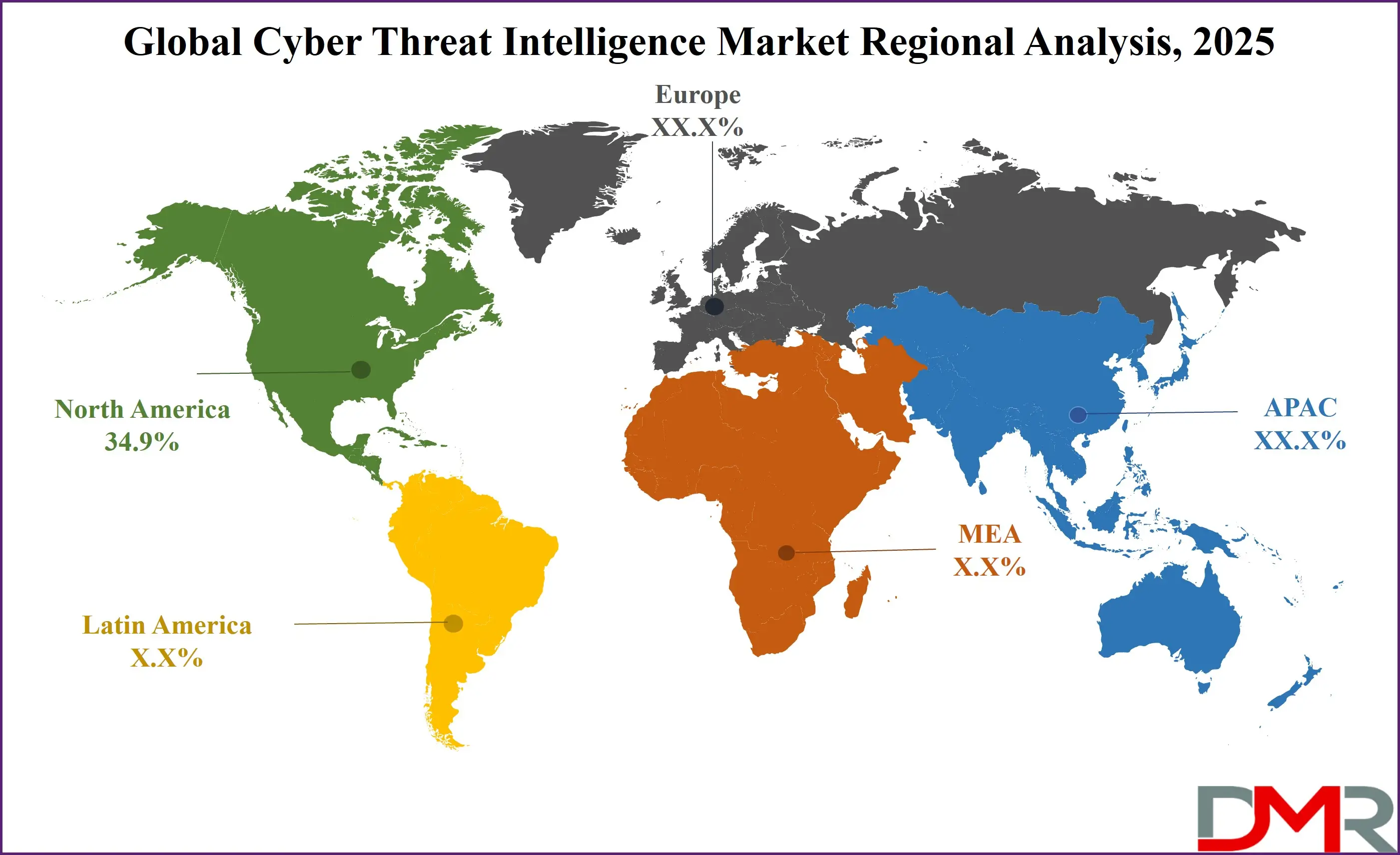
ℹ
To learn more about this report –
Download Your Free Sample Report Here
North America also promotes collaboration through information-sharing alliances that help companies prepare for and respond to evolving threats. With increasing digital transformation, especially in finance, healthcare, and defense, the demand for real-time, actionable intelligence continues to rise. As the region faces complex and frequent cyber threats, it remains a global leader in developing and implementing advanced Cyber Threat Intelligence solutions.
Fastest Growing Region in the Cyber Threat Intelligence Market
Asia Pacific is showing significant growth in the Cyber Threat Intelligence market over the forecast period due to rising cyber threats, rapid digital adoption, and increasing investment in cybersecurity infrastructure. Countries like China, India, South Korea, and Australia are focusing on strengthening their threat detection and response systems across sectors such as banking, defense, and healthcare.
Growing reliance on cloud computing, IoT, and mobile technologies is creating a larger attack surface, pushing demand for threat intelligence platforms. Governments in the region are also supporting cybersecurity awareness and data protection initiatives. With more organizations adopting proactive security measures, Cyber Threat Intelligence solutions are gaining traction across both public and private sectors.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Competitive Landscape
The cyber threat intelligence market is highly competitive, with many global and regional players offering a wide range of solutions and services. Companies compete by improving their technologies, enhancing real-time threat detection, and integrating with existing security systems. The market also sees partnerships, mergers, and acquisitions to expand capabilities and customer reach. Cloud-based intelligence platforms, AI-driven analysis, and threat-sharing frameworks are becoming key focus areas. As threats evolve, companies aim to provide faster, more accurate, and customized intelligence to meet the needs of different industries. The competition continues to grow as demand rises across both large enterprises and smaller businesses.
Some of the prominent players in the global Cyber Threat Intelligence are:
- IBM
- Cisco
- Palo Alto Networks
- CrowdStrike
- FireEye (now Trellix)
- McAfee
- Fortinet
- Check Point Software Technologies
- Broadcom (Symantec)
- Microsoft
- Rapid7
- Splunk
- RSA Security
- AT&T Cybersecurity
- Accenture
- Trend Micro
- Kaspersky
- Secureworks
- SentinelOne
- Elastic N.V.
- Other Key Players
Recent Developments
- In July 2025, Intel 471 introduced Verity471, its next-generation cyber threat intelligence (CTI) platform. Verity471 unifies Intel 471’s full suite of offerings into one intuitive platform, streamlining intelligence operations, enhancing team collaboration, and improving workflow efficiency. It delivers out-of-the-box, actionable insights that empower security teams to not only detect threats but also respond effectively. Designed for diverse security and risk scenarios, Verity471 offers seamless access to three robust intelligence portfolios, strengthening organizations’ overall threat readiness and cyber defense strategies.
- In May 2025, Cyware launched a cybersecurity solution suite customized for State, Local, Tribal, and Territorial (SLTT) governments across the U.S. As cyberattacks on public infrastructure grow more advanced, Cyware equips SLTT teams with unified threat intelligence, automation, and collaboration tools to turn fragmented data into coordinated action. With 77% of SLTT agencies citing poor coordination and 37% lacking confidence in incident response, this launch aims to strengthen collective cyber defense and resilience.
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 11.4 Bn |
| Forecast Value (2034) |
USD 55.7 Bn |
| CAGR (2025–2034) |
19.3% |
| Historical Data |
2019 – 2024 |
| The US Market Size (2025) |
USD 3.5 Bn |
| Forecast Data |
2025 – 2033 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors, etc. |
| Segments Covered |
By Component (Solutions and Services), By Deployment Mode (Cloud-based and On-premise), By Organization Size (Small and Medium Enterprises (SMEs) and Large Enterprises), By Application (Security Information and Event Management (SIEM), Threat Intelligence Platforms (TIP), Risk & Compliance Management, Incident Response, Security Analytics, and Others), By Threat Type (Advanced Persistent Threats (APT), Zero-day Exploits, Insider Threats, Distributed Denial of Service (DDoS), Malware, Phishing, and Others) |
| Regional Coverage |
North America – US, Canada; Europe – Germany, UK, France, Russia, Spain, Italy, Benelux, Nordic, Rest of Europe; Asia-Pacific – China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC; Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America; Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, Rest of MEA |
| Prominent Players |
IBM, Cisco, Palo Alto Networks, CrowdStrike, FireEye (now Trellix), McAfee, Fortinet, Check Point Software Technologies, Broadcom (Symantec), Microsoft, Rapid7, Splunk, RSA Security, AT&T Cybersecurity, Accenture, Trend Micro, Kaspersky, Secureworks, SentinelOne, Elastic N.V., and Other Key Players |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user), Multi-User License (Up to 5 Users), and Corporate Use License (Unlimited User) along with free report customization equivalent to 0 analyst working days, 3 analysts working days, and 5 analysts working days respectively. |
Frequently Asked Questions
How big is the Global Cyber Threat Intelligence Market?
▾ The Global Cyber Threat Intelligence Market size is expected to reach a value of USD 11.4 billion in 2025 and is expected to reach USD 55.7 billion by the end of 2034.
Which region accounted for the largest Global Cyber Threat Intelligence Market?
▾ North America is expected to have the largest market share in the Global Cyber Threat Intelligence Market, with a share of about 34.9% in 2025.
How big is the Cyber Threat Intelligence Market in the US?
▾ The Cyber Threat Intelligence Market in the US is expected to reach USD 3.5 billion in 2025.
Who are the key Cyber Threat Intelligence Market?
▾ Some of the major key players in the Global Cyber Threat Intelligence Market are Broadcom Inc., IBM, Cisco, and others
What is the growth rate in the Global Cyber Threat Intelligence Market?
▾ The market is growing at a CAGR of 19.3 percent over the forecasted period.