ℹ
To learn more about this report –
Download Your Free Sample Report Here
Over the past few years, IAM has become more important due to the growing cyberattacks and data breaches. As companies store more sensitive data online, they need strong controls to prevent unauthorized access. IAM systems are also essential for meeting privacy and security rules that governments and industry groups set. For example, regulations like GDPR and HIPAA require organizations to manage user access carefully. IAM helps them prove they are following these rules.
The demand for IAM is growing because the workplace is changing. People now work from different locations, using multiple devices and cloud apps, which means that access control has to be flexible and work across various platforms. In the past, companies had physical servers and office-based staff. Now, with remote work and cloud computing, IAM needs to manage access from anywhere, at any time, in a secure way.
A few major trends have shaped IAM in recent years. One is the move from passwords to more secure login methods, such as
Facial Recognition Technology, fingerprint scans, or one-time passcodes. Another trend is the use of AI to detect suspicious behavior. If a system notices someone logging in from a strange location or accessing files they usually don’t, it can flag this as a possible threat. Also, companies are shifting to identity-as-a-service (IDaaS), where IAM tools are offered as a cloud service.
Some key events have also pushed IAM forward. Large data breaches at major companies revealed how weak access controls can lead to big problems. These events have led to more investment in IAM solutions. Mergers and partnerships in the tech industry have also created better IAM tools, combining different features into single platforms. IAM has also become a top priority in digital transformation projects.
The US Identity & Access Management Market
The US Identity & Access Management Market size is projected to reach USD 7.5 billion in 2025 at a compound annual growth rate of 8.2% over its forecast period.
The US plays a major role in the Identity & Access Management (IAM) market due to its strong technology sector, early adoption of cybersecurity solutions, and strict data protection regulations. US-based companies are mostly at the forefront of developing advanced IAM tools, including cloud-based platforms, AI-driven access controls, and
Biometric Technology such as biometric authentication..
The growing cyberattacks targeting critical infrastructure and businesses in the US has driven significant investment in IAM solutions. Additionally, federal and state compliance requirements, such as HIPAA and CCPA, push organizations to implement secure identity systems. The country’s large enterprise base and growing remote workforce further increase demand. As a result, the US remains a major driver of innovation, adoption, and revenue in the global IAM market.
Europe Identity & Access Management Market
Europe Identity & Access Management Market size is projected to reach USD 5.5 billion in 2025 at a compound annual growth rate of 8.0% over its forecast period.
Europe plays a vital role in the Identity & Access Management (IAM) market, largely driven by strict data protection regulations such as the General Data Protection Regulation (GDPR). These rules require organizations to manage user identities and access rights carefully, boosting the demand for reliable IAM solutions. European businesses and government agencies are adopting IAM to ensure compliance, secure digital operations, and protect sensitive data.
The region also sees growing use of cloud services and remote work, which further increases the need for secure access control. Additionally, Europe is home to several IAM solution providers and supports innovation through strong cybersecurity initiatives. As a result, Europe remains a key region influencing IAM standards, policies, and technology development globally.
Japan Identity & Access Management Market
Japan Identity & Access Management Market size is projected to reach USD 1.3 billion in 2025 at a compound annual growth rate of 9.6% over its forecast period.
Japan is growing and plays important role in the Identity & Access Management (IAM) market, driven by its focus on digital transformation and strong cybersecurity policies. As Japanese businesses adopt cloud services and remote work models, the need for secure and efficient IAM systems is increasing. The government also encourages cybersecurity improvements through national strategies and data protection regulations.
Industries such as finance, manufacturing, and healthcare are implementing IAM tools to protect sensitive data and meet compliance requirements. Japan’s advanced technology infrastructure supports the adoption of modern IAM features like biometric authentication and AI-based access controls. With a rising awareness of cyber risks and a strong push toward secure digital innovation, Japan contributes significantly to the development and growth of the IAM market in Asia.
Identity & Access Management Market: Key Takeaways
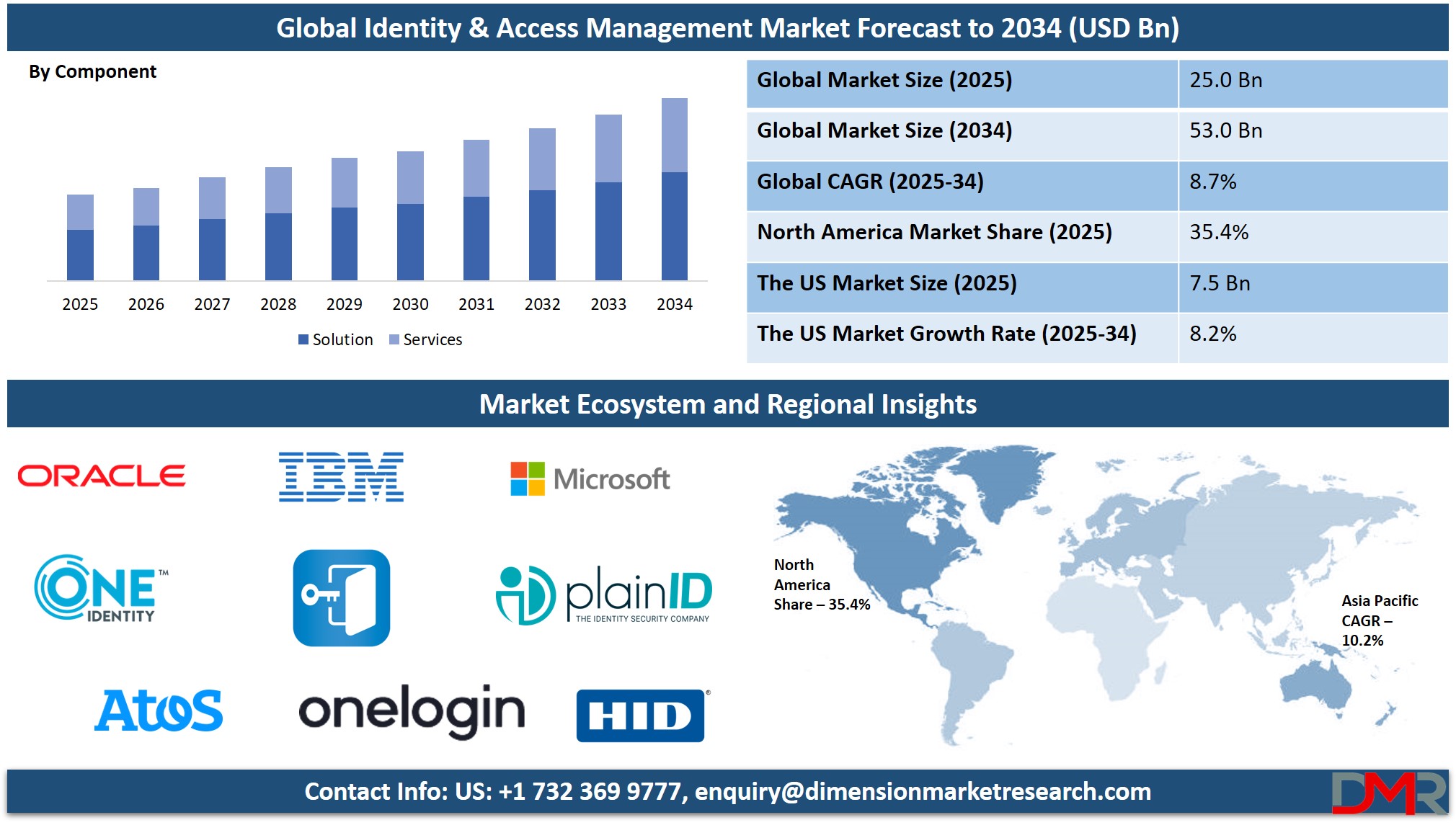
- Market Growth: The Identity & Access Management Market size is expected to grow by USD 26.9 billion, at a CAGR of 8.7%, during the forecasted period of 2026 to 2034.
- By Component: The solution segment is anticipated to get the majority share of the Identity & Access Management Market in 2025.
- By Organization Size: The Large enterprises is expected to get the largest revenue share in 2025 in the Identity & Access Management Market.
- Regional Insight: North America is expected to hold a 35.4% share of revenue in the Global Identity & Access Management Market in 2025.
- Use Cases: Some of the use cases of Identity & Access Management include secure remote access, regulatory compliance, and more.
Identity & Access Management Market: Use Cases:
- Employee Onboarding & Offboarding: When a new employee joins, IAM systems help assign the right access based on their role. They ensure the person can only use the tools and data needed for their job. When the employee leaves, IAM automatically removes access, reducing security risks.
- Secure Remote Access: IAM enables employees to safely log in to company systems from anywhere. It uses features like multi-factor authentication to confirm their identity, which helps businesses support remote work while keeping sensitive information safe.
- Regulatory Compliance: IAM supports organizations in following privacy and security rules by tracking who accesses what data and when. It creates detailed logs for audits and proves that only authorized users handle sensitive information, which is key for meeting industry and government standards.
- Protection Against Insider Threats: IAM limits what each user can access, based on their role and behavior patterns. If someone tries to access restricted data or acts suspiciously, the system can detect and stop it, which minimizes the risk of data leaks from within the company.
Stats & Facts
- According to CyberArk, 99% of security decision makers believe their organizations will experience an identity-related compromise within the next year, driven by the expanding number of identities and the increasing complexity of IT environments. Further, it reveals that the number of identities—both human and machine—is expected to grow by 240% in just 12 months, significantly widening the attack surface.
- IBM reports that 40% of data breaches involve data stored across multiple environments, with public cloud-stored data breaches resulting in the highest average cost of USD 5.17 million. The use of generative AI and IoT further complicates cloud security, requiring organizations to implement better governance and monitoring practices across hybrid infrastructures.
- CrowdStrike highlights that 80% of all cyberattacks use identity-based techniques, such as credential theft and privilege escalation, to infiltrate systems, indicating that identity is now the primary target for threat actors across most sectors.
- Mimecast research finds that 3 out of 4 CISOs believe collaboration tools bring significant new risks, and 94% say the native security features in Microsoft 365 are not sufficient. This shows a growing need for enhanced email and collaboration tool security in enterprise environments.
- IBM found that organizations implementing AI and automation in their cybersecurity strategies saved an average of USD 2.22 million in breach costs compared to those that did not. These technologies enhance threat detection, reduce response times, and support prevention strategies such as red-teaming and posture management.
- One Identity reports that 80% of organizations believe improved identity and access management could have prevented some or all of the cyberattacks they experienced. This emphasizes how central IAM has become to building effective cybersecurity defenses.
- According to Mimecast, 97% of 1,700 IT professionals reported being targeted by phishing emails within the past year, and 75% noted a rise in email-based threats. Additionally, 59% say attacks have grown more sophisticated, suggesting phishing remains a leading entry point for attackers.
- Microsoft observed an average of 156,000 daily attempts of business email compromise over the course of a year, illustrating the persistent and large-scale nature of phishing and impersonation attacks targeting enterprise users.
- Arctic Wolf reports that 48% of organizations now see ransomware as their top concern, with 42% having already experienced a ransomware attack in the past year. In another CyberArk survey, 89% of organizations stated they were targeted by ransomware, highlighting the scale of this threat. IBM states that breaches stemming from compromised credentials or insider threats take the longest to contain, with an average time to identify and resolve at 328 and 308 days, respectively. These prolonged breach durations increase exposure and potential financial losses.
- CrowdStrike again notes that identity-based attacks account for 80% of cyber threats, underlining the critical need for robust identity security solutions to guard against widespread credential misuse and lateral movement.
- According to Microsoft, password-based attacks surged to ten times their previous levels over the past year, signaling a growing reliance by attackers on stolen or weak credentials as a gateway into enterprise systems.
Market Dynamic
Driving Factors in the Identity & Access Management Market
Rise in Cybersecurity Threats and Data Breaches
As cyberattacks become more frequent and advanced, organizations are under pressure to secure their digital environments. Hackers often target user credentials to gain unauthorized access to systems, which can lead to data theft, financial losses, and reputational damage. Identity & Access Management (IAM) helps minimize this risk by controlling and monitoring who can access what data and when.
The ability to detect unusual login patterns and block unauthorized users is vital in stopping attacks before they cause harm. As a result, companies across all industries are investing more in IAM tools to strengthen their security posture. The growing number of high-profile data breaches has made IAM a top priority for IT teams and business leaders alike. This constant threat landscape is pushing steady demand in the IAM market.
Shift to Cloud Services and Remote Work
The global transformation to cloud computing and remote work has changed how companies manage access to their systems. Employees, contractors, and partners now need secure access to applications from different devices and locations. Traditional security models, which depend on in-office networks, no longer work in this flexible environment. IAM provides the tools to manage access rights consistently across cloud and on-premise systems.
Features like single sign-on, multi-factor authentication, and identity federation help keep systems secure without making access difficult. As companies adopt more cloud services and support remote teams, IAM becomes a key part of their IT infrastructure. This shift is mainly strong among small and mid-sized businesses moving to digital platforms. The need for secure, easy, and flexible identity control is driving strong growth in the IAM market.
Restraints in the Identity & Access Management Market
High Implementation Costs and Complexity
One of the biggest challenges in adopting Identity & Access Management (IAM) systems is the high cost of implementation. Setting up a full IAM solution often requires investment in software, hardware, integration, and staff training. For many small and mid-sized businesses, these expenses can be difficult to justify.
In addition, IAM systems can be complex to integrate with existing IT infrastructure, if a company uses a mix of old and new technologies. The process can take time and may require external experts, further increasing costs. This complexity can lead to delays or incomplete setups, limiting the effectiveness of the IAM system. As a result, some organizations are hesitant to fully adopt IAM tools, slowing down overall market growth.
Lack of Skilled Professionals and Awareness
The Identity & Access Management market faces a shortage of skilled professionals who understand both cybersecurity and IAM system management. IAM involves not only technical knowledge but also careful planning to align with business goals and compliance needs. Many companies struggle to find or train employees with the right expertise, which can lead to poor system setup and increased risks.
Additionally, some businesses still lack awareness of IAM's importance or assume that basic password controls are enough. This limited understanding means that IAM solutions may not be used to their full potential or are skipped altogether. The gap in talent and awareness can hold back wider adoption of IAM, especially in regions or industries with fewer IT resources.
Opportunities in the Identity & Access Management Market
Growing Demand for Cloud-Based IAM Solutions
As businesses continue to move their operations to the cloud, there is a growth in the demand for cloud-native Identity & Access Management (IAM) solutions. Cloud-based IAM offers flexibility, scalability, and lower upfront costs, making it ideal for organizations of all sizes. These solutions can easily integrate with popular cloud platforms, allowing secure access across multiple services and applications. They also help remote workforces by allowing secure login from any location or device.
The increasing adoption of Software-as-a-Service (SaaS) applications further boosts the demand for IAM tools that work seamlessly in cloud environments. Vendors offering user-friendly, cloud-compatible IAM solutions are well-positioned to capture a larger share of this growing market. This shift to the cloud creates a long-term opportunity for IAM providers.
Adoption of Advanced Technologies Like AI and Biometrics
The integration of technologies like
artificial intelligence (AI), machine learning, and biometrics into IAM systems presents a major growth opportunity. AI can improve IAM by identifying suspicious behavior, automating responses to threats, and making access decisions smarter and faster. Biometrics, like fingerprint or facial recognition, offer a secure and convenient alternative to traditional passwords, enhancing both security and user experience. These advanced features help organizations build a more proactive and adaptive identity management system.
As cyber threats become more sophisticated, demand is growing for IAM solutions that can intelligently respond to risks in real time. Companies investing in these cutting-edge capabilities can meet customer needs and gain a competitive advantage. The evolving tech landscape opens the door for innovation in the IAM market.
Trends in the Identity & Access Management Market
Integration of Artificial Intelligence and Machine Learning in IAM
The Identity & Access Management (IAM) landscape is highly embracing artificial intelligence (AI) and
machine learning (ML) to enhance security measures. These technologies allow IAM systems to analyze user behaviors, detect anomalies, and respond to potential threats in real-time. By automating tasks like user provisioning and access certification, AI and ML not only enhance efficiency but also bolster security by identifying suspicious activities promptly, which allows organizations to implement personalized access controls customized to individual user behaviors, thereby strengthening defenses against potential security breaches.
As AI and ML technologies constantly evolve, their integration into IAM systems is expected to become more specialized, offering predictive capabilities that anticipate and counter emerging threats, which highlights the transformation towards more intelligent and adaptive IAM solutions that can keep pace with the dynamic cybersecurity landscape.
Adoption of Zero Trust Security Models
The adoption of Zero Trust security models is gaining momentum within the IAM market. This approach operates on the principle of "never trust, always verify," requiring constant authentication and authorization of users and devices, regardless of their location within or outside the network perimeter. By implementing Zero Trust architectures, organizations can enforce granular access controls and minimize the risk of unauthorized access, which is particularly effective in mitigating insider threats and protecting against lateral movement by attackers within a network.
The emphasis on constant verification and the assumption that every access attempt could be a potential threat are driving organizations to integrate Zero Trust principles into their IAM strategies. As cyber threats become more sophisticated, the Zero Trust model offers a robust framework for enhancing security posture and ensuring that access to resources is granted based on strict verification processes.
Research Scope and Analysis
By Component Analysis
Solutions will lead the Identity & Access Management market in 2025, capturing a share of 59.6%, as it is driven by the growing need for robust security measures as businesses face rising cyber threats and regulatory pressures. IAM solutions, which include tools for authentication, access control, and identity verification, are vital for protecting sensitive data and ensuring compliance with privacy regulations. As organizations move to the cloud and support more remote work, these solutions become essential for managing secure access across multiple platforms. The demand for user-friendly, automated, and scalable IAM solutions is expected to continue increasing, driving further growth in the market.
Services in IAM are experiencing significant growth over the forecast period, as organizations look for expert support to deploy, manage, and optimize their IAM systems. Consulting, integration, and support services are crucial for businesses to effectively implement IAM solutions and maintain security. As technology evolves and cyber threats become more sophisticated, services like managed security and continuous monitoring are in high demand. These services help businesses stay compliant with regulations while improving operational efficiency. The growing complexity of IT environments also pushes the need for specialized services, contributing to the overall expansion of the IAM market.
By Deployment Mode Analysis
Cloud will lead the Identity & Access Management (IAM) market in 2025, holding a share of 67.9%. The cloud deployment mode offers businesses flexibility, scalability, and cost-effectiveness, making it the preferred choice for many organizations. As companies majorly shift to cloud-based platforms, IAM solutions in the cloud are vital for managing secure access to a wide range of applications and services. Cloud IAM allows organizations to implement advanced security features, like multi-factor authentication and real-time monitoring, without the burden of maintaining expensive infrastructure. With more employees working remotely and businesses relying on cloud services, the need for cloud-based IAM solutions will constantly rise, driving significant market growth.
On-premises deployment mode in IAM is seeing notable growth over the forecast period as businesses with strict data privacy concerns or regulatory requirements prefer to maintain control over their systems. On-premises solutions allow organizations to customize their IAM tools to fit specific needs while keeping sensitive data within their infrastructure. While cloud solutions are gaining popularity, on-premises systems provides more control and are suited for industries like finance or government that handle highly sensitive information. This preference for security and control in certain sectors is contributing to the ongoing growth of on-premises IAM deployments in the market.
By Solution Type Analysis
Identity lifecycle management will dominate the Identity & Access Management (IAM) market in 2025 with a 39.6% share, due to the growing need to manage user identities across their entire journey within an organization. From onboarding and access provisioning to role changes and offboarding, identity lifecycle management helps businesses ensure that users have the right access at the right time—no more, no less. This solution type supports automation and governance, reducing errors and improving security.
As companies grow and handle more users across multiple systems, tracking and controlling access manually becomes difficult. Identity lifecycle tools simplify this process, supporting organizations to stay compliant, minimize risks, and boost operational efficiency. With growth in data security concerns and regulatory demands, businesses are prioritizing identity lifecycle management as a key part of their digital security strategy.
Further, Authentication as a solution type is experiencing strong growth over the forecast period as organizations focus on verifying user identities before granting access. With cyberattacks and identity theft on the rise, businesses are turning to secure login methods like biometrics, one-time passwords, and multi-factor authentication. These tools add extra layers of protection and help reduce the risk of unauthorized access. Authentication solutions also improve user experience by offering faster, more convenient ways to log in across devices and platforms. As companies constantly adopt cloud services and remote work models, reliable authentication has become a top priority. The demand for stronger, smarter, and simpler identity verification methods is fueling growth in this segment of the IAM market.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
By Organization Type Analysis
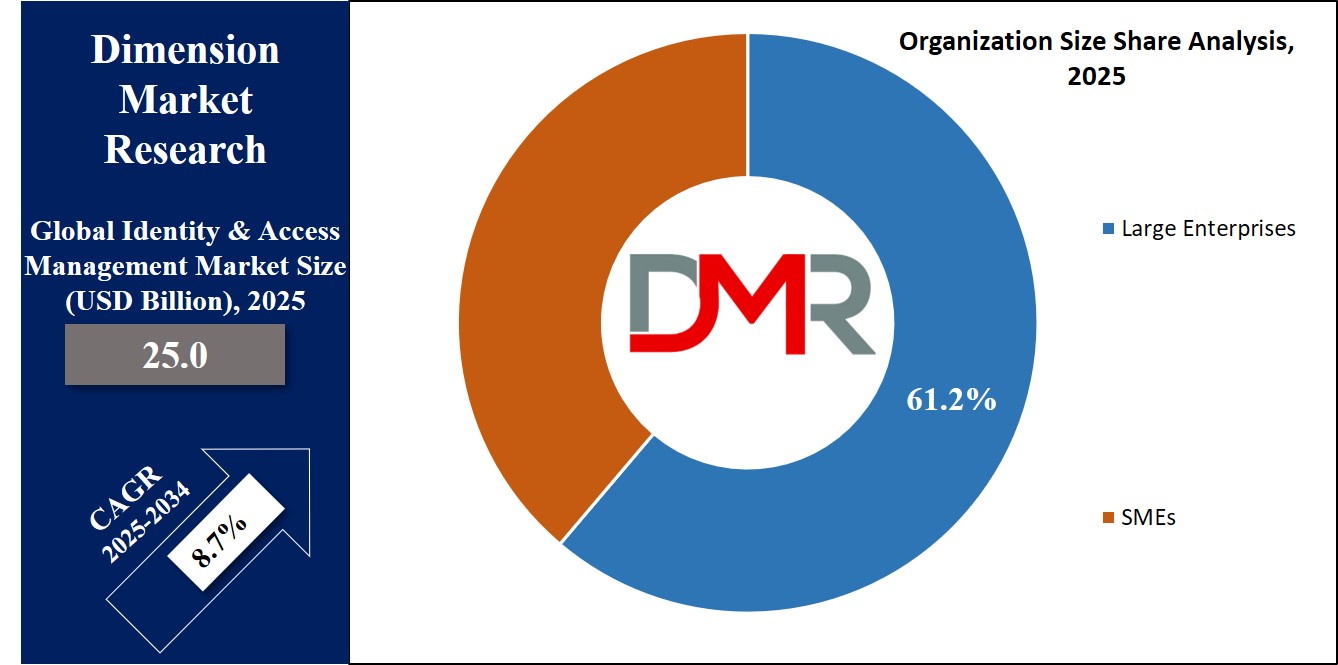
Large enterprises are set to be prominent in the Identity & Access Management (IAM) market in 2025, holding a
61.2% share due to their complex IT systems, high user volumes, and strict compliance needs. These organizations often manage thousands of employees, vendors, and customers, making secure and efficient identity control essential. IAM helps large businesses automate access rights, monitor user behavior, and reduce risks tied to human error or internal threats. With multiple departments and systems, large enterprises rely on IAM to ensure that only authorized users can access sensitive information.
Growing concerns over data breaches and strict global regulations have pushed these organizations to invest heavily in IAM tools. As digital operations expand and cloud adoption rises, large enterprises continue to drive strong demand for scalable, flexible, and secure IAM solutions to protect their assets and maintain business continuity.
In addition, SMEs are set to show significant growth over the forecast period in the Identity & Access Management market as they increasingly recognize the need to protect digital assets and manage user access efficiently. With the growth of cloud adoption and remote work, small and medium-sized businesses are facing similar cybersecurity challenges as larger firms.
IAM solutions help SMEs control who can access what, preventing data leaks and unauthorized entry into systems. These businesses are also looking for cost-effective, easy-to-deploy solutions that require minimal IT staff. As more affordable and user-friendly IAM tools become available, adoption is growing in this segment. Regulatory compliance needs and customer data protection are also pushing SMEs to invest in reliable IAM systems, supporting market growth.
By Authentication Type Analysis
Single-factor authentication will lead the Identity & Access Management (IAM) market in 2025 with a share of 59.4%, mainly due to its simplicity and higher use across various sectors. It typically includes a single method, like a password or PIN, to verify a user’s identity. Many organizations, mainly those with basic access needs or limited resources, still depend on single-factor authentication because it is easy to implement and cost-effective.
Despite growing security concerns, this method continues to dominate due to its familiarity and compatibility with existing systems. It is often used for non-critical applications where high-level security is not required. The ease of use and low complexity make it a preferred option for many businesses. As a result, single-factor authentication continues to play a key role in driving IAM market adoption across a wide range of industries.
Multi-factor authentication is showing strong growth over the forecast period in the Identity & Access Management market as security demands increase. This method combines two or more verification steps, such as passwords, biometrics, or one-time codes, to confirm a user’s identity. With cyberattacks becoming more common and sophisticated, businesses are adding layers of protection to reduce the risk of unauthorized access.
Multi-factor authentication offers higher security than single-factor and is mainly valuable for protecting sensitive systems and data. Organizations across sectors like finance, healthcare, and government are adopting it to meet compliance standards and ensure data privacy. As more users work remotely and access digital platforms, the need for strong, flexible security methods is driving the growing adoption of multi-factor authentication in the IAM market.
By Industry Vertical Analysis
In terms of industry vertical, BFSI will lead the Identity & Access Management (IAM) market in 2025 with a 25.8% share, driven by the need for high-level security, compliance, and fraud prevention. Banks, financial institutions, and insurance companies handle large volumes of sensitive customer data and financial transactions, making them top targets for cyberattacks.
IAM solutions help these organizations control who can access what information and systems, minimizing the risk of unauthorized access or data breaches. Regulatory bodies also require strict identity verification and data protection measures, which further push the adoption of IAM tools. Features like multi-factor authentication, role-based access, and user activity monitoring are critical in this sector. As digital banking grows and more services move online, BFSI companies are heavily investing in IAM systems to protect assets, ensure trust, and meet security standards.
Healthcare is experiencing significant growth in the IAM market as hospitals, clinics, and healthcare providers move toward digital records and telehealth services. With sensitive patient data stored and shared electronically, strong identity and access control has become essential to protect against data breaches and unauthorized use. IAM solutions help manage access to medical records, systems, and devices while ensuring that only authorized staff can view or edit information.
Compliance with regulations like HIPAA is also driving adoption, as organizations must prove they have strong data protection measures in place. As the healthcare sector modernizes and connects more systems digitally, IAM tools are playing a vital role in maintaining security and patient trust while enabling smooth access for medical professionals and staff.
The Identity & Access Management Market Report is segmented based on the following:
By Component
By Deployment Mode
By Solution Type
- Identity Lifecycle Management
- Authentication
- Authorization
- Audit, Compliance, and Governance
- Password Management
- Directory Services
- Access Management
- Privileged Access Management (PAM)
By Organization Size
- Small and Medium Enterprises (SMEs)
- Large Enterprises
By Authentication Type
- Single-Factor Authentication
- Multi-Factor Authentication
By Industry Vertical
- BFSI
- IT & Telecom
- Healthcare
- Government & Public Sector
- Retail & E-commerce
- Energy & Utilities
- Manufacturing
- Education
- Others
Regional Analysis
North America Leading Region in the Identity & Access Management Market
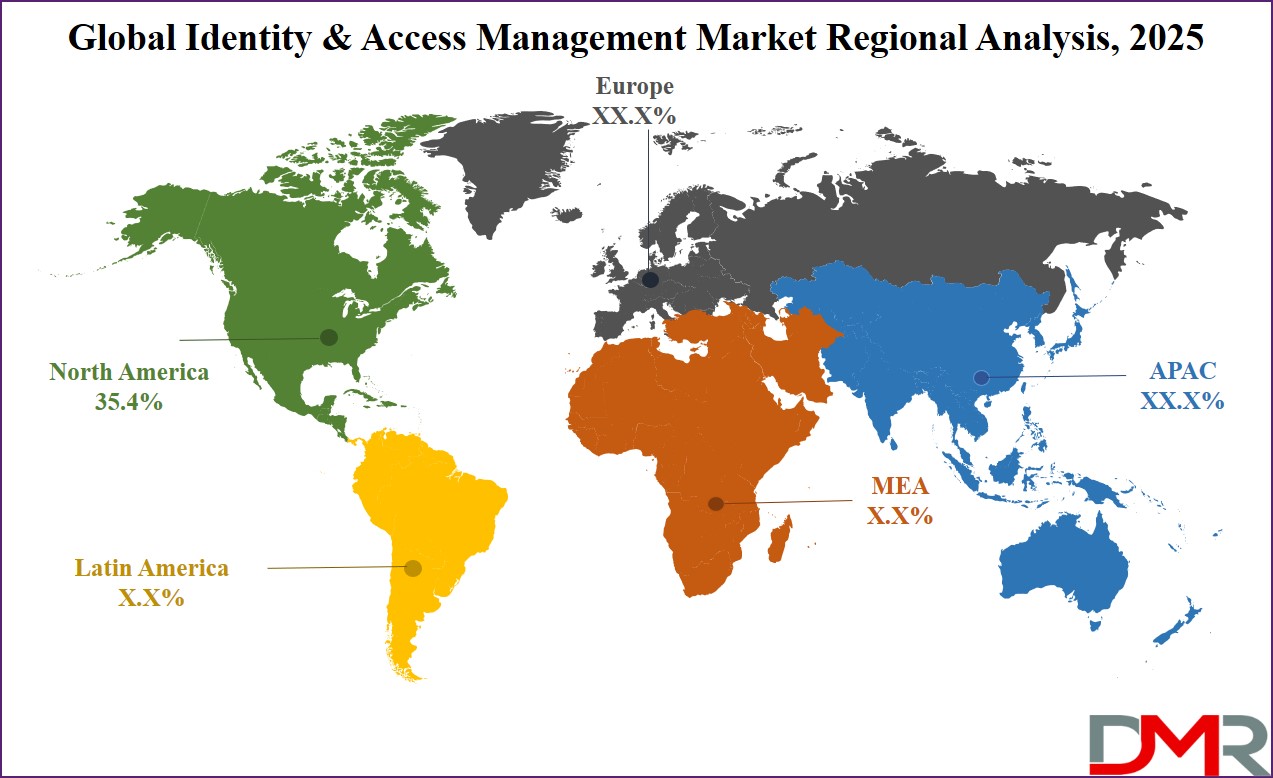
North America will be leading the Identity & Access Management (IAM) market in 2025 with a projected share of
35.4%, driven by early adoption of advanced cybersecurity solutions, strong presence of key technology providers, and strict regulatory requirements. The region’s organizations, mainly in industries like finance, healthcare, and government, are heavily investing in IAM tools to manage user identities, secure sensitive data, and meet compliance standards such as HIPAA, SOX, and CCPA.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
The rapid growth of cloud computing, remote work, and digital services across the US and Canada has increased the need for secure access management. In addition, growing threats from cyberattacks and data breaches are pushing both private and public sectors to upgrade their identity security infrastructure. As IAM solutions become more intelligent and automated, North American companies continue to lead in innovation and adoption, making the region a central force in shaping global IAM market trends throughout 2025 and beyond.
Fastest Growing Region in the Identity & Access Management Market
Asia Pacific is showing significant growth in the Identity & Access Management (IAM) market over the forecast period due to rapid digital transformation, rising cyber threats, and growing awareness of data protection across developing economies. Countries like China, India, Japan, and South Korea are increasing investments in cybersecurity infrastructure and access control systems to safeguard critical information.
The expansion of cloud computing, mobile applications, and remote work has also increased the need for reliable identity governance and user access solutions. Regulatory frameworks focusing on data privacy and security are further encouraging businesses to adopt IAM technologies. With 2025 underway, the region is estimated to continue its strong upward trend as companies seek better identity verification and secure login tools.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Competitive Landscape
The Identity & Access Management (IAM) market is highly competitive and growing fast, with many technology providers offering different tools and solutions. Some focus on helping large businesses manage complex user systems, while others create easier options for smaller companies. These providers compete by offering advanced security features, faster login methods, and easy-to-use dashboards. Many are also moving toward cloud-based services to meet growing demand for remote access and flexible work environments.
Innovation is key, especially in areas like passwordless login, artificial intelligence, and automated user role management. As cyber threats increase, more companies are looking for IAM tools that are both secure and simple to use, which has made the market dynamic, with new features and updates released often.
Some of the prominent players in the global Identity & Access Management are:
- Microsoft
- IBM
- Oracle
- One Identity
- ForgeRock
- Avatier
- OneLogin
- HID Global
- SecureAuth
- Curity
- Optimal IdM
- Centrify
- NetIQ
- Atos
- Bitium
- Janrain
- iWelcome
- Ubisecure
- EmpowerID
- PlainID
- Other Key Players
Recent Developments
- In April 2025, 1Password introduced new features to its platform that secure every sign-in across all apps and devices, including unmanaged ones. These updates boost visibility, control, and automation with extended device compliance, agentic AI security, a unified admin console, and a central app launcher.
- In April 2025, CyberArk launched its Secure AI Agents Solution to help organizations apply identity-first security to agentic AI through the CyberArk Identity Security Platform. As AI agents autonomously interact, access sensitive data, and escalate privileges, the solution addresses emerging identity-related risks. With AI agents forming a new class of digital identities, CyberArk’s end-to-end approach secures their privileged access.
- In March 2025, Axonius introduced Axonius Identities, an advanced solution that combines identity management, governance, and security into a single platform powered by asset intelligence. Launched at the Axonius Adapt conference, the product assists organizations in tackling identity and access challenges by aligning IT and security functions.
- In November 2024, Eviden launched Evidian Orbion, a next-gen Identity-as-a-Service (IDaaS) solution that unifies IGA, AM, and PAM for hybrid environments. Designed for scalability and security, it simplifies identity and access management while supporting regulatory and sovereignty needs. As organizations shift beyond traditional security perimeters, Evidian Orbion enables secure access for employees and partners from anywhere. It minimizes IAM complexity through features like self-enrolment and integration with Identity Proofing tools, making it ideal for mid-market and large enterprises.
- In October 2024, Evo Security, a top identity and access management (IAM) provider for Managed Service Providers (MSPs), launched a major rebrand, enhanced solutions, and new product releases, marking a key step in its growth. The new identity, built around “Managed Security Starts with Identity,” highlights Evo’s focus on unified, modern security.