Market Overview
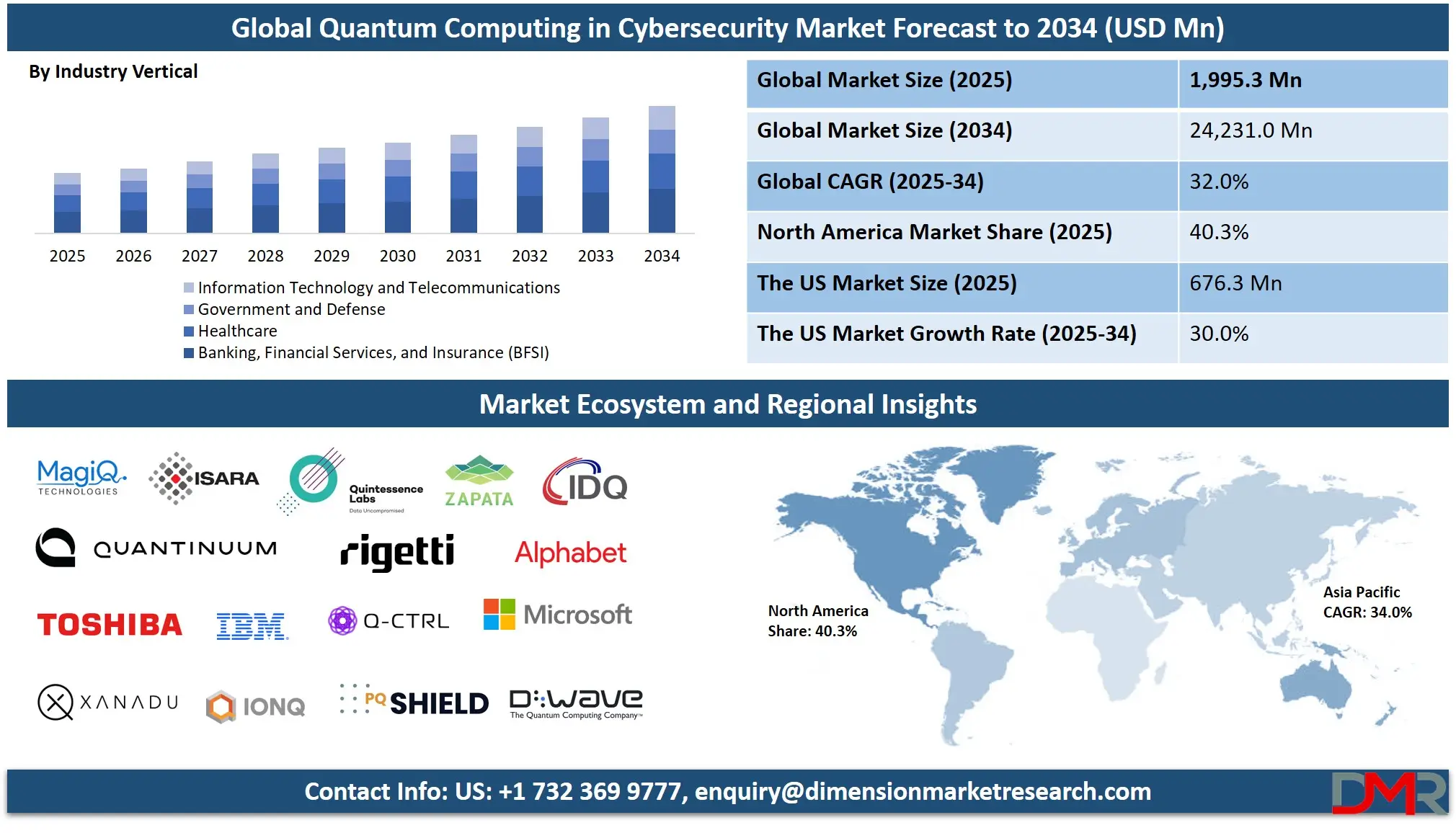
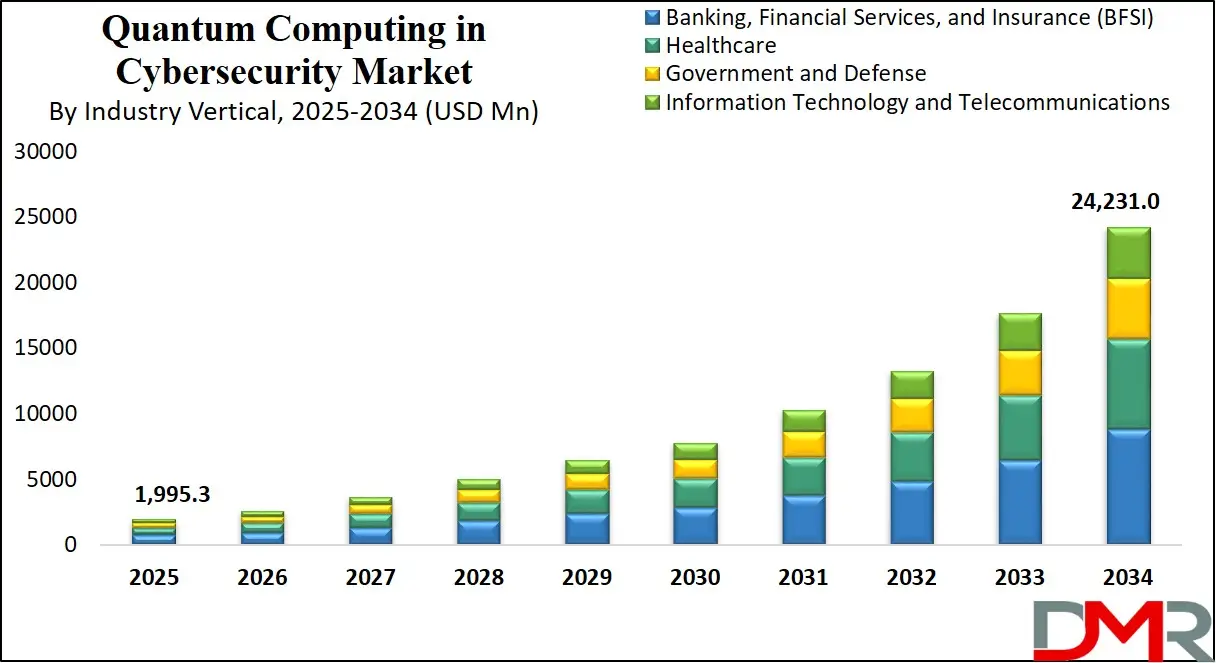
The Global Quantum Computing in Cybersecurity Market is projected to reach USD 1,995.3 million in 2025 and grow at a compound annual growth rate of 32.0% from there until 2034 to reach a value of USD 24,231.0 million.
The global quantum computing in cybersecurity market is rapidly evolving, driven by the pressing need to counteract emerging quantum threats. As quantum computers advance, traditional encryption methods face obsolescence, prompting a shift towards quantum-resistant solutions. This transition is fueled by the potential of quantum computing to solve complex problems, offering both opportunities and challenges in the cybersecurity landscape.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
Key trends include the development of quantum-resistant cryptographic algorithms and the integration of quantum key distribution (QKD) systems. These innovations aim to safeguard data against quantum-enabled breaches. Additionally, the rise of quantum-powered threat detection platforms enhances the ability to identify and mitigate sophisticated cyber threats.
Opportunities abound in sectors like finance, healthcare, and government, where the protection of sensitive information is paramount. The adoption of quantum-secured blockchain solutions also presents a frontier for secure transactions and data integrity. However, the market faces restraints such as high implementation costs and the need for specialized expertise, which can hinder widespread adoption.
This surge is attributed to increased investments in quantum research and the escalating demand for robust cybersecurity measures. As organizations recognize the imperative to future-proof their systems, the quantum computing in cybersecurity market is poised for substantial expansion, marking a pivotal shift in how data security is approached globally.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
The US Quantum Computing in Cybersecurity Market
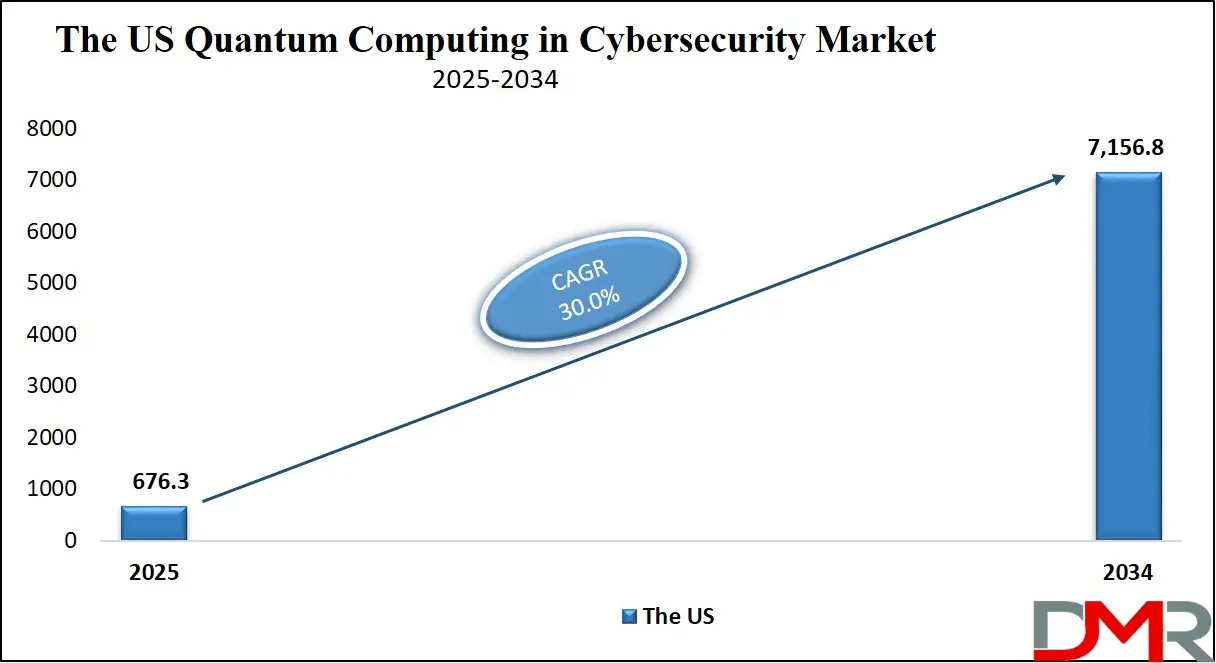
The US Quantum Computing in Cybersecurity Market is projected to reach USD 676.3 million in 2025 at a compound annual growth rate of 30.0% over its forecast period.
The United States is at the forefront of integrating quantum computing into its cybersecurity infrastructure. Recognizing the potential threats posed by quantum advancements, federal agencies have initiated comprehensive strategies to transition to quantum-resistant systems. The Cybersecurity and Infrastructure Security Agency (CISA) has launched the Post-Quantum Cryptography Initiative, aiming to unify efforts across government and industry to address quantum-related cybersecurity challenges.
The National Institute of Standards and Technology (NIST) is actively developing new cryptographic standards to replace vulnerable public-key algorithms. This proactive approach ensures that critical infrastructure and government networks are prepared for the quantum era.
Demographically, the U.S. boasts a robust ecosystem of research institutions, tech companies, and a skilled workforce dedicated to quantum technologies. Cities like Boston, Chicago, and Chattanooga are emerging as quantum hubs, fostering innovation and collaboration between academia and industry.
However, challenges persist. A report by the Government Accountability Office (GAO) highlights gaps in leadership and strategy, emphasizing the need for a cohesive national approach to quantum cybersecurity. Addressing these issues is crucial to maintaining the nation's competitive edge and ensuring the security of its digital infrastructure.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
The European Quantum Computing in Cybersecurity Market
The European Quantum Computing in Cybersecurity Market is estimated to be valued at USD 299.3 million in 2025 and is further anticipated to reach USD 1,792.0 million by 2034 at a CAGR of 22.0%.
Europe is making significant strides in quantum computing, particularly in its application to cybersecurity. The European Union has identified quantum technologies as a strategic priority, investing heavily in research and development to bolster digital sovereignty.
The European Commission's Quantum Flagship initiative exemplifies this commitment, aiming to position Europe as a leader in quantum research. By fostering collaboration among member states, academia, and industry, the EU seeks to develop quantum-resistant cryptographic solutions to safeguard its digital infrastructure.
Europe's demographic advantage lies in its highly educated workforce and a strong network of research institutions. Countries like Germany, France, and the Netherlands are home to leading quantum research centers, contributing to a vibrant innovation ecosystem.
Despite these strengths, Europe faces challenges in translating research into commercial applications. The European Cyber Security Organisation (ECSO) emphasizes the need for increased investment in cybersecurity startups and the development of a unified market strategy to accelerate the adoption of quantum technologies.
In summary, Europe's concerted efforts in quantum computing and cybersecurity position it as a formidable player on the global stage. Continued investment and strategic coordination will be key to harnessing the full potential of quantum technologies in securing Europe's digital future.
The Japan Quantum Computing in Cybersecurity Market
The Japan Quantum Computing in Cybersecurity Market is projected to be valued at USD 79.8 million in 2025. It is further expected to witness subsequent growth in the upcoming period, holding USD 736.1 million in 2034 at a CAGR of 28.0%.
Japan is actively advancing its quantum computing capabilities, recognizing the technology's potential to revolutionize cybersecurity. The government has outlined a comprehensive strategy to develop quantum encryption technologies by 2030, aiming to counter emerging cyber threats.
This initiative involves collaboration with leading corporations such as Toshiba and NEC, leveraging their expertise to accelerate research and development. The focus is on creating practical applications of quantum technologies to enhance data security across various sectors.
Japan's demographic advantage includes a highly skilled workforce and a strong foundation in technological innovation. The country's emphasis on education and research has cultivated a talent pool capable of driving advancements in quantum computing.
However, challenges remain. The complexity of quantum technologies and the need for substantial investment pose hurdles to rapid implementation. To address this, Japan is fostering public-private partnerships and increasing funding for quantum research initiatives.
In conclusion, Japan's proactive approach to integrating quantum computing into its cybersecurity framework underscores its commitment to maintaining technological leadership. By investing in research, fostering collaboration, and leveraging its skilled workforce, Japan is well-positioned to navigate the challenges and opportunities presented by the quantum era.
Global Quantum Computing in Cybersecurity Market: Key Takeaways
- Global Market Size Insights: The Global Quantum Computing in Cybersecurity Market size is estimated to have a value of USD 1,995.3 million in 2025 and is expected to reach USD 24,231.0 million by the end of 2034.
- The US Market Size Insights: The US Quantum Computing in Cybersecurity Market is projected to be valued at USD 676.3 million in 2025. It is expected to witness subsequent growth in the upcoming period as it holds USD 7,156.8 million in 2034 at a CAGR of 30.0%.
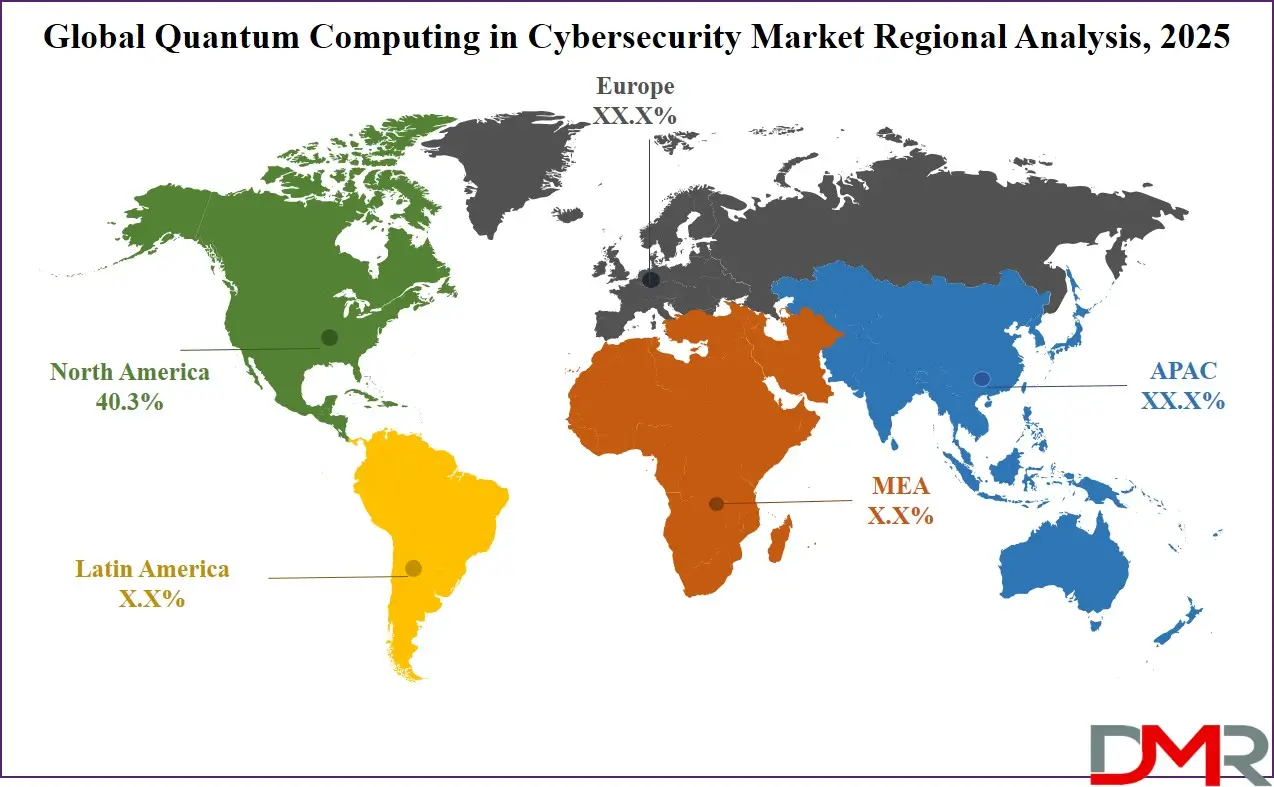
- Regional Insights: North America is expected to have the largest market share in the Global Quantum Computing in Cybersecurity Market with a share of about 40.3% in 2025.
- Key Players: Some of the major key players in the Global Quantum Computing in Cybersecurity Market are IBM, Microsoft, Google (Alphabet Inc.), D-Wave Systems, Rigetti Computing, IonQ, Quantinuum, Xanadu, Atos SE, Toshiba Corporation, ID Quantique, QuintessenceLabs, and many others.
- The Global Market Growth Rate: The market is growing at a CAGR of 32.0 percent over the forecasted period of 2025.
Global Quantum Computing in Cybersecurity Market: Use Cases
- Quantum-Resistant Cryptography: Organizations are implementing algorithms designed to withstand quantum attacks, ensuring long-term data confidentiality and integrity in the face of evolving computational threats.
- Quantum Key Distribution (QKD): Financial institutions utilize QKD to establish secure communication channels, leveraging quantum mechanics to detect eavesdropping and prevent data interception.
- Quantum-Powered Threat Detection: Cybersecurity firms employ quantum-enhanced machine learning to analyze vast datasets, enabling the early detection of anomalies and potential cyber threats.
- Quantum-Secured Blockchain: Supply chain companies adopt quantum-secured blockchain technologies to ensure tamper-proof transaction records, enhancing transparency and trust.
- Secure Government Communications: Defense agencies integrate quantum encryption methods to protect sensitive communications, safeguarding national security interests against advanced cyber espionage.
Global Quantum Computing in Cybersecurity Market: Stats & Facts
National Institute of Standards and Technology (NIST)
- Post-Quantum Cryptography Standards Finalized: In 2024, NIST completed the development of the first set of quantum-resistant encryption algorithms to safeguard digital communications. These algorithms are designed to replace public-key cryptographic systems that could be compromised by quantum computers.
- Urgent Implementation Guidance: NIST strongly encourages organizations and government bodies to begin planning for cryptographic transition today, as retrofitting secure systems later could be time-consuming and costly.
- Clarification of PQC Definition: NIST emphasizes that post-quantum cryptography (PQC) is not reliant on quantum physics but instead based on hard mathematical problems (like lattice-based cryptography), making it practical and scalable for immediate deployment.
Cybersecurity and Infrastructure Security Agency (CISA)
- Post-Quantum Cryptography Initiative: CISA established a formal framework to coordinate with interagency and private-sector stakeholders to prepare critical infrastructure for quantum threats.
- Four-Pillar Framework:
- Risk Assessment: Evaluate current encryption vulnerabilities to quantum threats.
- Strategic Planning: Develop roadmaps for cryptographic migration.
- Stakeholder Engagement: Facilitate cross-sector communication and education.
- Implementation: Initiate technical transitions to quantum-safe systems.
- Strategic Warnings: CISA warns that sectors such as energy, healthcare, and transportation will be particularly vulnerable unless proactive measures are taken.
Government Accountability Office (GAO)
- Quantum Timeline Forecast: GAO reports that experts believe quantum computers capable of breaking current encryption could emerge between 2030 and 2040, creating a critical window for preparedness.
- “Harvest Now, Decrypt Later” Threat: The GAO explains that adversaries may be collecting encrypted data now to decrypt it when quantum computing becomes powerful enough, jeopardizing long-term confidentiality.
- Federal Risk Report: Urges all federal agencies to initiate comprehensive cryptographic system inventories to understand where quantum-vulnerable encryption is currently in use.
National Security Agency (NSA)
- Guidance Against QKD: The NSA does not endorse Quantum Key Distribution (QKD) for securing National Security Systems due to concerns around scalability, bandwidth inefficiency, and lack of interoperability with modern infrastructure.
- Prioritization of Post-Quantum Algorithms: The agency recommends focusing national resources on developing and deploying quantum-resistant algorithms, particularly those standardized by NIST.
U.S. Department of Homeland Security (DHS)
- Quantum Technology’s Transformative Potential: DHS recognizes quantum computing as a transformative technology that could disrupt encryption and authentication mechanisms, potentially impacting government, finance, and defense sectors.
- Migration Assistance: DHS is working with federal IT leadership to coordinate inventory management, risk prioritization, and procurement strategies for quantum-safe technologies.
U.S. Customs and Border Protection (CBP)
- Early PQC Adoption: CBP is piloting the implementation of post-quantum cryptography in its communication and operational systems, aiming to stay ahead of potential cryptographic disruptions.
- Security-First Approach: CBP emphasizes that securing sensitive data such as passenger records and trade documentation is essential, and PQC can provide the necessary protection in the coming decades.
U.S. Department of the Treasury
- G7 Cyber Expert Group Recommendations: Treasury's work with the G7 emphasizes the need for financial institutions to:
- Monitor quantum advancements.
- Conduct cryptographic risk assessments.
- Design transition roadmaps toward quantum-safe systems.
- Sector-Wide Risk Recognition: The department underscores that financial institutions are especially susceptible due to long-term data confidentiality requirements, such as customer records and transaction logs.
National Quantum Initiative (quantum.gov)
- National-Level Coordination: Established under the National Quantum Initiative Act, this body coordinates investments across academia, national labs, and industry to accelerate the U.S. lead in quantum innovation.
- Cross-Agency Collaboration: Works in tandem with NIST, DOE, NSF, and DoD to ensure quantum advancements are linked with cybersecurity strategy.
- Education and Workforce Development: Also invests in training programs to build a new generation of quantum-capable cybersecurity professionals.
U.S. Congress
- Quantum Computing Cybersecurity Preparedness Act: This law mandates federal agencies to inventory all cryptographic systems, assess vulnerabilities, and submit migration plans to Congress.
- Legislative Mandates:
- Prepare detailed timelines for cryptographic transition.
- Collaborate with NIST on standards implementation.
- Secure funding for cryptographic modernization initiatives.
Pacific Northwest National Laboratory (PNNL)
- Algorithmic Innovation: Scientists at PNNL developed a new algorithm that drastically reduces the data preparation steps needed for quantum computing models, making cybersecurity simulations faster and more efficient.
- Impact on Security Research: This advancement enhances the lab’s ability to simulate quantum attacks on encrypted systems, allowing preemptive strengthening of digital infrastructure.
Global Quantum Computing in Cybersecurity Market: Market Dynamics
Driving Factors in the Global Quantum Computing in Cybersecurity Market
Increasing Government Funding and Regulatory Push for Quantum-Safe Infrastructure
Government funding and regulatory directives are emerging as dominant growth drivers in the quantum cybersecurity ecosystem. Public sector bodies across the U.S., Canada, Germany, Japan, and Australia have launched dedicated national strategies, allocating billions toward quantum computing research with cybersecurity preparedness as a primary component. The U.S. Quantum Initiative Act and the Quantum Computing Cybersecurity Preparedness Act are pivotal policies requiring all federal agencies to inventory existing cryptographic systems and transition toward post-quantum standards within defined timelines. Similarly, the European Union has established programs like Horizon Europe and the Digital Europe Programme to support quantum communication infrastructure and post-quantum cryptographic algorithm development.
These legislative and fiscal actions are compelling both government agencies and private contractors to upgrade their encryption protocols and deploy quantum-safe technologies. Defense and intelligence sectors, in particular, are accelerating quantum-resistant architecture adoption in mission-critical networks. This regulatory momentum is driving enterprise-level investment in hybrid cryptographic solutions and crypto-agility frameworks, where organizations can pivot rapidly to newer algorithms as threats evolve. Such governance-backed demand is also encouraging start-ups and scale-ups to commercialize quantum cybersecurity tools faster, supported by innovation grants, pilot programs, and R&D tax credits. As quantum threat awareness grows, so does the market pull for compliance-ready, NIST-approved, and government-certified encryption technologies.
Rising Threat of "Harvest Now, Decrypt Later" Tactics
The increasing awareness around “Harvest Now, Decrypt Later” (HNDL) strategies is significantly propelling the demand for quantum-resistant cybersecurity solutions. In this exploit model, cyber adversaries especially state-sponsored actors intercept and store encrypted sensitive data today, to decrypt it in the near future using quantum computing power. With quantum decryption projected to be viable within the next 10–20 years, this tactic poses an existential threat to sectors where long-term confidentiality is vital, such as banking, healthcare, defense, and critical infrastructure. Organizations are recognizing that data breaches executed now can have damaging repercussions well into the future, especially for data subject to regulatory compliance, such as medical records under HIPAA or classified intelligence data.
This looming threat is pushing chief information security officers (CISOs) to prioritize quantum-resilient encryption in procurement and IT roadmaps. Moreover, insurance providers and legal advisors are revising cyber liability policies and data retention frameworks to factor in potential future decryption risks. Companies are increasingly deploying hybrid security models that incorporate both classical and post-quantum encryption layers, creating a phased approach to risk mitigation. This anticipation of quantum attacks is fundamentally shifting cybersecurity from reactive to proactive, ensuring long-term data protection against evolving threats and thus catalyzing significant market growth.
Restraints in the Global Quantum Computing in Cybersecurity Market
High Cost and Technical Complexity of Deployment
The high cost and technical complexity involved in deploying quantum-resistant cybersecurity solutions pose a significant restraint on market growth. Implementing quantum-safe protocols requires overhauling existing cryptographic infrastructure, which can be deeply embedded across applications, databases, and network layers. The transition demands skilled cryptographers, security architects, and systems engineers who can manage hybrid environments where classical and post-quantum algorithms coexist. Moreover, quantum technologies like QKD require expensive hardware, including single-photon sources, quantum random number generators, and specialized fiber or satellite links, cost-prohibitive for small and medium-sized enterprises (SMEs).
Even software-based post-quantum algorithms involve computational overhead that can degrade system performance, especially on legacy hardware. Additionally, uncertainty around final standards, algorithm acceptance, and regulatory timelines makes companies hesitant to invest in solutions that may become obsolete or require further adaptation. This risk-averse behavior slows innovation cycles and delays commercial deployments. Vendor-side challenges include product interoperability, testing complexity, and scalability constraints. As a result, the high financial and technical barriers limit early-stage adoption, especially in low-margin sectors like education or agriculture. Without substantial subsidies, training, or standardized deployment toolkits, quantum cybersecurity solutions may remain concentrated among large enterprises and government institutions, creating an uneven landscape of security preparedness.
Limited Global Consensus and Standard Harmonization
A critical restraint for the global quantum cybersecurity market is the lack of universal consensus and standard harmonization for post-quantum cryptographic implementations. While the U.S. (via NIST), Europe (through ETSI), and China are all progressing rapidly in defining post-quantum algorithms and protocols, there is fragmentation in approaches, interoperability norms, and deployment timelines. This divergence creates confusion among enterprises and national agencies when choosing technologies that align with both domestic policies and international trade standards. For multinational corporations, this raises legal and operational concerns about data sovereignty, encryption export controls, and cross-border interoperability.
Furthermore, different algorithm preferences across regions, such as lattice-based cryptography in the U.S. versus code-based systems favored in parts of Asia, lead to software and hardware compatibility issues. These gaps hinder collaborative cybersecurity frameworks and delay mass adoption. Additionally, smaller countries and developing economies lack the institutional frameworks and technical expertise to participate in standard-setting, further widening the digital divide. Without synchronized global guidance, vendors face regulatory ambiguity, and enterprises face uncertainty in long-term strategic planning. Until international cooperation strengthens and cross-border harmonization accelerates, the market will experience fragmented growth, underutilized solutions, and missed opportunities for unified cyber defense readiness.
Opportunities in the Global Quantum Computing in Cybersecurity Market
Integration of Quantum-Safe Protocols in Cloud Infrastructure
The integration of quantum-safe cryptographic solutions into mainstream cloud infrastructure presents one of the most significant growth opportunities for the cybersecurity market. Major cloud service providers such as AWS, Microsoft Azure, and Google Cloud are actively exploring post-quantum cryptography (PQC) integration within their services, ranging from data storage to identity and access management. As cloud adoption accelerates globally across sectors like fintech, healthcare, and government services, ensuring data-at-rest and data-in-transit protection from future quantum threats is becoming paramount. This creates a substantial addressable market for cloud-native PQC toolkits, key management systems, and hybrid cryptographic modules.
Vendors offering API-based PQC integration, centralized certificate management, and seamless transition layers are poised to benefit. Moreover, the emergence of confidential computing and secure enclaves offers a complementary base for quantum-safe innovations, providing multi-layered data protection. Enterprises migrating to multi-cloud and hybrid-cloud setups are also seeking scalable encryption solutions that are future-proof and standards-compliant. Regulatory alignment from NIST, CISA, and ISO further drives cloud players to embed post-quantum capabilities, ensuring legal and operational readiness. The cloud’s centrality in global IT architecture positions it as a natural launchpad for widespread PQC adoption, unlocking a multibillion-dollar revenue stream for vendors offering plug-and-play quantum cybersecurity integrations.
Expansion of Quantum-Secured Blockchain Systems
The intersection of blockchain technology and quantum cybersecurity is emerging as a lucrative growth area, particularly through the development of quantum-secured blockchain systems. Traditional blockchain relies heavily on public-key cryptographic mechanisms like ECDSA and SHA-256, which are susceptible to quantum attacks such as Shor’s algorithm. As blockchain adoption surges across decentralized finance (DeFi), supply chain transparency, voting systems, and digital identity management, ensuring cryptographic robustness becomes critical. This has led to the rise of quantum-resistant blockchain protocols, such as lattice-based digital signatures and zero-knowledge proofs that withstand quantum decryption attempts.
Several startups and research consortia are actively designing Layer-1 blockchains with built-in quantum-safe protocols, attracting venture capital and institutional backing. Additionally, central banks exploring Central Bank Digital Currencies (CBDCs) are embedding quantum security layers from the design phase to future-proof monetary systems. Cross-chain interoperability platforms and crypto wallets are also evolving to support hybrid post-quantum key infrastructure (PKI), ensuring secure onboarding and transaction verification. As organizations transition to web3 frameworks, quantum-secured blockchain not only protects digital assets but also builds user trust and regulatory credibility. This evolution creates a high-margin, innovation-driven opportunity for cybersecurity vendors to deliver end-to-end quantum-proof blockchain security solutions, accelerating both adoption and revenue potential.
Trends in the Global Quantum Computing in Cybersecurity Market
Rapid Standardization of Post-Quantum Cryptography (PQC)
A major trend transforming the quantum cybersecurity market is the accelerated standardization of post-quantum cryptographic protocols, spearheaded by the National Institute of Standards and Technology (NIST). As quantum computing edges closer to practical utility, the vulnerability of current public-key encryption schemes, such as RSA and ECC, has become a critical concern. NIST’s formal selection and standardization of PQC algorithms have signaled a shift in industry preparedness, prompting organizations, governments, and infrastructure operators to integrate quantum-resistant protocols across networks. This standardization is not only shaping the R&D efforts of cybersecurity vendors but also influencing procurement, risk governance, and compliance policies globally.
It’s fostering greater collaboration among academic institutions, federal agencies, and technology companies, who are now jointly testing algorithms for interoperability and resilience. Countries such as the U.S., Canada, Germany, and Japan are also launching national transition strategies based on these standards, boosting the international alignment. As vendors move toward hybrid cryptographic systems combining classical and post-quantum algorithms the demand for forward-compatible solutions is accelerating. This trend is establishing PQC as a new benchmark in cybersecurity resilience, driving investments into crypto-agile hardware, software toolkits, and managed service frameworks, thereby expanding the market ecosystem for quantum-secure products and services.
Emergence of Quantum Key Distribution (QKD) Networks
The adoption of Quantum Key Distribution (QKD) technologies is becoming a prominent trend within the cybersecurity domain, driven by demand for ultra-secure communication frameworks. QKD leverages quantum mechanics principles to securely transmit cryptographic keys, making it theoretically immune to both classical and quantum attacks. This technology is gaining traction, particularly in sectors like defense, critical infrastructure, and financial services, where zero-trust environments and high-value data exchange are common. Nation-states such as China, the U.S., and European Union members have initiated large-scale QKD trials, including intercity fiber-based systems and satellite-enabled quantum communication links. For instance, China’s "Quantum Experiments at Space Scale" (QUESS) project and the EU’s EuroQCI initiative are laying the groundwork for secure quantum communication infrastructure.
Companies are responding by developing integrated QKD modules with enhanced key refresh rates and compatibility with existing IPsec/VPN systems. Moreover, hybrid QKD systems that complement post-quantum cryptographic methods are emerging, offering dual-layer protection. While QKD remains capital-intensive and infrastructure-dependent, declining costs of single-photon emitters and detectors are enhancing its commercial viability. As regulatory bodies and governments evaluate QKD’s role in future security architectures, the trend is expected to drive innovations in quantum networking, leading to dedicated QKD-as-a-service models and specialized secure transport layers, thereby expanding market breadth.
Global Quantum Computing in Cybersecurity Market: Research Scope and Analysis
By Solution Type Analysis
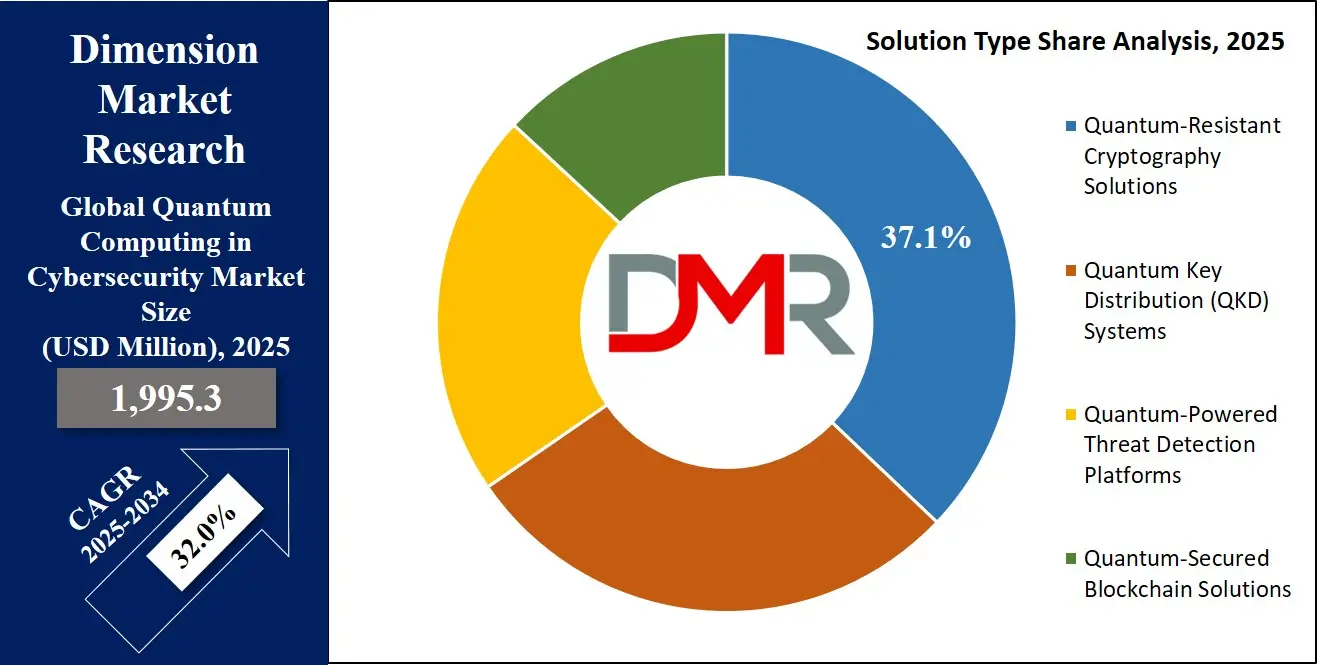
Quantum-Resistant Cryptography (QRC) solutions are projected to dominate the Quantum Computing in Cybersecurity Market due to their immediate relevance, broad applicability, and alignment with global regulatory initiatives. As quantum computers inch closer to practical use, the threat they pose to classical cryptographic protocols like RSA, ECC, and DH becomes increasingly tangible. QRC addresses this core vulnerability by offering algorithmic replacements that can resist decryption by quantum algorithms such as Shor’s and Grover’s. These post-quantum cryptographic methods including lattice-based, hash-based, and multivariate polynomial cryptography are designed to be implemented using current digital infrastructure, making them far more accessible and deployable than hardware-intensive alternatives like Quantum Key Distribution (QKD).
Government and enterprise security frameworks are already mandating the adoption of QRC. The U.S. National Institute of Standards and Technology (NIST) has identified and standardized several QRC algorithms for federal use, and global enterprises are aligning their cyber strategies accordingly. QRC is also the foundation for crypto-agility, allowing organizations to swiftly switch encryption methods as new standards emerge or threats evolve. This adaptability has made QRC the preferred choice across diverse sectors, including BFSI, healthcare, defense, and telecommunications. Moreover, QRC offers a cost-effective, scalable path to quantum readiness that fits into existing software stacks, making it highly attractive for CIOs and CISOs seeking compliance without a massive infrastructure overhaul. Its dominance is thus driven by urgency, practicality, regulatory pressure, and long-term resilience against both current and future cyber threats.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
By Application Analysis
Network Security is expected to represent the most dominant application in the Quantum Computing in Cybersecurity Market due to the foundational role it plays in securing digital infrastructure. As cyber threats escalate in both volume and sophistication, protecting data in transit across private, public, and hybrid networks has become a top priority. Quantum computing introduces new challenges to this arena by threatening to break the encryption methods that currently secure SSL/TLS protocols, VPNs, routers, and firewalls. Post-quantum attacks on these systems could expose everything from government communications to financial transactions, making network security the most urgent frontier for quantum-resistant innovation.
Organizations are racing to deploy quantum-safe VPNs, secure socket layers, and hybrid cryptographic models to protect traffic flowing across the internet and intranets. Quantum-resistant algorithms are being embedded into transport layers, IPsec frameworks, and virtual private network protocols to guard against the “harvest now, decrypt later” tactic increasingly used by advanced persistent threats (APTs). The rise of edge computing, IoT ecosystems, and 5G infrastructure further intensifies the need for quantum-safe network security, as more endpoints and data packets are introduced into vulnerable environments.
Additionally, governments and regulatory bodies are prioritizing network security in their post-quantum cybersecurity guidelines, with initiatives like the U.S. CISA’s “Post-Quantum Cryptography Initiative” specifically highlighting secure communication protocols. Enterprises view network protection as their first line of defense, making investment in quantum-resilient network tools non-negotiable. As the digital economy grows, ensuring that networks are future-proof against quantum decryption becomes both a regulatory necessity and a strategic imperative, solidifying network security’s dominance in this market.
By Industry Vertical Analysis
The Banking, Financial Services, and Insurance (BFSI) sector is expected to dominate the Quantum Computing in Cybersecurity Market due to its data sensitivity, high-value transactions, and stringent regulatory landscape. BFSI handles massive volumes of confidential financial data credit card numbers, transaction records, customer identities, investment portfolios that are prime targets for cybercriminals. The quantum threat poses an existential risk to the sector, as quantum computers could break classical encryption methods like RSA and ECC, which form the foundation of financial data security, digital signatures, and secure payment gateways.
Moreover, the sector’s reliance on long-term data confidentiality makes it highly vulnerable to “harvest now, decrypt later” attacks. Financial institutions are therefore among the earliest adopters of quantum-resistant cryptographic solutions and hybrid encryption models. Institutions like JPMorgan Chase, HSBC, and Mastercard are already investing in post-quantum research, quantum key distribution trials, and blockchain systems embedded with quantum-safe protocols. Simultaneously, regulatory bodies such as the U.S. SEC, FINRA, and the European Central Bank are updating compliance requirements to include quantum readiness, further compelling BFSI players to act proactively.
In addition, the rise of digital banking, decentralized finance (DeFi), and blockchain-based financial services has expanded attack surfaces. As BFSI becomes more interconnected and cloud-reliant, the need to secure network infrastructure, authentication mechanisms, and transaction logs from quantum decryption becomes paramount. High budgets, rapid digitalization, and reputational risk sensitivity make BFSI the most prepared and incentivized sector to lead quantum cybersecurity adoption. Their early investment and regulatory alignment ensure BFSI remains the dominant vertical in this rapidly evolving landscape.
The Global Quantum Computing in Cybersecurity Market Report is segmented on the basis of the following
By Solution Type
- Quantum-Resistant Cryptography Solutions
- Quantum Key Distribution (QKD) Systems
- Quantum-Powered Threat Detection Platforms
- Quantum-Secured Blockchain Solutions
By Application
- Network Security
- Cloud Security
- Database and Application Security
By Industry Vertical
- Banking, Financial Services, and Insurance (BFSI)
- Healthcare
- Government and Defense
- Information Technology and Telecommunications
Global Quantum Computing in Cybersecurity Market: Regional Analysis
Region with the Largest Revenue Share
North America is expected to dominate the Quantum Computing in Cybersecurity Market as it commands over 40.3% of the total revenue share by the end of 2025, due to its robust technological ecosystem, heavy government funding, and proactive regulatory frameworks. The United States leads global quantum research, with agencies such as the Department of Energy (DOE), National Institute of Standards and Technology (NIST), and National Security Agency (NSA) investing billions into quantum-resilient cryptographic solutions. Major tech firms headquartered in the U.S. including IBM, Google, Microsoft, and Intel are pioneering quantum algorithms, hardware, and security solutions. The presence of cybersecurity giants like Palo Alto Networks, FireEye, and CrowdStrike further accelerates the region’s integration of quantum-safe protocols across commercial and federal systems.
Additionally, the U.S. federal government’s “National Quantum Initiative Act” and NIST’s post-quantum cryptography standardization efforts are forcing early enterprise adoption of quantum-resilient technologies. The North American BFSI and defense sectors, which manage vast amounts of sensitive data, are leading the demand for quantum-secure infrastructure. Canada also plays a key role through companies like D-Wave and Xanadu and government-supported research hubs such as the Perimeter Institute. The synergy between academia, industry, and government creates a mature, innovation-driven market, securing North America’s dominance in this space.
ℹ
To learn more about this report –
Download Your Free Sample Report Here
Region with the Highest CAGR
Asia Pacific is projected to record the highest CAGR in the Quantum Computing in Cybersecurity Market due to aggressive government investments, burgeoning digital ecosystems, and increasing geopolitical emphasis on cybersecurity. China, Japan, South Korea, Singapore, and India are investing heavily in quantum R&D through national initiatives like China’s Quantum Experiments at Space Scale (QUESS) and Japan’s Quantum Leap Flagship Program. These programs emphasize cybersecurity use cases, especially for critical infrastructure, telecommunications, and national defense.
As APAC economies digitize rapidly, particularly in banking, healthcare, and telecom, there’s an urgent need to future-proof data systems against quantum threats. Countries such as Japan and South Korea are integrating quantum-resistant protocols into their national cybersecurity frameworks. Moreover, the proliferation of startups, increasing public-private partnerships, and favorable policy reforms make APAC a high-growth region. The region’s accelerated 5G rollout, smart city initiatives, and AI expansion also create fertile ground for quantum-secured networks. As infrastructure matures, APAC's CAGR reflects both urgency and long-term scalability, positioning it as a fast-emerging player in this market.
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Global Quantum Computing in Cybersecurity Market: Competitive Landscape
The Quantum Computing in Cybersecurity Market is highly competitive and characterized by a mix of established technology firms, quantum-specialized startups, and collaborative research institutions. Leading players include IBM, Microsoft, Google (Alphabet Inc.), D-Wave Systems, and Quantinuum, all of which are developing end-to-end quantum and post-quantum cryptography solutions. These companies leverage extensive R&D capabilities and partnerships with academic institutions to stay ahead in innovation.
Startups like ISARA Corporation, PQShield, QNu Labs, and QuintessenceLabs focus on niche quantum security offerings such as quantum key distribution, quantum random number generation, and post-quantum VPNs. These agile firms are frequently targeted for strategic partnerships or acquisitions by larger cybersecurity vendors. Hardware developers such as Rigetti Computing and IonQ contribute quantum processing units (QPUs) used in encryption and simulation tasks, indirectly supporting cybersecurity applications.
Companies like ID Quantique and Toshiba Corporation lead in QKD commercialization, while global consortia and standards bodies like ETSI, NIST, and IEEE influence product direction through compliance guidelines. The competitive landscape is further shaped by growing cross-industry collaboration, government-funded pilot projects, and open-source cryptographic tools. With increasing geopolitical cyber risk and regulatory mandates, vendor competition is expected to intensify, driving accelerated innovation and deployment cycles.
Some of the prominent players in the Global Quantum Computing in Cybersecurity Market are:
- IBM
- Microsoft
- Google (Alphabet Inc.)
- D-Wave Systems
- Rigetti Computing
- IonQ
- Quantinuum
- Xanadu
- Atos SE
- Toshiba Corporation
- ID Quantique
- QuintessenceLabs
- PQShield
- ISARA Corporation
- Post-Quantum
- Qrypt
- MagiQ Technologies
- QNu Labs
- Q-CTRL
- Zapata Computing
- Other Key Players
Recent Developments in Global Quantum Computing in the Cybersecurity Market
May 2025
- Nvidia’s Strategic Investment in PsiQuantum: Nvidia entered advanced talks to invest in PsiQuantum, which is raising at least $750 million at a $6 billion pre-money valuation. This reinforces Nvidia’s quantum push, including its new quantum research lab in Boston in collaboration with MIT and Harvard.
- KETS Quantum Security Prototype Deployment: KETS Quantum Security, a UK-based startup, initiated prototype testing of its silicon photonics-based quantum encryption system with BT. The chip transmits quantum-encrypted keys and instantly detects interception, aligning with the EuroQCI initiative to deploy quantum-secure networks across Europe.
April 2025
- Cloudflare’s Quantum-Resistant Infrastructure Rollout: Cloudflare embedded post-quantum cryptographic algorithms into its Zero Trust Network Access service. By mid-2025, it aims to secure all IP protocols, preparing for the quantum threat to classical encryption.
- Big Tech Milestones in Quantum: Tech giants, including IBM, Google, Microsoft, Amazon, and Nvidia, revealed roadmap expansions. IBM plans a 4,000+ qubit quantum-centric supercomputer, while Google is refining quantum error correction. These advancements are amplifying the demand for quantum-specific cybersecurity defenses.
March 2025
- Quantum Innovation Summit, Dubai: The event attracted 800+ attendees, including global tech leaders and policymakers. Key launches included VerneX Quantum Valley, a partnership between ID Quantique and Abu Dhabi Maritime Academy, and a strategic alliance between Kipu Quantum and NYU Abu Dhabi.
- Nvidia’s Quantum Day Announcements at GTC: Nvidia hosted its first Quantum Day, announcing new hardware for hybrid quantum-classical computing and launching a dedicated quantum lab in Boston. Collaborations with D-Wave, Infleqtion, and SEEQC focused on secure blockchain, contextual AI, and cryogenic integration.
February 2025
- Quantinuum Launches Generative Quantum AI: Quantinuum introduced a new framework enabling synthetic data generation for use in healthcare diagnostics, finance simulations, and logistics. It announced new European partnerships, including integration pilots with the HPE Group in Italy.
January 2025
- Maryland’s “Capital of Quantum” Plan: Governor Wes Moore unveiled a $27.5 million state-funded initiative to build Maryland into a global quantum hub. The plan includes attracting private investment, launching educational initiatives, and expanding quantum R&D across public institutions.
- SEEQC Secures $30 Million: Quantum computing company SEEQC closed a $30 million funding round led by NordicNinja and Booz Allen Ventures. The funds support the commercialization of its integrated quantum platform, optimized for cybersecurity and post-quantum cryptographic simulations.
- Microsoft's Quantum Ready Program: Microsoft launched a program to help enterprises assess quantum risks and develop post-quantum transition strategies. The initiative also provides training and tooling to begin prototyping quantum-safe systems in current IT environments.
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 1,995.3 Mn |
| Forecast Value (2034) |
USD 24,231.0 Mn |
| CAGR (2025–2034) |
32.0% |
| Historical Data |
2019 – 2024 |
| The US Market Size (2025) |
USD 676.3 Mn |
| Forecast Data |
2025 – 2033 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors, etc. |
| Segments Covered |
By Solution Type (Quantum-Resistant Cryptography Solutions, Quantum Key Distribution (QKD) Systems, Quantum-Powered Threat Detection Platforms, Quantum-Secured Blockchain Solutions), By Application (Network Security, Cloud Security, Database and Application Security) By Industry Vertical (Banking, Financial Services, and Insurance (BFSI), Healthcare, Government and Defense, Information Technology and Telecommunications) |
| Regional Coverage |
North America – US, Canada;
Europe – Germany, UK, France, Russia, Spain, Italy, Benelux, Nordic, Rest of Europe;
Asia-Pacific – China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC;
Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America;
Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, Rest of MEA
|
| Prominent Players |
IBM, Microsoft, Google (Alphabet Inc.), D-Wave Systems, Rigetti Computing, IonQ, Quantinuum, Xanadu, Atos SE, Toshiba Corporation, ID Quantique, QuintessenceLabs, PQShield, ISARA Corporation, Post-Quantum, Qrypt, MagiQ Technologies, QNu Labs, Q-CTRL, Zapata Computing., and Other Key Players |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user),
Multi-User License (Up to 5 Users), and
Corporate Use License (Unlimited User) along with free report customization equivalent to
0 analyst working days, 3 analysts working days, and 5 analysts working days respectively.
|
Frequently Asked Questions
How big is the Global Quantum Computing in Cybersecurity Market?
▾ The Global Quantum Computing in Cybersecurity Market size is estimated to have a value of USD 1,995.3 million in 2025 and is expected to reach USD 24,231.0 million by the end of 2034.
What is the size of the US Quantum Computing in Cybersecurity Market?
▾ The US Quantum Computing in Cybersecurity Market is projected to be valued at USD 676.3 million in 2025. It is expected to witness subsequent growth in the upcoming period as it holds USD 7,156.8 million in 2034 at a CAGR of 30.0%.
Which region accounted for the largest Global Quantum Computing in Cybersecurity Market?
▾ North America is expected to have the largest market share in the Global Quantum Computing in Cybersecurity Market with a share of about 40.3% in 2025.
Who are the key players in the Global Quantum Computing in Cybersecurity Market?
▾ Some of the major key players in the Global Quantum Computing in Cybersecurity Market are IBM, Microsoft, Google (Alphabet Inc.), D-Wave Systems, Rigetti Computing, IonQ, Quantinuum, Xanadu, Atos SE, Toshiba Corporation, ID Quantique, QuintessenceLabs, and many others.
What is the growth rate of the Global Quantum Computing in Cybersecurity Market in 2025?
▾ The market is growing at a CAGR of 32.0 percent over the forecasted period of 2025.