Market Overview
The Global Cybersecurity Mesh Market is expected to reach a value of USD 2.9 billion in 2025, and it is further anticipated to reach a market value of USD 33.7 billion by 2034 at a CAGR of 30.2%. The market has seen significant growth over the past few years and is predicted to grow significantly during the forecasted period as well.
Cybersecurity mesh provides a distinct approach to cyber defense, securing each device with its own set of perimeters, including firewalls & network protection tools, different from traditional security practices that are established on a single perimeter, cybersecurity mesh holds a comprehensive strategy.
Further, the rise in this strategy corresponds to the increasing importance of remote work & cloud solutions, distributing devices across diverse locations. This shift requires updates to data access 7 control policies, accompanied by the integration of cutting-edge technologies.
Cybersecurity mesh offers not only functional advantages for institutions but also strategic advantages. Identity and Access Management (IAM) services should support over 50% of Identity and Access Management requests, improving delivery while increasing demand for Managed Security Service Providers (MSSPs).
Cybersecurity mesh, consisting of composable security and identity services, offers many advantages such as responsive security, improved collaboration, flexibility, scalability and redefined cybersecurity parameters. As is often the case, cybersecurity mesh presents unique challenges when applied to existing ecosystems, including its complexity and high costs. Ensuring secure identity-based systems along with appropriate training and support services for optimal functioning is vital for its effective operation.
According to the Fortinet 2022 Cybersecurity Skills Gap Global Research Report, 80% of organizations worldwide experienced cyberattacks due to an insufficient supply of qualified cybersecurity professionals. One of the primary difficulties organizations experience in hiring and retaining cybersecurity talent; 67% believe a lack of skilled professionals increases their risk of cyberattacks.
Cyber threats exploit network vulnerabilities to penetrate enterprise systems. With the rise of sophisticated cyberattacks such as zero-day threats, organizations require robust security measures. Cybersecurity mesh solutions play an integral role in detecting and mitigating these threats; however, due to low awareness of advanced cyber threats many organizations fail to invest enough in cybersecurity training programs. Emerging sectors like the
AI in Cybersecurity are responding by integrating intelligent automation into threat detection and incident response.
Demand for qualified cybersecurity professionals has never been higher, with 76% of organizations reporting their boards of directors have recommended expanding IT and cybersecurity teams. A report identified Cloud Security Specialists and Security Operations Analysts as two in-demand roles followed by Security Administrators/Architects; instead of hiring randomly, organizations are now strategically creating teams capable of managing an increasingly complex cyber landscape.
Key Takeaways
- Market Size & Share: Cybersecurity Mesh Market is expected to reach a value of USD 2.9 billion in 2025, and it is further anticipated to reach a market value of USD 33.7 billion by 2034 at a CAGR of 30.2%.
- In 2024, cybersecurity mesh solutions dominate with a 73.2% market share, driven by integration with AI, ML, and edge computing technologies.
- Cloud-based models significantly contribute to market revenue due to their scalability, flexibility, and cost-efficiency, making them highly attractive for businesses.
- Large-scale organizations' data systems hold a 64.2% market share, emphasizing their increased need for robust cybersecurity frameworks.
- The IT & telecom sector is a major revenue contributor, leveraging cloud and virtualization for better efficiency and security responsiveness.
- In 2024, the North American region secures a substantial market share, accounting for about 39.7%
Use Cases
- Decentralized Identity & Access Management (IAM): Provides secure and adaptive identity verification across distributed environments, reducing the risk of unauthorized access.
- Zero Trust Security Framework: Ensures continuous verification of users, devices, and applications, preventing lateral movement of cyber threats within networks.
- Cloud Security & Hybrid IT Protection: Protects multi-cloud and hybrid IT infrastructures by applying security policies consistently across different environments.
- Threat Intelligence & Automated Response: Uses AI-driven analytics to detect, analyze, and respond to cyber threats in real-time, minimizing damage from attacks.
- Secure Remote Workforce & Endpoint Protection: Extends security controls to remote employees and endpoints, reducing exposure to phishing, ransomware, and insider threats.
Market Dynamic
The Cybersecurity Mesh Architecture (CSMA) provides a scalable & modular solution for growing security controls across widely dispersed assets. This adaptable approach is mainly well-suited for hybrid multi-cloud systems & modular strategies. CSMA allows for seamless communication among technologies through many layers, including security intelligence, centralized policy management, & identity fabric, removing isolated security tool silos. These advantages are projected to fuel future market demand.
Moreover, CSMA facilitates secure communication around diverse locations, channels, app generations, and hybrid & multi-cloud environments for both people & machines. This allows comprehensive protection for the organization's digital assets while strengthening a consistent security posture to improve business agility. CSMA provides services such as security analytics, distributed identity fabric, intelligence, automation, triggers, & centralized policy administration to make seamless integration possible for security solutions.
Driving Factors
Cyberattacks of increasing frequency and sophistication are driving the expansion of the cybersecurity mesh market. Organizations now face complex and varied threats such as ransomware to data breaches that necessitate decentralized security architectures for protection.
Cybersecurity mesh solutions enable businesses to enforce consistent security policies across cloud, hybrid, on premises systems while still protecting data, devices, users from malicious attacks.
With rising threats becoming ever more sophisticated as well as increased demand for comprehensive protection solutions such as these mesh solutions growing, companies need comprehensive protection solutions like this to provide comprehensive protection from ransomware attacks as ransomware attacks increase.
Trending Factors
One of the primary trends in cybersecurity mesh market is artificial intelligence (AI) and automation integration. AI technologies enable cybersecurity mesh solutions to detect and respond quickly to security incidents in real time, improving threat detection while decreasing response times.
Machine learning algorithms can analyze vast amounts of network data faster and more accurately than human teams can, quickly detecting vulnerabilities or potential threats quicker and enhancing efficiency with automation reducing manual intervention while increasing overall efficiency something AI and automation play an integral part in doing. As AI and automation continue their advancement into newer capabilities for cybersecurity mesh capabilities
Restraining Factors
A key barrier in the cybersecurity mesh market is its complexity of implementation, as organizations may face difficulty integrating cybersecurity mesh solutions with their current IT infrastructures particularly legacy ones. Decentralized mesh architectures demand careful coordination among different security layers and tools, which may be challenging for businesses with limited resources or expertise.
Complexities associated with managing distributed security policies across multiple environments can present additional implementation hurdles that delay adoption of cybersecurity mesh solutions by smaller organizations on limited budgets.
Opportunity
The increasing adoption of hybrid IT environments represents an exciting new market for cybersecurity mesh vendors. When organizations switch to hybrid cloud setups that combine on premises infrastructure with cloud services, they face unique security issues that must be managed. Cybersecurity mesh offers an ideal way of protecting decentralized environments by offering a centralized security framework that encompasses both cloud based and on premises systems.
As hybrid environments become more widespread, organizations require flexible, scalable and decentralized security solutions to protect their data and networks. This presents cybersecurity mesh providers with an attractive market opportunity by providing tailored solutions tailored to the specific requirements of hybrid IT infrastructures. This is particularly evident in sectors such as the
Healthcare Cybersecurity, where a growing number of connected health devices and compliance mandates necessitate specialized, adaptive security strategies.
Research Scope and Analysis
By Component
In 2024, the solutions for the cybersecurity mesh lead the market with a 73.2% Market share, primarily driven by the growth of cybersecurity mesh solutions, fueled by technologies such as edge computing,
machine learning (ML), &
artificial intelligence (AI). These technologies strengthen security by allowing smart threat detection, behavior analysis, & automated responses at the edge.
In a landscape marked by strict data security & privacy regulations, cybersecurity mesh solutions provide a strategic advantage. They empower organizations to sustain compliance effectively by applying security controls at the device level. This critical aspect is expected to fuel a growing demand for cybersecurity mesh solutions across various industries during the forecasted period.
By Deployment
In 2024, cloud deployment plays a major role in the market as it contributes significantly to the global overall revenue of cybersecurity mesh, driven by the captivation of cloud computing's scalability, flexibility, & cost-efficiency for businesses.
As companies exponentially adopt cloud solutions, making sure of strong security becomes important, mainly with critical operations & data moving to the cloud. By utilizing a cybersecurity mesh in the cloud, organizations can secure their cloud environments in a distributed & scalable manner, ensuring consistent application of security measures across all cloud resources.
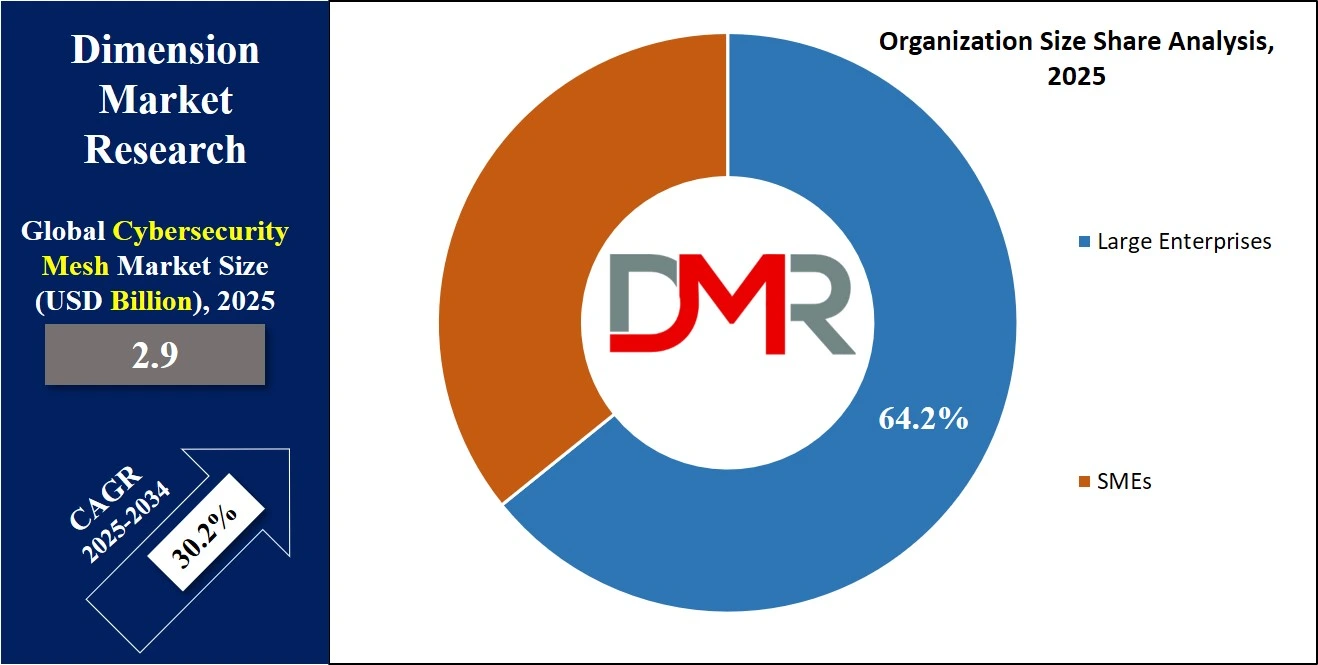
By Organization Size
In 2024, the cybersecurity Mesh market is largely dominated by the large enterprise segment with a 64.2% market share, reflecting their substantial data & resource holdings that make them appealing targets for cyberattacks. In addition to the growing difficulties & complexities of cyber threats, large businesses are made to adopt advanced security protocols. Cybersecurity mesh solutions provide a strong defense strategy by implementing security controls at the device level, allowing real-time threat detection, swift response, & containment actions.
Also, Small and Medium-sized Enterprises (SMEs) are not excluded from the threat of cyber-attacks, often targeted due to comparatively weaker security infrastructure compared to their larger counterparts. Recognizing the increasing frequency & complexity of cyber threats, including ransomware, phishing, & data breaches, SMEs are progressively realizing the importance of strong cybersecurity measures.
By End User Industry
The IT & telecom sector has emerged as a major driver of the cybersecurity Mesh market in 2024, as it contributes significantly towards the overall market revenue. The sector has quickly adapted to cloud computing & virtualization technologies, as seen by the benefits of enhanced agility, scalability, & cost-efficiency. However, these technologies bring about specific security challenges, surrounding data privacy, multi-tenancy, & vulnerabilities in virtual machine environments.
To address these issues, cybersecurity mesh solutions provide a unified security framework customized for the IT & Telecom sectors. This complete approach spans across virtualized infrastructure & cloud landscapes while making sure consistent application of security controls & policies to secure critical data & applications.
This trend is set to increase the demand for cybersecurity mesh solutions across the IT & telecom sector, as organizations look to strengthen their security position while taking advantage of cloud & virtualization technologies.
The Global Cybersecurity Mesh Market Report is segmented based on the following
By Component
By Deployment
By Organization Size
By End User Industry
- BFSI
- IT & Telecom
- Healthcare
- Government
- Others
How Does Artificial Intelligence Contribute To Improve Cybersecurity Mesh Market ?
- AI-driven Threat Detection & Prevention: AI continuously monitors network traffic and user behavior to identify anomalies and potential cyber threats before they escalate.
- Automated Incident Response: AI-powered security systems automate threat mitigation, reducing response time and minimizing the impact of cyberattacks.
- Predictive Security Analytics: AI leverages machine learning models to predict emerging cyber threats based on historical attack patterns, allowing proactive security measures.
- Zero Trust Security Enhancement: AI enables real-time identity verification, continuously assessing risk levels and enforcing security policies in a dynamic, decentralized environment.
- Adaptive Authentication & Access Control: AI enhances multi-factor authentication (MFA) by analyzing contextual data (e.g., user behavior, device trust level) to grant or restrict access dynamically.
Regional Analysis
In 2024, the North American region secures a substantial market share, accounting for
about 39.7% of the total revenue for the global Cybersecurity Mesh Market, as the cyber threat landscape in North America remains complex and dynamic, marked by a growth in cyberattacks targeting critical infrastructure, businesses, governmental bodies, & individuals through online channels.
The need for strong cybersecurity measures has intensified to protect sensitive data, essential systems, & critical infrastructure. In addition, major data breaches have emerged as a major concern, impacting both corporations & individuals in high-profile incidents. The exposure of private data ruins trust & raises privacy concerns. Addressing these challenges, cybersecurity mesh solutions use strict security controls & advanced encryption methods and will be seeing significant growth in the coming future as well.
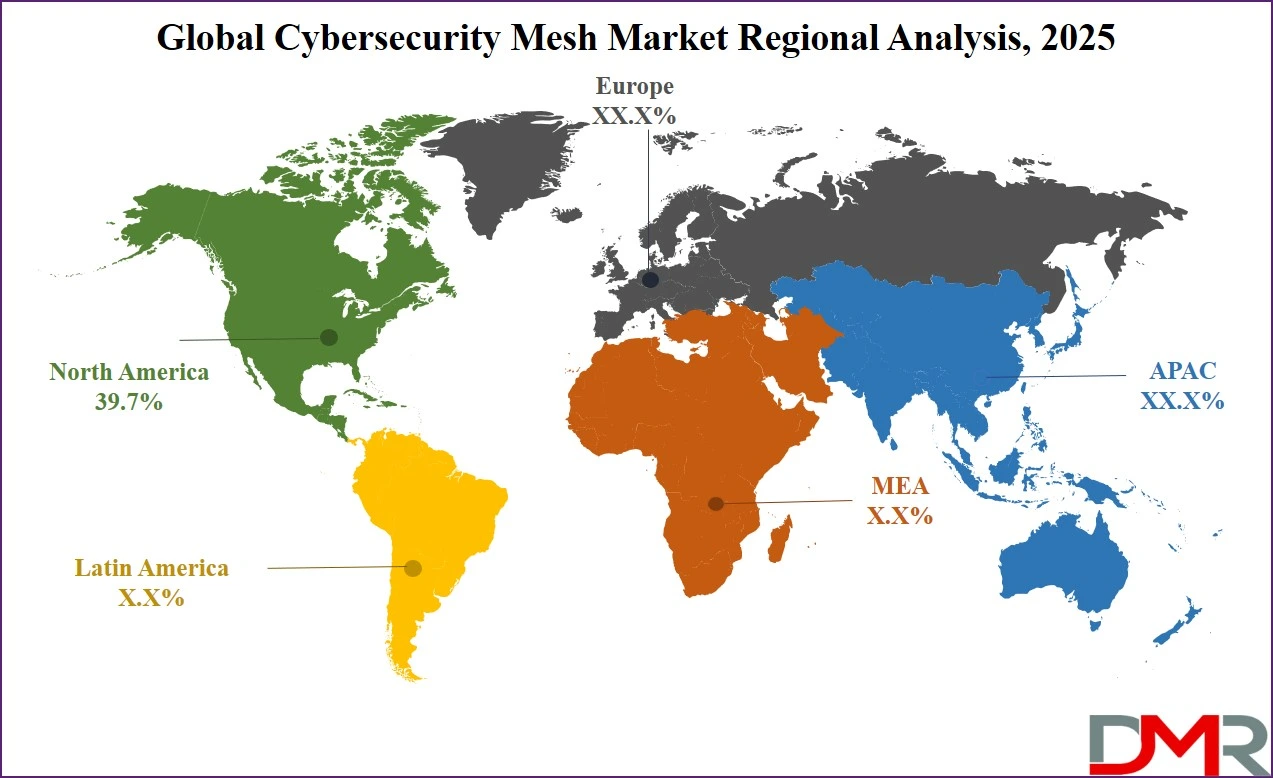
By Region
North America
Europe
- Germany
- The U.K.
- France
- Italy
- Russia
- Spain
- Benelux
- Nordic
- Rest of Europe
Asia-Pacific
- China
- Japan
- South Korea
- India
- ANZ
- ASEAN
- Rest of Asia-Pacific
Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Rest of Latin America
Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Israel
- Egypt
- Rest of MEA
Competitive Landscape
The competitive landscape of the global Cybersecurity Mesh market shows intense competitiveness among key players looking to establish their market presence & capitalize on the growing demand for advanced security solutions.
In addition, well-established cybersecurity firms, along with emerging technology providers, are constantly competing by providing innovative cybersecurity mesh solutions that look to the evolving threat landscape. Mainly, partnerships, collaborations, & strategic acquisitions are driving consolidation in the market, allowing companies to improve their product offerings & expand their customer base.
As the need for strong & adaptable security measures increases, competition in the Cybersecurity Mesh market is anticipated to remain intense, commanding to the ongoing advancements & increasing innovations across the industry.
For instance, in June 2024, Eviden, a subsidiary of Atos, introduced AIsaac Cyber Mesh, a cutting-edge cybersecurity detection & response solution, supported by the capabilities of Amazon Web Services (AWS) Security Data Lake & driven by generative AI advancements. In addition, it provides an innovative end-to-end approach for detection, response, & recovery, structured upon a cybersecurity mesh-enabled architecture. This architecture uses the potential of generative AI & predictive analytics to provide better solutions.
Some of the prominent players in the Global Cybersecurity Mesh Market are
Recent Developments
- In December 2024, Tuskira emerged from stealth with a $28.5 million funding round to unveil its AI-powered unified threat defense platform, aimed at redefining enterprise cybersecurity through automation and real-time threat response.
- In April 2025, Kenzo Security raised $4.5 million to develop its Agentic AI Security Operations Platform, focusing on enhancing cyber defense through autonomous, intelligent threat detection and mitigation.
- In March 2025, Sola Security came out of stealth with $30 million in funding to empower organizations with tools to create custom cybersecurity applications, offering greater control and flexibility in defending against evolving digital threats.
- In March 2025, Mesh secured $82 million in a Series B round to advance its global crypto payments network, aiming to simplify and secure digital transactions across borders with scalable blockchain infrastructure.
Report Details
| Report Characteristics |
| Market Size (2025) |
USD 2.9 Bn |
| Forecast Value (2034) |
USD 33.7 Bn |
| CAGR (2025-2034) |
30.2% |
| Historical Data |
2019 - 2024 |
| Forecast Data |
2025 - 2034 |
| Base Year |
2024 |
| Estimate Year |
2025 |
| Report Coverage |
Market Revenue Estimation, Market Dynamics, Competitive Landscape, Growth Factors and etc. |
| Segments Covered |
By Component (Solutions and Services), By Deployment (Cloud and On-Premises), By Size (SMEs and Large Enterprises), By End User Industry (BFSI, IT & Telecom, Healthcare, Government, and Others) |
| Regional Coverage |
North America – The US and Canada; Europe – Germany, The UK, France, Russia, Spain, Italy, Benelux, Nordic, & Rest of Europe; Asia- Pacific– China, Japan, South Korea, India, ANZ, ASEAN, Rest of APAC; Latin America – Brazil, Mexico, Argentina, Colombia, Rest of Latin America; Middle East & Africa – Saudi Arabia, UAE, South Africa, Turkey, Egypt, Israel, & Rest of MEA |
| Prominent Players |
Fortinet Inc., Cisco System, Forcepoint, BAE Systems Inc., Exium, IBM Corp., Oracle, Mesh Security Ltd, Naoris Protocol, Eviden, and Other Key Players |
| Purchase Options |
We have three licenses to opt for: Single User License (Limited to 1 user), Multi-User License (Up to 5 Users), and Corporate Use License (Unlimited User) along with free report customization equivalent to 0 analyst working days, 3 analysts working days and 5 analysts working days respectively. |
Frequently Asked Questions
The Global Cybersecurity Mesh Market size is estimated to have a value of USD 1.7 billion in 2023 and is expected to reach USD 18.4 billion by the end of 2032.
North America has the largest market share for the Global Cybersecurity Mesh Market with a share of about 39.7% in 2023.
Some of the major key players in the Global Cybersecurity Mesh Market are IBM Corp, Oracle, Cisco System, and many others.
The market is growing at a CAGR of 30.2 percent over the forecasted period.